In this article, we’ve gathered everything you need to know about remote work. We share our own experiences and talk about how to organize remote access to company resources, how to protect the accounts of users who are working from home, what remote team working tools you can use for communicating and managing tasks, and how to keep in touch with your remote teams.
Working remotely during the pandemic is not a mere trend. Today, with the number of people infected by the coronavirus that causes COVID-19 rising exponentially, and given that a cure or vaccine for the virus has yet to be discovered, the only means of fighting the epidemic is social distancing and learning how to work from home.
Many countries have already implemented a quarantine. Airports, train stations, schools, restaurants, gyms, malls, beauty salons, and (in some cases) even parks and playgrounds have been closed. Concerts, lectures, and conferences have been postponed. In this situation, a majority of private and public entities have been forced to transition to having their employees work from home whenever feasible.
We suggest that business owners view this transition to remote work as an opportunity to learn about new remote workplace software and optimize their resources. Facing an imminent economic crisis, we have to use all the means at our disposal to adapt to difficult market conditions and press onward.
In this context, particular attention must be given to the topic of cyber security and risk management. Remote network connections are an additional avenue of attack for would-be intruders. We’ll tell you what you should be afraid of, what basic cybersecurity tips and rules you should implement for remote workers, and how to secure remote desktop connection to workplace computers.
Table of contents:
- Where do I start?
- Setting up remote access
- Essential tools for remote work
- IT security threats when working remotely
- Cybersecurity when working from home
Where do I start?
- Think about the technology employees will use to work remotely. If people use company laptops, they can take these home with them during the quarantine. If employees use desktop computers, you’ll need to set up remote access to these computers.
- Take care to protect remote connections and user accounts on company computers. Be sure that employees set secure passwords and activate two-factor authentication for all the services they use to do their work. Enable two-factor authentication for Windows and Microsoft RDP.
- Prepare a remote working software package for communicating, working with documents, tracking tasks, and holding presentations online. Most likely, you’re already using tools in most of these categories. If something is missing, you’ll need to choose team software and install it on all your employees’ computers.
- Maintain security policies for working from a computer at home. Hold mandatory training on the basics of IT security and come up with a remote work policy. Some of your employees may not know what phishing, malvertising, and social engineering are, why they shouldn’t connect to an unknown Wi-Fi network, and why they shouldn’t save usernames and passwords in a file on the desktop.
Setting up remote access
The remote access software available depends on the operating system installed on users’ workstations.
- Windows: If you use Windows, it’s best to organize remote desktop connection over the RDP (Remote Desktop Protocol). To do so, use the built-in Microsoft Remote Desktop program (available under Windows Professional, Enterprise, and Ultimate). If you use a different version of Windows, the best free remote desktop software for you is Microsoft Remote Assistance.
- macOS: Use the standard Screen Sharing application. You can also set up remote desktop connection for Mac using a third-party program or find out how to use Chrome Remote Desktop.
- Linux: Under Linux, as with any other operating system (Windows, macOS), third-party software for remote computer access, such as TeamViewer, AnyDesk, or Chrome Remote Desktop, will work.
- Large companies should also consider infrastructure solutions for remote work from Citrix, VMWare, and Cisco. In general, these solutions are expensive, but they guarantee the required level of remote desktop security.
Connecting to a remote desktop over RDP
During the 2020 quarantine brought about by the COVID-19 epidemic, a portion of the Protectimus team transitioned to working remotely. To do so, remote computer access was set up using the RDP client over a VPN. The VPN is used to access the corporate network, while RDP protocol is used to connect to a remote workstation. We also protect our employees’ Windows user accounts with two-factor authentication for Windows remote desktop.
This system of connecting to a remote workstation running Windows 7/8/10 makes it possible to maintain a well-secured connection. The VPN and RDP provide an encrypted connection, and thanks to the use of two-factor authentication tokens, we can be sure that it’s our employees accessing the PCs remotely, not an attacker. We recommend that you, too, configure remote access in a similar manner to ensure a remote desktop connection security. You can find out more about how to set up remote desktop access using a VPN and RDP here.
Remote connection over RDP is available only for the Pro version of Windows and above. However, users can connect to a remote Windows desktop over RDP regardless of the operating systems they use on their home devices (Windows, macOS, and even Android and iOS). For Windows remote desktop connection from macOS, Android, or iOS, they’ll also need to install a free RDP client.
To do work over the RDP, the server computer must be turned on. Once the user connects to the Windows remote desktop over RDP, the RDP server computer’s screen will be hidden until the end of the session.
Connecting to a remote desktop Windows 10 / 8 / 7 makes it possible to use all of the remote computer’s resources and view the Windows 10 / 8 / 7 remote desktop just as if the user were working directly with that computer. Files can be transferred to the remote desktop using a shared clipboard, and local devices (such as printers, scanners, and hard disks) can be connected to the remote PC.
Setting up two-factor authentication for VPN
If you use VPN clients (SonicWall, Sophos, Cisco, etc.) to secure your remote access, take care to additionally protect your VPN with two-factor authentication.
It’s quite easy to integrate Protectimus two-factor authentication system with any VPN supporting RADIUS protocol. Read more about VPN two-factor authentication and get in touch with our support team, who’ll be glad to assist you with adding 2-factor authentication to your corporate infrastructure even in real-time.
Setting up two-factor authentication for RDP
The Protectimus Winlogon is a Windows and remote desktop two-factor authentication solution that enables you to set up two-factor authentication on computers running Windows operating systems, so you can protect Windows user accounts for both local access and remote access over RDP.
- Download the Protectimus Winlogon installer.
Navigate to https://www.protectimus.com/winlogon/ to download the Protectimus Winlogon installer and detailed solution setup instructions.
- Register with the Protectimus SaaS service.
Follow this link to the Protectimus two-factor authentication cloud service and sign up.

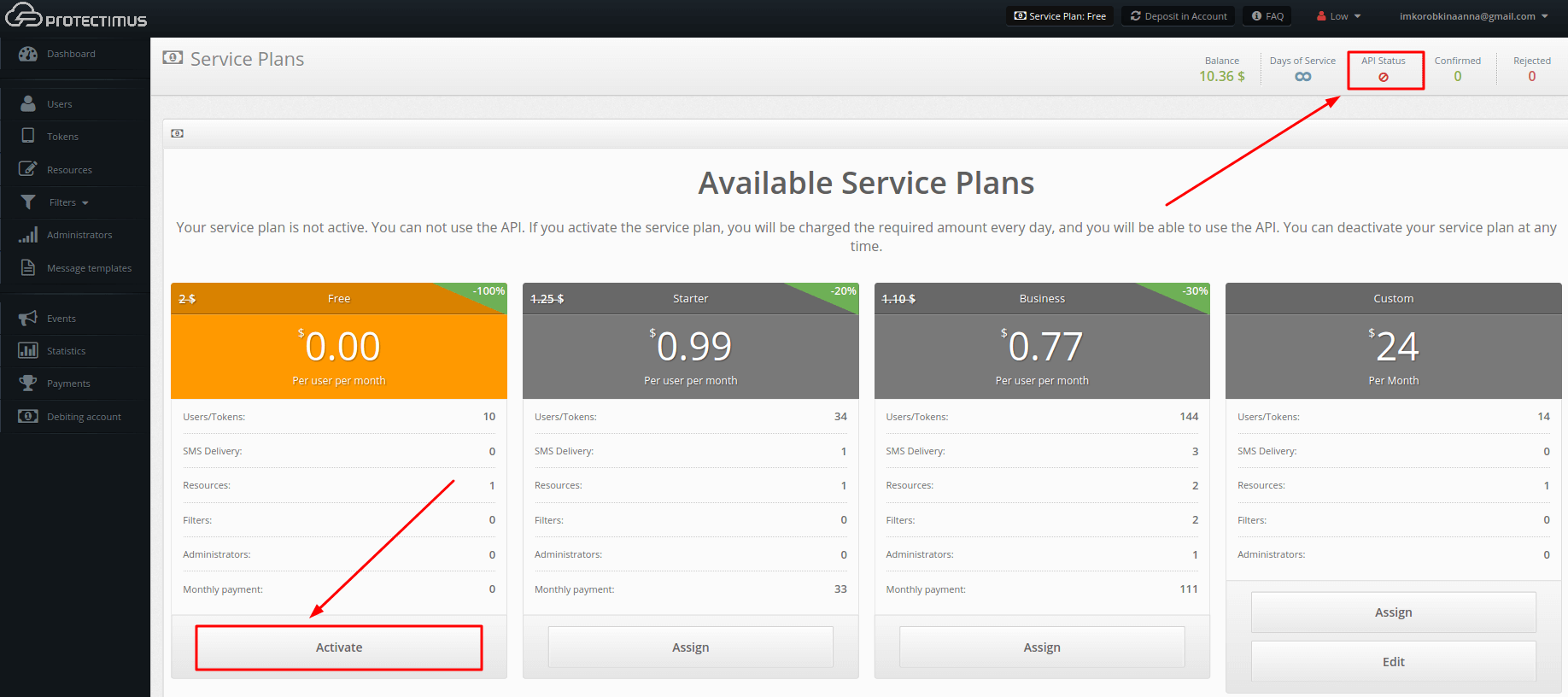
- Activate a service plan to activate the API.
Navigate to the Payment plans section and activate the plan that meets your needs. First, click Assign, and then, click Activate. The Free plan must also be activated. After activating a plan, you’ll notice that the API status in the upper-right corner changes to active.

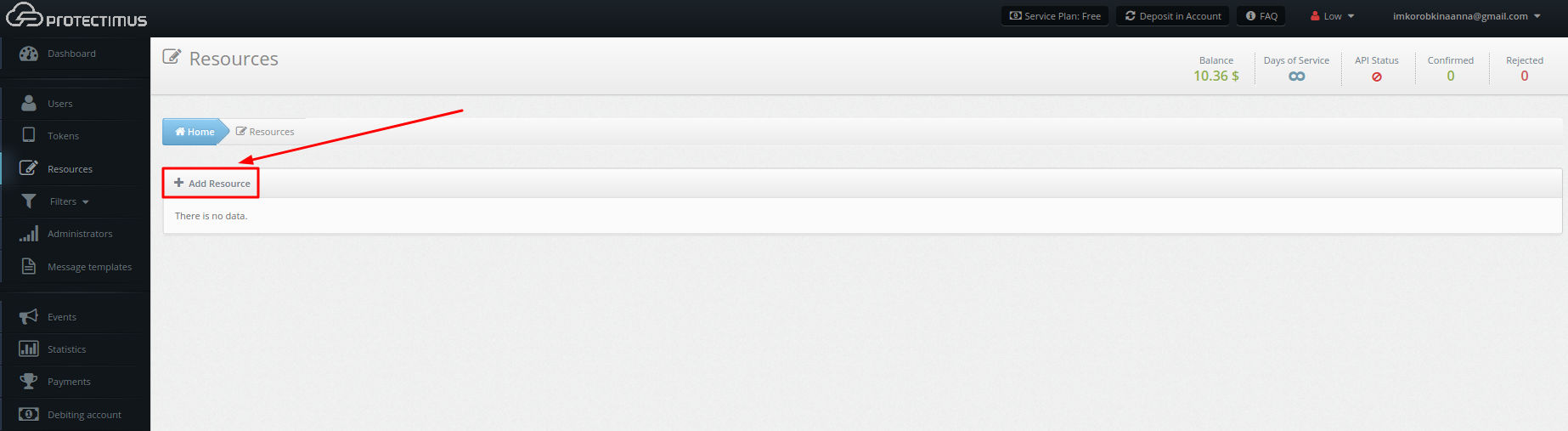
- Create a resource.
Navigate to the Resources section. Click the Add Resource button, type a name for the resource, and set the other parameters as you like.

- Create users and tokens.
You can add users and tokens manually (you can find more about creating tokens and users manually in the Protectimus Winlogon setup instructions, which you already downloaded), or you can activate automatic registration. If you use automatic registration, users will be able to create only Protectimus Smart, Protectimus SMS, and Protectimus Mail tokens.
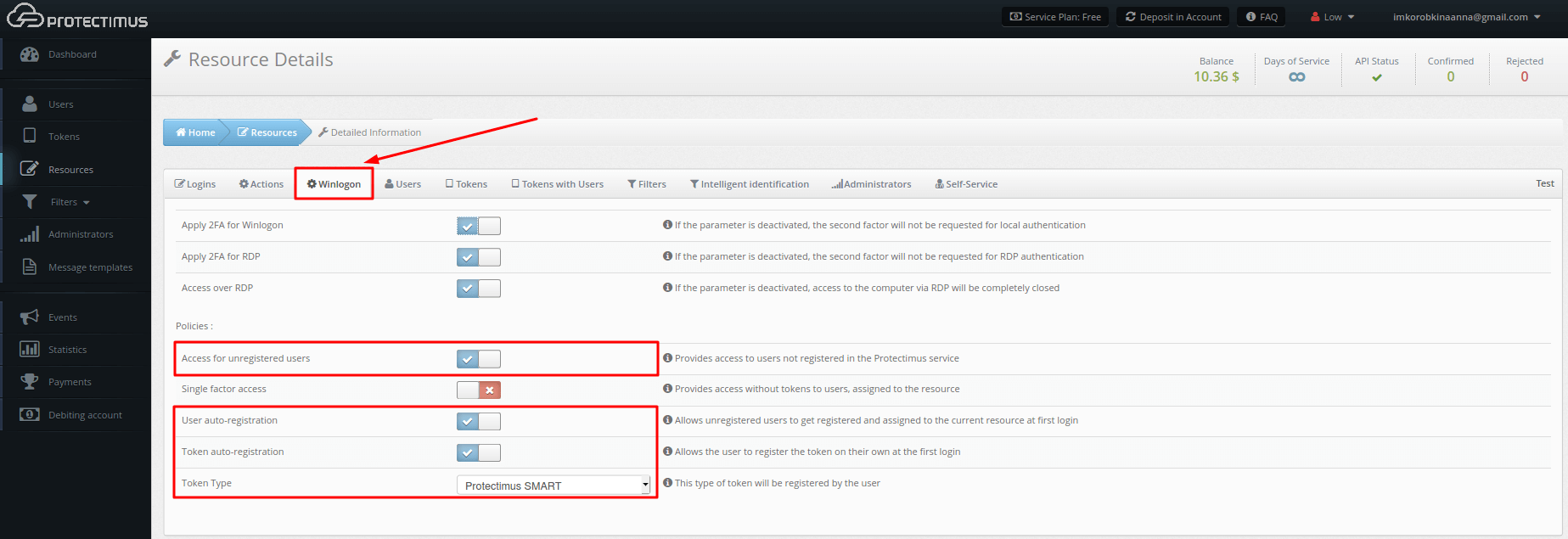
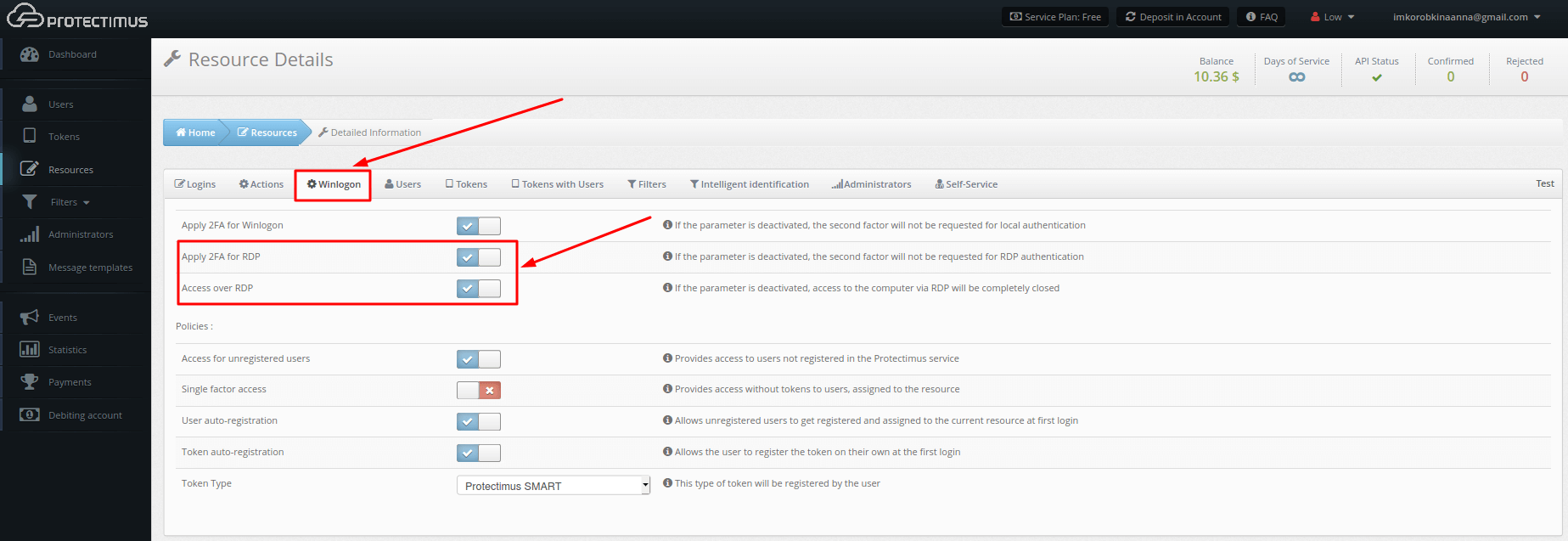
To activate automatic user and token registration, navigate to the Resources page. Click the name of the resource, select the Winlogon tab, and mark the following options:
– Access for unregistered users
– User auto-registration
– Token auto-registration
– Select token type users can create
After activating automatic registration, the first time users log into their accounts, they’ll enter their normal Windows usernames and passwords. Then, they’ll issue a token.
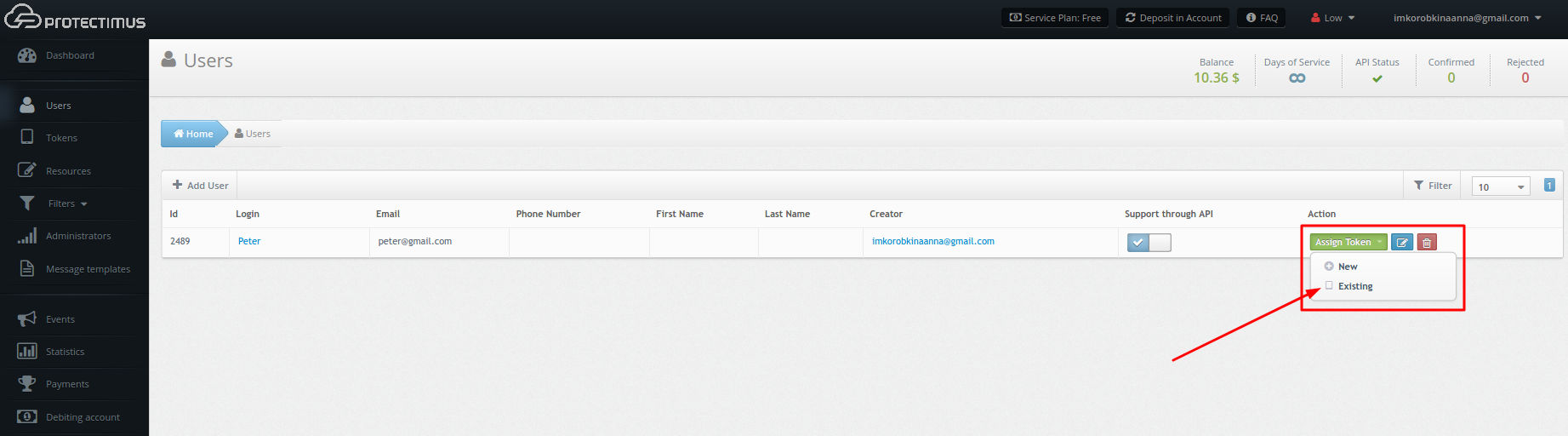
- Assign tokens to users.
Skip this step if you activated automatic user and token registration!
Navigate to the Users page and assign the tokens you just created to the corresponding users. To do so, click Assign Token — Existing, select the token, and click Assign.
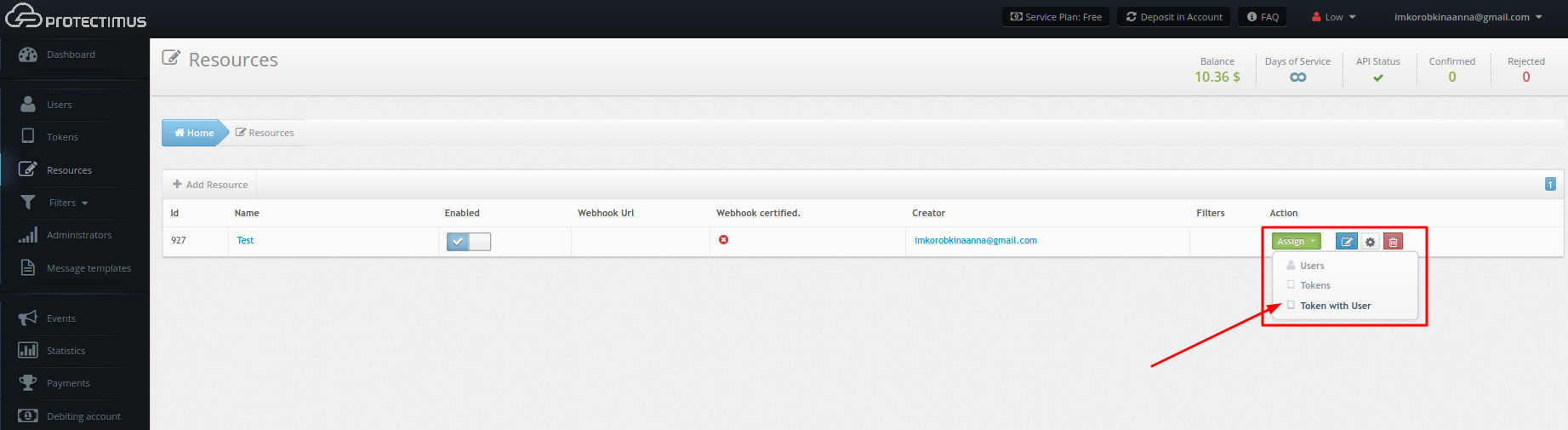
- Assign tokens with users to a resource.
Skip this step if you activated automatic user and token registration!
Navigate to the Resources page. Click Assign, choose “Token with user”, and select the tokens to assign to the resource.
- Run the Protectimus Winlogon installer as an administrator on the computer that will receive RDP connections and install the software.
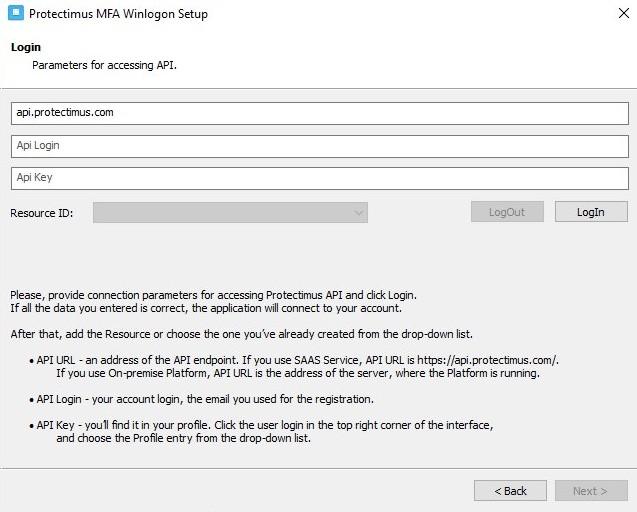
The installation process is intuitive. During one step of the process, you’ll need to specify the following parameters:
– API URL. Use the API URL https://api.protectimus.com/.
– API Login. This is the login you chose when registering with the service (that is, your email).
– API Key. You’ll need to copy your API key from the Profile page. To navigate to your user profile, click on your username in the upper-right corner of the interface. Then, choose “Profile” from the drop-down list.
You can find additional details in the Protectimus Winlogon setup instructions that you downloaded.
- Set up Windows remote desktop two-factor authentication.
Navigate to the Resources page, click the name of the resource, and select the Winlogon tab.
Turn on the “Access over RDP” setting. Turning on this setting allows accessing computers over RDP without two-factor authentication.
Turn on the “Apply 2FA for RDP” setting to enable two-factor authentication for RDP access requests.
| Read also: Active Directory Two-Factor Authentication
Essential tools for remote work
Cloud services for remote work
Saving work-related files and folders on a home computer is inconvenient, besides, and it’s an additional security risk. Cloud services like G Suite or Office 365 are essential for working with documents. This is highly practical and important to protecting company data. It would be virtually impossible for our team to work remotely without Google Drive.
G Suite and Office 365 offer a complete range of tools for collaborating on text documents, spreadsheets, and presentations. Files, folders, and documents are stored in the cloud, not on employees’ home PCs. That means documents won’t ever get lost, you can access them from anywhere in the world, you’ll always have the latest version of every document, and any team member who has access can make changes or leave comments. Also included are tools for making video and audio calls, task managers, and calendars.
Prohibit users from storing work documents on their home PCs in your remote work security policy. All files should be stored in the cloud, and users’ G Suite or Office 365 accounts should be protected with two-factor authentication. Using hardware tokens for authentication provides the highest level of remote working cybersecurity. The Protectimus Slim NFC can be connected to a Google account or to Office 365.
Messaging apps
You’ll need to choose a convenient messaging app (like Telegram, Slack, Discord, or Skype) to communicate with your team. If you have a smaller team (up to 50 people), Telegram is a suitable choice. Larger companies prefer Slack. Most commonly, Skype and Zoom are used for video meetings.
If you don’t want to use a third-party app to handle internal communication, consider Rocket.Chat, an open source messaging app. It can be installed on your company server and it’s free. That way, all data exchanged by employees in chats will remain on company servers.
Working from home requires each employee to have your chosen messaging app installed. Typically, a general chat for all employees is created to publish announcements, and smaller chats are created for each individual project, so people can discuss their ongoing tasks. Calls are better for resolving serious issues.
| Read also: Which messaging apps are trustworthy?
Task managers and CRM
You’ll need a task manager (like Trello, Asana, or Jira) to set tasks and monitor remote team working progress. To work efficiently with your customers, you’ll need a CRM (customer relationship management) system. Often, task managers and CRM systems are available in a single package (like Zoho, Bitrix, and Asana, mentioned before). Each task manager has its own strengths and is appropriate for different kinds of projects. For example, Jira is often used in the IT industry because it’s excellent for tracking development stages. Smaller companies often choose Trello because it’s a free task manager that’s also straightforward and convenient to use. Try a few options and choose the one that suits you best.
Video calling, presentation, and conferencing tools
During the quarantine, all meetings and presentations have to be conducted online. Remote working also forces you to call your team to discuss important issues. It’s a good idea to enable your camera and learn how to share your screen for these calls. Be sure that your sales team is set up to use a variety of video calling tools, like Skype, Zoom, Google Hangouts, and GoToMeeting.
| Read also: 9 Must-Follow Gmail Security Rules
IT security threats when working remotely
Working from home involves an increased risk of company data leaks and provides attackers with additional opportunities to penetrate your company network. This is because it’s impossible to know how employees’ computers are set up, how technically literate they are, and how many third parties (family members, friends, hackers) have access to these computers.
For hackers, COVID-19 and the quarantines implemented by most countries around the world are a dream come true. During the quarantine, with almost every business forced to switch to online work, hackers will be focusing all their efforts on finding ways into poorly protected computers and networks. Hackers try to find the “weakest link”: whose computer has already been infected by a virus, who is using weak passwords, who isn’t protecting their accounts with two-factor authentication, and who clicks on links in phishing emails from unknown senders. All this is in order to compromise a user’s home computer and, through it, access a corporate network. Governments and financial institutions should be especially cautious, as well as big companies that save large amounts of data on their servers.
Confidential information can be leaked
- An employee’s personal computer being used to access a Windows remote desktop may be infected by malware.
- An employee may become the victim of a phishing or social engineering attack if they aren’t prepared and informed about these potential threats.
- A user may lose a personal laptop or smartphone with an open remote desktop connection to Windows 7 / 8 / 10.
- A device set up for a secure remote desktop connection, and which has usernames and passwords saved on it, may stop working and require repairs.
- A single account on an employee’s home computer may be shared with all of the employee’s family members / friends / neighbors. There is a good chance that at least one of them will download a file containing a virus. It’s also impossible to exclude the possibility that one of these people would like to gain access to your company network.
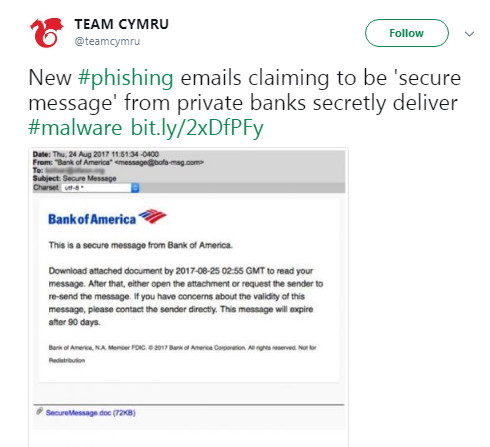
Malware can compromise corporate networks
If a computer used for remote work is infected by malware, then the entire corporate network could also be infected. The source of the virus might be a torrent download or a phishing email. However, the main reason such a threat can exist is a lack of antivirus software on users’ computers.
Unauthorized users can gain access to company networks
If a user has a weak password and doesn’t use two-factor authentication, there is an extremely high risk that the user’s account will be compromised. A home computer may be infected by malware capable of collecting or intercepting usernames and passwords. Additionally, someone else in the user’s environment may use their login details to gain access to the company’s internal infrastructure (we all know how usernames and passwords can be carelessly written on a piece of paper left near the computer or stored in a “passwords” file on the desktop).
| Read also: Ransomware – to Pay or Not to Pay
Cybersecurity tips when working from home
- Encrypt network traffic for connections to remote workstations.
- Use two-factor authentication when connecting to a remote desktop.
- Inform employees of basic cybersecurity rules; ideally, incorporate your remote work from home policy into your standard contract as a separate section.
Protecting remote connection
When setting up remote access to computer over the internet, be sure the connection is secure. Use an encrypted VPN or set up another means of encrypting network traffic. For example, even if you use RDP directly, without a VPN, the Microsoft Remote Desktop app lets you configure additional encryption options and change the RDP port.
Two-factor authentication
2-factor authentication should be activated for every service your employees use. It acts as a barrier that is almost impossible for attackers to penetrate.
Two-factor authentication protects you from brute-force attacks and keyloggers. It often saves accounts from being compromised after a successful phishing, social engineering, or man-in-the-middle attack. It also prevents unauthorized access by other people with physical access to a computer, as well as by hackers that have obtained usernames and passwords in an attack.
Be sure that two-factor authentication is set up for all critical nodes:
- First and foremost, set up two-factor authentication for remote desktop. If you use other tools to enable remote work, such as Citrix or VMWare products, set up two-factor authentication via RADIUS.
- Encourage users to install Protectimus Winlogon on their home computers if they use Windows, or to enable the built-in two-factor authentication if they use macOS.
- All employees should enable two-factor authentication for cloud services the team will be using to collaborate on documents (Google, Office 365, etc.).
We recommend using hardware tokens to generate one-time passwords.

Choosing OTP tokens for remote work
Order hardware tokens for all employees to use in generating one-time passwords. This is the most reliable means of two-factor authentication.
- For Windows and RDP authentication via Protectimus Winlogon, connect Protectimus Two hardware tokens. These are the most reliable, cost-effective tokens for this context. The Protectimus Slim NFC is also an excellent choice, but it is a more expensive token. If you have a limited budget, the Protectimus Smart 2FA app or messaging service chatbots on Telegram, Viber, and Facebook Messenger also provide a good level of security. We recommend avoiding SMS authentication since it’s expensive and not secure.
- For the G Suite and Office 365 cloud services, use Protectimus Slim NFC tokens, since only programmable hardware tokens can be connected to these services.
Windows и RDP(when using the Protectimus Winlogon solution) | ||
Recommended tokens | Level of protection | Token features |
|  |
|
|  |
|
|  |
|
|  |
|
GSuite | ||
Recommended tokens | Level of protection | Token features |
|  |
|
|  |
|
Office 365 | ||
Recommended tokens | Level of protection | Token features |
|  |
|
|  |
|
| Read also: The Pros and Cons of Different Two-Factor Authentication Types and Methods
Security policies
Your duty is to clearly state your IT security rules for remote work and inform employees of them. Each member of the team needs to know how to act in order to minimize the risk of having their user account compromised.
Your remote work policy template might look something like this:
- When finished working, do not forget to disconnect from the VPN and RDP.
- Do not share login details and tokens with anyone.
- Do not save login details on your computer or write them down anywhere.
- Do not allow others to use your PC with the VPN and RDP connected.
- Do not download data from work computers to your home PC. Perform all operations exclusively on a work PC, or on a collaborative cloud service when working with documents.
- Enable two-factor authentication in Windows / G Suite / Office 365.
- Be certain that your home PC is not infected by viruses. If you aren’t sure, download antivirus software and scan your system. If you still have doubts or questions after running a scan, contact the system administrator.
- Do not open links in, or download files from, emails from unfamiliar senders.
Employees should follow basic security rules regardless of where they work, at home or at the office. For this reason, we recommend regularly holding IT security “master classes” and training sessions to teach employees to recognize phishing and social engineering, use passwords managers and two-factor authentication, change passwords every few months, and not reveal too much personal information on social networks.
How long citizens will remain isolated is uncertain. Epidemiologists have made a variety of predictions. Some claim that the quarantine may be extended until next spring. You start transitioning your team to remote work as soon as you can, and we’ll help you take care of security. You can contact us with questions at any time by writing to [email protected].
Read more:
- Duo Security vs Protectimus
- Best Protectimus MFA Features for Financial Services Cybersecurity
- Hardware Tokens for Azure MFA
- Time Drift in TOTP Hardware Tokens Explained and Solved
- Keycloak Multi-Factor Authentication With Hardware Tokens
- 10 Steps to Eliminate Digital Security Risks in Fintech Project
- 10 Most Popular Two-Factor Authentication Apps Compared
- 2FA Security Flaws You Should Know About
Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from our team.






2020-04-27
Thank you for an informative article. You covered almost all pressing issues but one: how to track team productivity. Is it worth using the productivity tracking software tools, what do you think?
2020-04-27
For daily meetings we’ve recently switched to Whereby. The interface is exceptional and extremely easy to use, not to mention the call quality.
2020-04-28
Hey! Thank you for the advice, maybe we’ll give it a try too.
2020-04-28
If I use this tool for RDP two-factor authentication, does this mean I’ll have to install this software on each office machine in the environment manually? Considering there are around 300 computers, it’s not very convenient.
2020-04-28
Hi Michael! Not to install the application separately on each computer, automate the installation creating and deploying an MSI through GPO (Group Policy Object). Protectimus Winlogon features allow this.
2020-09-08
Is NLA maintained with RDP use or does TLS use need to be disabled to support the use of Protectimus and thus RDP use be forced to Standard RDP security?
2020-09-08
Hi William! Our component replaces a standard credential provider and extends the authentication logic. The process of verifying the first factor remains standard, so, in theory, everything should work fine. But make sure that both the RDP client and server are upgraded to the last version.