As cyber threats become more advanced, choosing the right cryptographic algorithm is essential to keep data secure. SHA256 stands out among other options because it offers strong protection against vulnerabilities and aligns with top industry standards. In this article, we’ll dive into why Protectimus endorses SHA256 and how this algorithm supports the security of our 2FA solutions.
1. Understanding TOTP Tokens and Hashing Algorithms
TOTP tokens serve as an additional layer of protection, providing a unique and time-sensitive password for each login attempt. TOTP, or Time-Based One-Time Password, is a mechanism that generates one-time passwords valid for a short period – 30 or 60 seconds. The process of generating TOTP passcodes involves the utilization of a hashing algorithm, such as SHA-1 or SHA-256, to convert a shared secret and the current time into a unique one-time password. This shared secret is typically known to both the server and the user’s device, ensuring that both parties can independently generate the same OTP at any given moment.
The time-based element is crucial to the security of TOTP tokens. Both the server and the user’s device must be in sync regarding time. The OTP is valid only for a short window of time, usually 30 seconds, after which it becomes invalid and useless for any future login attempts. This time factor introduces an additional level of complexity for potential attackers trying to predict or brute-force the correct OTP.
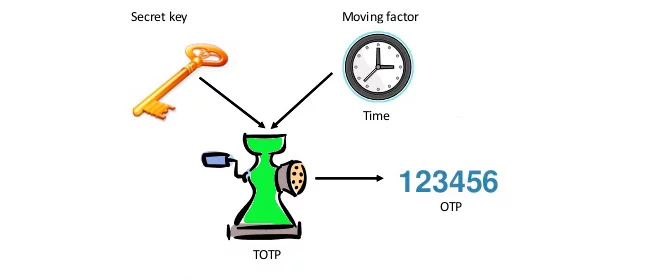
To fully grasp how TOTP tokens work, it’s essential to delve into the underlying hashing algorithms SHA-1 and SHA-256. But what is a hash?
What Is Hash?
A hash function takes an input (or ‘message’) and converts it into a fixed-length string of characters, typically a sequence of numbers and letters. This output is commonly referred to as the hash value or hash code. The critical characteristic of a hashing algorithm is that it is a one-way process, meaning that it is computationally infeasible to reverse-engineer the original input from the hash value. This property ensures that sensitive data, such as passwords and TOTP secrets, remains well protected.
It’s important to understand the difference between encryption and hashing. While encryption involves transforming data into ciphertext that can be reversed using a specific key, hashing irreversibly transforms data into a fixed-size string of characters (hash). Hash functions like SHA-1 and SHA-256 generate unique hash values that are practically impossible to reverse-engineer, ensuring the security of TOTP tokens.
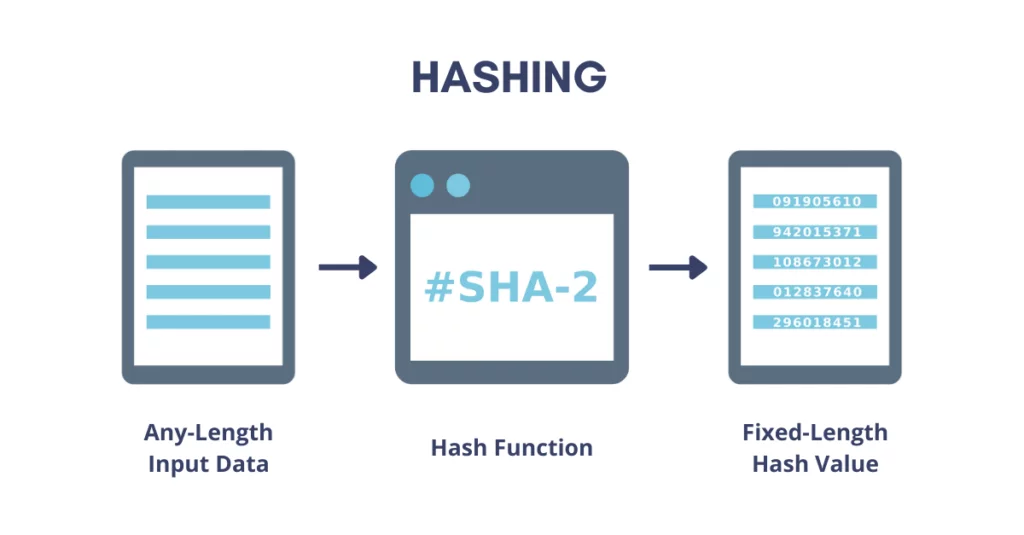
The importance of secure TOTP token generation cannot be overstated. It safeguards sensitive information, strengthens authentication mechanisms, and bolsters the overall security posture of systems implementing 2FA. By adopting robust hashing algorithms like SHA-256, organizations can enhance their defenses against potential threats, providing users with a more secure and reliable authentication experience.
2. Vulnerabilities and Risks of SHA-1 in TOTP Token Systems
SHA1, once considered a secure hashing algorithm, has been found to possess several vulnerabilities when used in TOTP token systems. These weaknesses can pose certain security risks, compromising the integrity of the one-time passwords and making systems more susceptible to attacks. However, transitioning to the more advanced SHA-256 algorithm can address these issues and enhance the overall security of TOTP token systems.
Collision Vulnerabilities
One of the primary vulnerabilities of SHA-1 is its susceptibility to collision attacks. This means that different inputs can produce the same hash value, potentially allowing attackers to create valid one-time passwords for unauthorized access.
Weakening Security
SHA-1’s weakening security over time is a concern in the rapidly evolving threat landscape. As computing power and cryptanalysis techniques advance, SHA-1 becomes more vulnerable to exploitation.
Reduced Trust
The industry’s recognition of SHA-1’s vulnerabilities has led to its deprecation and the recommendation to adopt stronger hashing algorithms, such as SHA-256. Continuing to use SHA-1 in TOTP token systems may lead to compliance issues and a loss of trust from users and stakeholders, as its security weaknesses become more widely known.
To address these vulnerabilities and risks, it is crucial for organizations to transition from SHA-1 to more secure hashing algorithms like SHA-256. Upgrading to stronger cryptographic primitives enhances the security and reliability of TOTP token systems, providing better protection against potential threats and ensuring the integrity of sensitive data.
| Read also: OCRA Algorithm Explained
3. Advantages of SHA-256 for TOTP Token Generation
SHA-256, a member of the SHA-2 (Secure Hash Algorithm 2) family, has gained prominence for its enhanced security features over its predecessor, SHA-1. SHA-256 offers several advantages that make it a superior choice for generating TOTP tokens.
SHA-256 Has Larger Hash Size
First and foremost, SHA-256 provides a significantly larger hash size compared to SHA-1, offering a stronger cryptographic foundation. While SHA-1 produces a 160-bit hash value, SHA-256 generates a much larger 256-bit hash value. This increased hash size expands the potential hash space, making it exponentially more difficult for attackers to guess or reverse-engineer the original input based on the output hash.
Resistance Against Collision Attacks
Another advantage lies in the resistance of SHA-256 against collision attacks. Collision attacks occur when two different inputs produce the same hash output, potentially leading to security vulnerabilities. SHA-1, unfortunately, has known weaknesses in this regard, whereas SHA-256 has been designed to be highly resistant to collision attacks, providing a higher level of data integrity and security for TOTP tokens.
SHA-256 Aligns With Industry Best Practices and Security Standards
Moreover, the adoption of SHA-256 for TOTP token generation aligns with industry best practices and security standards. It is widely recognized as a more secure alternative and is recommended by organizations such as the National Institute of Standards and Technology (NIST) for cryptographic operations. By embracing SHA-256, organizations can enhance the overall security posture of their TOTP token solutions and mitigate potential risks associated with continued use of SHA-1.
In conclusion, the robustness and security features offered by SHA-256 make it an advantageous choice for generating TOTP tokens. Its larger hash size, resistance to collision attacks, and alignment with industry standards contribute to the overall integrity and protection of TOTP-based authentication systems. By transitioning from SHA-1 to SHA-256, organizations can strengthen their TOTP token security and stay ahead in the ever-evolving landscape of cybersecurity threats.
| Read also: Authenticator App Protectimus SMART Updated – Now With Encrypted Cloud Backup
4. Future-proofing TOTP Tokens Protectimus SHARK: Embracing SHA-256
Understanding the significance of the SHA-256 algorithm for bolstering one-time password security, we are thrilled to introduce the latest addition to our Protectimus token collection: the Protectimus SHARK hardware token, designed to support SHA-256.
Compact and non-programmable, the Protectimus SHARK is a classic TOTP security token that easily fits on a keychain. Utilizing the TOTP OATH standard and fortified by SHA-256, this MFA token generates time-based one-time passwords with enhanced security.

Whether you prefer the convenience of our Protectimus Cloud Service or the flexibility of the On-Premise Platform, the Protectimus SHARK effortlessly integrates with any 2FA service that supports SHA256 TOTP tokens.
With support for TOTP and SHA-256 algorithms, compliance with OATH standards, and 32-character long secret keys (Base32), the Protectimus SHARK TOTP hardware token guarantees your data’s safety. Compact, yet sturdy, it measures 28.62mm х 61.62mm х 8.9mm and weighs a mere 16.1 g. Equipped with an LED display featuring 6 digits and a time indicator, it boasts dust and water resistance (IP67). Additionally, for bulk orders of 1000 pieces, customization with branding is available, and each token comes with a reassuring 12-month warranty. The battery charge indicator ensures the token’s battery will last a remarkable 3-5 years.
In conclusion, the Protectimus SHARK TOTP hardware token stands as the epitome of security and reliability for one-time password generation, all thanks to its robust support for the SHA-256 algorithm. With its user-friendly design, exceptional durability, and adherence to industry standards, the Protectimus SHARK is the perfect choice for meeting your two-factor authentication needs.
| Read also: Protectimus SHARK: A TOTP Token Empowered by SHA-256 Algorithm
5. Conclusion
In conclusion, the advantages of SHA-256 over SHA-1 for TOTP token security are evident, highlighting the importance of choosing the right hash algorithm for robust two-factor authentication. SHA-256’s larger hash size and resistance to collision attacks provide a stronger cryptographic foundation, making it exponentially more difficult for attackers to compromise sensitive data. Additionally, SHA-256 aligns with industry best practices and security standards, ensuring the integrity and protection of TOTP-based authentication systems.
The vulnerabilities and risks associated with SHA-1 in TOTP token systems emphasize the need for organizations to transition to more secure hashing algorithms like SHA-256 or SHA-512. Upgrading to SHA-256 enhances the overall security and reliability of TOTP tokens, guarding against potential threats and maintaining user trust and compliance.
The Protectimus SHARK hardware token further exemplifies the commitment to security with its support for SHA-256. By adopting the Protectimus SHARK, organizations can future-proof their TOTP token systems and ensure a highly secure and user-friendly two-factor authentication experience.
In the dynamic landscape of cybersecurity threats, choosing SHA-256 TOTP hardware token is a strategic decision to bolster the defenses of your organization. Embracing the superiority of SHA-256 ensures that your TOTP token system remains robust, resilient, and aligned with the latest security standards for years to come.
6. Read More
- Protectimus MFA Prices: How to Save with Coupons, Discounts, Referrals, and Subscriptions
- 5 Steps to Prepare your Business for Multifactor Authentication
- Google Authenticator vs Protectimus SMART: Which Authenticator App with Cloud Backup is Best for Your Security Needs
- Protectimus Customer Stories: 2FA for DXC Technology
- Protectimus Customer Stories: 2FA for Advcash
- Protectimus Customer Stories: 2FA for SICIM
Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from our team.

Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from Protectimus blog.
You have successfully subscribed!