The first programmable TOTP tokens Protectimus Slim NFC were released just a couple years ago. Since then, we’ve received hundreds of orders, as well as hundreds of questions about how it works, how programmable security key differs from the classic one, how to program tokens, and whether or not using this kind of OTP token is secure.
In this article, I’ll explain how classic TOTP hardware token and programmable TOTP token work, show you how to program the Protectimus Slim NFC OTP token, and answer all the other common questions we get.
A table of contents for your convenience:
- How do TOTP tokens work?
- How does the authentication server verify one-time passwords?
- How are classic TOTP tokens different from programmable ones?
- Why are reprogrammable TOTP tokens better than the rest?
- How can I tell whether the Protectimus Slim NFC token is compatible with a service?
- How do I program the Protectimus Slim NFC token?
- Frequently asked questions
How do TOTP tokens work?
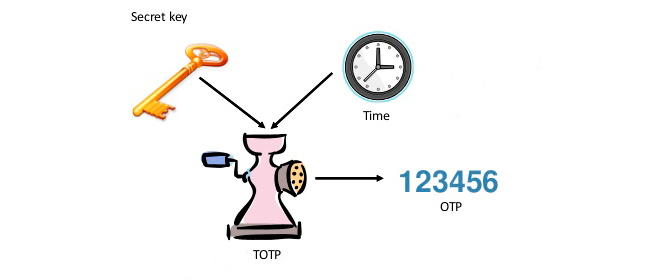
TOTP meaning is time-based one-time password. Correspondingly, there are two parameters used to generate one-time passwords using the TOTP algorithm:
- The shared secret. A unique code, generally 16-32 Base32 characters long.
- The current time interval (usually 30 or 60 seconds). Time intervals are counted from the beginning of UNIX time (which starts at the midnight between December 31, 1969 and January 1, 1970, UTC time). That means that for a TOTP device supporting 30-second intervals, the number of seconds that have passed since midnight on January 1, 1970 is divided by 30. The resulting number is used for generating a one-time password.
The OTP device processes these two values according to the TOTP algorithm (RFC 6238). The result is hashed, and the hash is truncated, leaving only the last 6 (sometimes 8) digits. The result is shown on the token’s display. In this way, we receive a time-based one-time password.
How does the authentication server verify one-time passwords?
For the two-factor authentication server to be able to verify one-time passwords and allow or deny access to accounts, it needs the same information — the same time interval and shared secret.
- Time interval. Every server has a clock, which means it also has the ability to calculate the current time interval.
- Shared secret. There are two options here:
- The administrator can upload a CSV file to the server containing predetermined shared secrets (this is how classic tokens with hard-coded secrets are connected), or
- The shared secrets can be generated by the server (this is how one-time password generator apps, like Protectimus Smart and Google Authenticator, are connected, as well as programmable hardware TOTP tokens).
This brings us to an explanation of the differences between classic and programmable hardware tokens.
| Classic TOTP tokens | Programmable TOTP tokens |
|---|---|
| Classic hardware 2FA tokens come from the factory with a hard-coded secret key that can’t be changed. | Programmable OTP hardware tokens don’t come with a secret key. The user can add one to the token after obtaining it from an authentication server, as when using a smartphone app for authentication. |
How are classic TOTP tokens different from programmable ones?
Classic TOTP tokens
Classic TOTP hardware tokens (Protectimus Two) are OTP tokens with predefined secret keys. To use classic OATH TOTP tokens, customers need the ability to upload the shared secrets to the server.
If a customer plans on using classic 2FA security keys with a third-party two-factor authentication service (such as Azure MFA or Sophos XG), we can transmit the shared secrets to them in an encrypted form.
If they will be using classic OTP tokens with the Protectimus cloud service, we can add the shared secrets to the Protectimus two-factor authentication server directly, as it is more secure and convenient.

Programmable TOTP tokens
Programmable TOTP hardware token (Protectimus Slim NFC) is an excellent solution if you don’t have access to the authentication server to upload a CSV file containing shared secrets.
To program the shared secret, you use an Android smartphone that supports NFC technology, with the Protectimus TOTP Burner app installed. The server generates a QR code containing the shared secret and asks the user to scan it using a 2FA app. However, instead of using a standard authentication app, the owner of the Protectimus Slim NFC token scans the secret using the Protectimus TOTP Burner app to transmit it to the token over NFC.
Programmable oath TOTP hardware token is suited for both enterprise (Office 365, Keycloak, Mailchimp) and private use (PayPal, Dropbox, Facebook, Coinbase, etc.).

Why are reprogrammable TOTP tokens better than the rest?
The main benefit of programmable OTP token is its universal nature. Programmable token generator can be used just like a classic TOTP hardware device, or to replace a one-time password generator app.
It’s worth noting that when you receive a Protectimus Slim NFC TOTP token, it comes with a preset secret key, just like a classic token. We can provide these keys upon request.
Another major advantage of the Protectimus Slim NFC programmable TOTP token is that its clock is synchronized each time the shared secret is programmed.
The Protectimus Slim NFC security key can be reprogrammed an unlimited number of times. Note, however, that each token can only hold one secret key at a time (it is NOT a multi-token). Each time the token is programmed, the previous shared secret is deleted and replaced with the new one.
| SMS | 2FA app | Classic token | Programmable token | |
| Cellular network connection not necessary | no | yes | yes | yes |
| OTP cannot be intercepted during delivery | no | yes | yes | yes |
| Token cannot be compromised by SIM card forgery | no | yes | yes | yes |
| Internet not required | yes | yes | yes | yes |
| Not vulnerable to virus infections | no | no | yes | yes |
| Token availability independent of phone battery life | no | no | yes | yes |
| Time synchronization feature available | yes | yes | no | yes |
| Token available free of charge for individual users and businesses alike | no | yes | no | no |
| No end-user action required for issuing | yes | no1 | no2 | no2 |
- ↑The user must install an in-app TOTP generator and issue a token linked to a specific resource.
- ↑Hardware tokens must be distributed to users in some manner (sent by mail, or delivered in person by hand). Users must also link their tokens to their accounts.
More about this below.
Security
Programmable hardware tokens came about to replace 2FA apps in situations where it isn’t possible to connect classic tokens. This begs the question: why even bother replacing software tokens with hardware ones?
The thing is, hardware tokens are much more reliable than software tokens. Hardware TOTP tokens can’t be infected by viruses, unlike the smartphones on which authentication apps are installed. On top of that, phones are often lost or stolen, and users sometimes restore them to factory settings or accidentally delete a 2FA app, not realizing that all their tokens will be permanently lost in the process.
There are also cases in which using a smartphone is simply not possible. For example, a user may only have a plain feature phone that doesn’t allow installing apps. Or, a company may introduce mandatory two-factor authentication for accessing corporate resources, but some employees refuse to use their personal phones for this purpose.
| Read also: The Pros and Cons of Different Two-Factor Authentication Types and Methods
Time synchronization
An unavoidable problem with all hardware tokens is that their clocks can fall out of sync with the server. Since hardware OTP security tokens are standalone devices that can’t be connected to any kind of network, their internal clocks are prone to drifting over time.
According to RFC 6238 (the TOTP standard), the possibility of time drift has to be taken into account on the server side. But not all 2FA services follow this recommendation. This is why Protectimus Slim NFC tokens automatically resynchronize their clocks each time they are programmed. That is, every time the token is programmed with a new secret key, the built-in clock is reset to the exact current time. It’s the first hardware TOTP token with such a feature.
| Read also: Time Drift in TOTP Hardware Tokens Explained and Solved
Branding
Protectimus Slim NFC programmable tokens can be produced in your company’s colors and with your logo for orders of even 1 unit. Branding costs US$299 regardless of order size.
We offer branding for all token types, but it’s normally only available for large orders (1000 units or more).

How can I tell whether the Protectimus Slim NFC token is compatible with a service?
The Protectimus Slim NFC token supports secret keys with a length of 16 to 32 Base32 characters. Accordingly, in order to tell whether you can connect this token to a given site or system, you’ll need to find the answers to these questions:
- Is it possible to set up two-factor authentication for this resource using an app?
- What is the length of the shared secret needed to issue a token? If the shared secret length is no more than 32 characters, the Protectimus Slim NFC TOTP security key will work.
We periodically update our list of instructions for setting up two-factor authentication on various sites using the Protectimus Slim NFC hardware security token.
Sites that support the use of the Protectimus Slim NFC hardware token include PayPal, Google, Azure MFA, Office 365, Sophos, Keycloak, Github, WordPress, Dropbox, Mailchimp, Evernote, Facebook, Twitter, Instagram, Reddit, Kickstarter, Slack, Nintendo, LiteBit, ICE3X, AdvCash, Interkassa, Exmo, Bitfinex, Bitstamp, BitKonan, Coinbase, LocalBitcoins, CEX.io, Bitlio, Luno, Livecoin, and Poloniex, to name just a few.
| Read also: One-Time Passwords: Generation Algorithms and Overview of the Main Types of Tokens
How do I program the Protectimus Slim NFC token?
Frequently asked questions
The Protectimus Slim NFC token can only be programmed with one shared secret at a time. However, it can be reprogrammed an unlimited number of times. That means that you can use this OATH TOTP hardware token with only one account at a time, but if you need to, you can unlink it from one account to link it with another. Each time the token is programmed, the previous shared secret is deleted and replaced with the new one.
The OTP token price is US$29.99 per unit. For orders of 50 units or more, you can buy TOTP token Protectumus Slim NFC for US$28.99 or less.
You can connect the token to virtually any service that supports two-factor authentication using Google Authenticator, provided that the shared secret length is within the limit: 16 to 32 Base32 characters. For example, the token can be used for two-factor authentication with Google, PayPal, Office365, Azure MFA, Sophos, Keycloak, Dropbox, GitHub, Facebook, Twitter, Instagram, most payment systems, cryptocurrency exchanges, and other services.
To program this TOTP token generator, you’ll need an Android smartphone that supports NFC and the Protectimus TOTP Burner app. More detailed instructions are available above.
No. The app for programming the Protectimus Slim NFC token is only available for Android.
The battery lasts from 3 to 5 years. The unit has a 12-month guarantee. The battery cannot be replaced or recharged.
The secret key cannot be extracted from the token. The token has no open interfaces, so once after production, it cannot communicate with the outside world (except NFC). But, for NFC, the token does not have an API for reading secret (only writing secret). Additionally, the app does not store secret keys. You can safely use a single phone to program several tokens.
We don’t recommend doing this, since you could accidentally drill into the electronics.
TOTP hard token with your company’s own design can be ordered in quantities of 1 unit or more. Branding costs US$299 regardless of order size.
An Android smartphone is needed only to program the token. After that, the token will work on its own without a phone.
Read more:
- How does 2-factor authentication work?
- The Evolution of Two-Step Authentication
- 4 Reasons Two-Factor Authentication Isn’t a Panacea
- Electronic Visit Verification with Hardware Tokens
- Two-factor authentication for Windows 7, 8, 10
- Active Directory Two-Factor Authentication
- 2FA Chatbots vs. SMS Authentication
- Best Protectimus MFA Features for Financial Services Cybersecurity
Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from our team.

Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from Protectimus blog.
You have successfully subscribed!