Among the available MFA deployment options, on-premise solutions have gained traction, especially among organizations with stringent security policies and a strong desire for control. Unlike cloud-based alternatives, on-premise MFA systems are installed directly on the client’s infrastructure or private cloud, offering unparalleled oversight and customization opportunities. On-prem MFA solutions eliminate reliance on external networks, ensuring maximum protection for sensitive data and systems.
The Protectimus On-Premise MFA Platform is a versatile and comprehensive multi-factor authentication solution tailored to meet the unique needs of businesses prioritizing security and control. Designed to operate seamlessly within isolated networks, our platform combines advanced security features with the flexibility to adapt to diverse organizational requirements. In this article, we will delve into the pros and cons of on-premise MFA, explore the standout features of the Protectimus 2FA platform, and provide insights into its architecture including the standalone cluster architecture.
Pros and Cons of On-Premise MFA
Using on-premise MFA provides unparalleled control over your data, processes, and the system’s fault tolerance, as well as robust protection against potential attacks. Organizations can design a security system around their authentication server tailored to their specific needs. This includes deploying firewalls, completely isolating the server from external access, and implementing any other security measures deemed necessary.
Advantages:
- Complete Control: full authority over sensitive data, system operations, and infrastructure.
- Enhanced Security: operates in isolated environments, reducing vulnerabilities and minimizing exposure to external threats.
- Customization: allows tailored configurations and the addition of unique features to meet specific organizational needs.
- Compliance: facilitates adherence to stringent regulatory requirements by keeping all data within the organization\u2019s premises.
Disadvantages:
- Higher Costs: requires a significant upfront investment in infrastructure, setup, and ongoing maintenance.
- Resource-Intensive: demands skilled IT personnel and continuous administrative effort.
- Longer Implementation Time: compared to cloud-based solutions, on-premise systems take more time to configure, deploy, and optimize.
Key Features of the Protectimus On-Premise MFA Platform
The Protectimus On-Premise MFA Platform can be installed locally or in a client’s private cloud, granting full control over the authentication system, including sensitive user data. The platform supports multidomain environments, clustering, replication, and backup functionality to ensure resilience and security.
Additional features include geographic and time-based filters, event notifications, detailed analytics and reporting, role-based access control, and a data-signing feature (CWYS – Confirm What You See).
The platform is compatible with all Protectimus two-factor authentication methods including both hardware and software tokens and supports OTP delivery via SMS (SMPP protocol), email, and chatbots. It enables integration across diverse environments and ensures high availability and reliability.
Cross-Platform Compatibility:
- Supports Linux, FreeBSD, Windows, and other major operating systems.
- Compatible with Google Chrome, Mozilla Firefox, Internet Explorer, and other popular browsers.
Industry-Standard Security:
- Fully compliant with OATH OTP standards.
- Utilizes HMAC, HOTP, TOTP, and OCRA algorithms for generating secure one-time passwords.
Scalable and Flexible:
- Includes a self-service portal for users to manage tokens and personal data.
- Allows administrators to configure access filters based on geography, time, or user behavior.
- Enables multi-node setups for large enterprises with globally distributed users.
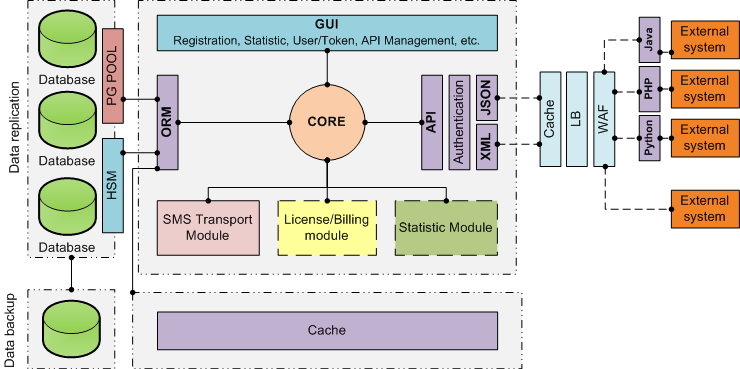
Protectimus MFA System Architecture
Protectimus is built following the best practices of SOA (Service-Oriented Architecture), MVC (Model-View-Controller), and RESTful design principles. This foundation ensures seamless scalability, fault tolerance, and high performance. Let’s look at the overall solution architecture presented below.
Performance Optimization:
- Client-Side: implements browser caching, resource minimization (HTML, CSS, JavaScript), and image optimization.
- Server-Side: uses Memcached for caching, Nginx for static content optimization, and load balancing for performance enhancement.
- Database-Side: optimized database settings, indexing, and partitioning improve query efficiency.
User Interface:
- Managed via a responsive GUI based on Twitter Bootstrap, ensuring compatibility with various devices and browsers.
Integration:
- RESTful API supports XML and JSON data formats for seamless interaction with client systems.
- Prebuilt libraries in Java, Python, and PHP simplify integration.
- Ready-to integrate components and plugins for RADIUS, Windows and RDP, Ubuntu, MacOS, OWA, ADFS, Active Directory, LDAP, Roundcube, etc.
Token and Authentication Options:
- Supports all OATH-compliant tokens and authentication methods (HOTP, TOTP, OCRA) for flexibility including classic and programmable hardware OTP tokens, MFA authenticator apps for generating one-time passwords, one-time password and notification delivery through Telegram, Viber, and Messenger, OTP delivery via email.
- SMS delivery of OTPs ensured by integration with the client’s chosen SMS provider.
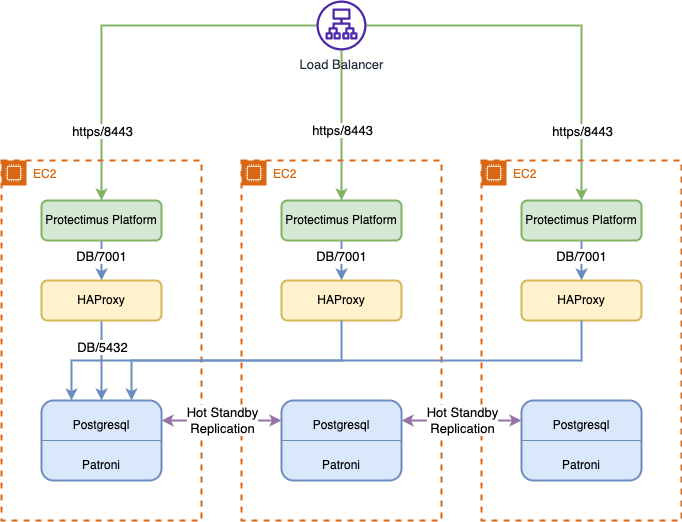
Protectimus On-Premise MFA Platform Cluster Functionality
The Protectimus on-premise MFA platform cluster is designed with a robust, fault-tolerant architecture that guarantees continuous availability and seamless performance, even in the face of node failures.
At its core, the cluster comprises a minimum of three nodes, ensuring resilience and high reliability. In environments with resource constraints, a simplified setup of two standard nodes and a third minimal-resource arbitrator node can be deployed to maintain quorum for master node election.
The platform utilizes Patroni for PostgreSQL clustering, which automates key processes such as node failover, recovery, and reintegration into the cluster, ensuring smooth operations with minimal disruption.
While the platform’s distribution does not include a built-in load balancer, it offers flexibility for clients to integrate one of their choice, with HAProxy being a commonly used option. HAProxy monitors the health of the cluster and directs traffic to the active master node, optimizing load distribution.
This architecture ensures high availability, seamless performance, and fault tolerance, making Protectimus an ideal solution for organizations that prioritize both security and reliability in their MFA deployments.
Here is the standard Protectimus MFA Platform cluster scheme with three nodes:
Key Features of the Cluster Setup:
- Fault Tolerance: standard configuration includes at least three nodes, ensuring high availability and reliability.
- Lightweight Arbitrator Node: in smaller setups, a minimal-resource arbitrator node provides quorum to ensure proper master node election.
- Traffic Distribution: HAProxy monitors the health of the cluster and distributes traffic to the active master node.
Patroni’s Role:
- PostgreSQL Clustering: Patroni manages automatic failover, node recovery, and query load balancing.
- Efficient Query Processing: secondary nodes handle replication, ensuring efficient load distribution.
Backup and Replication:
- Robust Backup Systems: Protectimus ensures data safety with comprehensive backup and replication mechanisms, preventing data loss.
- Rapid Recovery: in case of a node failure, rapid recovery capabilities ensure uninterrupted operations.
Global Reach:
- The platform’s distributed architecture allows deployment across multiple geographic zones, ensuring optimal performance for users regardless of their location.
Real-World Applications and Use Cases
The Protectimus On-Premise MFA Platform is ideal for industries requiring the highest levels of security and compliance, such as finance, healthcare, government, and enterprise sectors. Its flexible, scalable architecture ensures robust protection for sensitive data and user identities, making it the preferred choice for organizations with stringent security needs.
Organizations across various sectors have successfully implemented Protectimus, significantly reducing the risk of unauthorized access and enhancing user authentication. Here are some case studies showcasing how customers benefit from the Protectimus On-Premise MFA Platform.
Read more:
- On-Premise 2FA vs Cloud-Based Authentication
- Multi-Factor Authentication for LDAP
- Strengthening Security with Multi-Factor Authentication for RADIUS
- Protectimus MFA Prices: How to Save with Coupons, Discounts, Referrals, and Subscriptions
- Strengthening Security with Multi-Factor Authentication for RADIUS
- Keycloak Multi-Factor Authentication With Hardware Tokens
Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from our team.





Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from Protectimus blog.
You have successfully subscribed!