MFA is usually viewed as a sensible thing to have, and indeed, sometimes your partners or regulators can request setting multifactor authentication up before you can start operating at full capacity. Well, let’s dive into the main specifics of it!
So, you are weighing all pros and cons regarding the implementation of MFA authentication in your business. And naturally, you are leaning towards making the best use of it. Setting multi-factor authentication up can be a daunting task, and we’re here to cover all you’d ever need to know about it:
What Is MFA and How It Improves Your Business Security
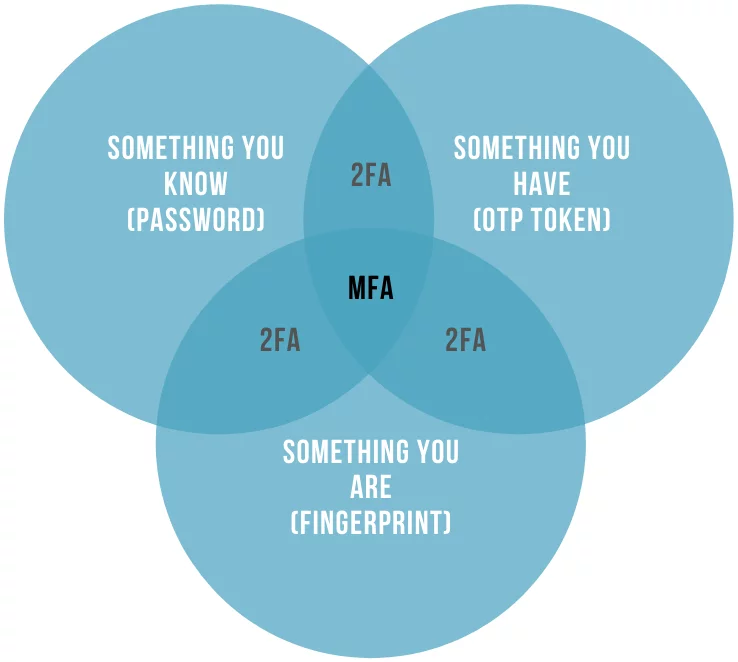
Let us first define what is multifactor authentication in general terms, and how it can help you to protect your business. MFA adds additional protection layers to any authentication attempt your employees and users will make to assign to their accounts. Multifactor authentication is a combination of two or more different authentication factors that your trusted users would use to access their accounts:
- Knowledge-based, aka passwords and secret questions. Most of the data on the Internet is protected by passwords and choosing a good password can be a challenging task in itself. Learn how to choose a strong password that is easy to remember here.
- Inherence-based, aka biometrics. This one can include fingerprints, voice recognition, and other biometric data.
- Possession-based, aka additional stuff that you (and only you) might have. It’s usually a small device that generates one-time passwords — OTP token, a phone, or, for example, a banking card.
Also, some additional authentication factors can be used over and above the classic three:
- Location-based, aka IP verification or geographic filters. It tries to utilize the information regarding the proximity of a device and/or its user regarding other devices that are usually used in the authentication. One particular example here would be checking the network the authentication attempt comes from and comparing its parameters to some trusted value.
- Action-based, aka adding a requirement for a user to participate in some sort of distinct activity. For example, filling out a CAPTCHA.
As you see, multifactor authentication can be a very versatile tool, and it depends on the needs of your particular business which authentication methods to choose. Your chosen MFA solution and types of authenticators will depend on the needs of your particular business which are some very particular things, such as the number of your employees; their degree of personal compliance and responsibility; the laws of the country that your office is stationed in; the sensitivity of the data you utilize; the type of service you provide for your clients, and the possibility of THEM losing any of their data when interacting with your business; any sort of certifications that your line of work might demand (such as PCI DDS for finances or HIPPA if you work in healthcare). So, before setting up any solution you must have this information prepared and organized.
And there is always an important thing to keep in mind: MFA can protect your data from malicious actors, but it won’t protect it against destructive negligence. As it asks from its users for more involvement, they tend to do ever less. You must efficiently balance asking and delivering: your chosen solution must be secure enough to do its job, and unobtrusive enough to keep its users from trying to circumvent it.
| Read also: 6 MFA Myths You Still Believe
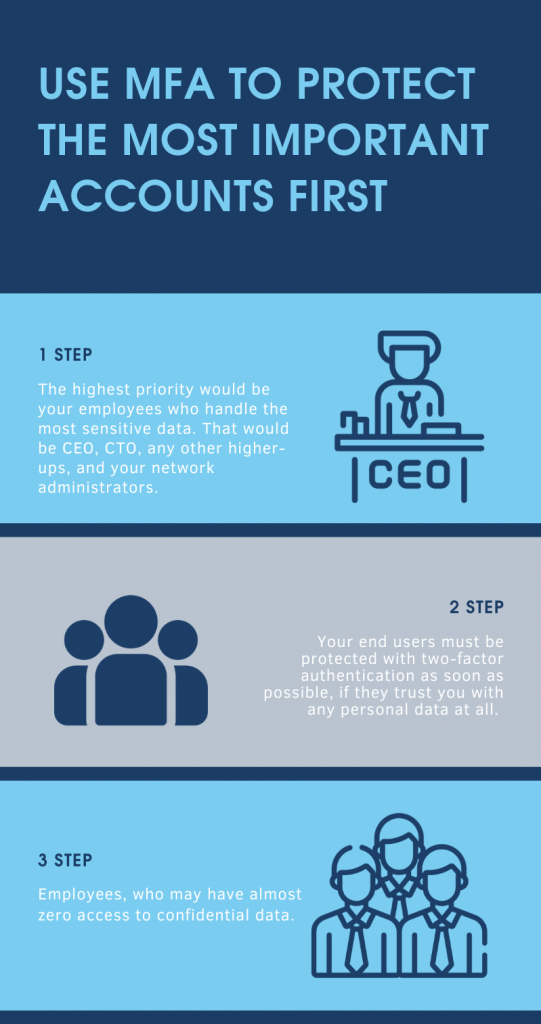
1. Use Multifactor Authentication to Protect the Most Important Accounts First
We’ve established that MFA security is a fairly complex venture that asks for your time and money, and also can inconvenience your employees.
So, can you cut corners here? As it turns out, you can.
Your MFA will cover different groups of people within (and outside) your company. While your local laws and business standards may require you to commit to full MFA coverage, an easier and more practical solution would be to pick out some priority groups first.
- The highest priority would be your employees who handle the most sensitive data. Most of the cases that would be CEO, CTO, any other higher-ups, and your network administrators.
- Your end users also should be protected if they trust you with any personal data at all.
- Another group would be your regular employees, who may have almost zero access to confidential data.
As a rule of thumb (and also according to NIST (The US National Institute of Standards and Technology) guidelines) MFA should be used whenever possible. But if you are on a tight budget, you might want to test your solution on a smaller group of people first. Showing your colleagues, partners, and clients that you have two-factor authentication will usually work as a sign of good faith — for starters. This is especially important for any healthcare or financial institution, more so if there were any data breaches recently. Prioritize your administration when you are starting to organize the inner workings of your business, and switch the focus to your end-users whenever you start going public.
| Read also: Best Protectimus MFA Features for Financial Services Cybersecurity
2. Choose Most Practical MFA Solutions
Your chosen 2-factor authentication service must be versatile enough to support multiple authentication methods so you can switch and adapt to any given situation on the fly. It also must be convenient and easy both in implementation inside your given workspace, and in usage by your team. Consider if your MFA options do more good than harm to your regular employee — securing that database is, of course, paramount, but do you really need to ask the one-time password each time the session expires?
Then again, things cost money. It can be impractical and quite expensive to give a hard token to each and every one of your employees. Perhaps some of them will be better off with a free OTP delivery via chat-bots in messaging apps or 2FA apps, especially if they utilize their own devices at work. And those who don’t agree to use their own devices as 2FA tokens, can get programmable hardware OTP tokens like Protectimus Flex or Protectimus Slim NFC. Also, you can order hardware OTP tokens for the system administrators and other employees who have the highest level of access to confidential data, as hardware tokens are the most reliable authentication method. Read more about the pros and cons of different two-factor authentication methods here.
Your ideal MFA solution should look like this:
- easy to install and maintain;
- compatible both with your technical requirements and software and hardware (Windows and RDP, OWA, ADFS, Azure, VPN, etc.);
- flexible enough to accommodate your business with a variety of authentication factors;
- user-friendly and making good use of adaptive authentication features;
- respects the time and efforts of your network administrators;
- being affordable and not overpriced for the amount of utility that it offers.
Do your best to keep up with the latest trends in the world of cybersecurity, as it may both save you money otherwise spent on inefficient solutions, and save your data from unreliable MFA security solutions. For example, SMS codes, while still fairly standard, are vulnerable to being circumvented through identity theft, as bad actors can attempt to contact the mobile service provider pretending they are the SIM-card holders.
| Read also: On-Premise 2FA vs Cloud-Based Authentication
3. Remember That Multifactor Authentication Must Be as Easy for Users as Possible
One of the best ways to make your multifactor authentication as user-friendly as possible is to choose between multifactor authentication vendors who offer adaptive authentication options. Adaptive authentication will assess the risk of a breach each time a user goes through the authorization process and will act accordingly depending on a predefined set of rules that applies to the user of this particular group.
In other words, adaptive authentication means analyzing the user’s environment (browser name and version, operating system and language, window size and screen resolution, color depth, presence or absence of Java, plugins, etc.) and asking an OTP code only if an established mismatch threshold has been exceeded.
This solution becomes more precise the longer you use it as it builds the database of safe profiles and environments for your users to compare against any future login attempt. This feature adds flexibility and lowers obtrusiveness if compared with the regular MFA solution without the adaptive authentication feature.
4. Find the Best 2FA Provider
All other things settled, you still need to choose the right multiple factor authentication provider to implement the solution that suits you. So, what things should you be on the lookout for?
- Obviously, the MFA provider must be able to work within the boundaries of the exact solution you need for your specific situation.
- The solution must not be too complex, as complex implementations usually earn the ire both of your IT department and your end-users.
- It should be affordable, stable, and work as advertised.
Your best bet is to choose something that integrates easily into your existing IT framework. Undemanding and simple solutions give you more time to actually react and mitigate the threats you’d encounter.
Being the top solution for any of your MFA necessities, Protectimus can offer any MFA technology that you might need for your business. Protectimus is also fully prepared to take on custom requests regarding MFA, and will help to integrate your chosen 2FA into your particular infrastructure, however intricate or straightforward it might be.
| Read also: Two-Factor Authentication Solutions Comparison: Google Authenticator vs. Protectimus
5. Explain Multifactor Authentication to Its End Users
Even the best defense falls flat if people don’t realize (or don’t care) how to use it. Take care to explain your multi-factor security system to everyone who’d use it one way or another. If it’s your employee, make a point about how the data they are working with is made into a product you are working with. Make an additional point on how losing the data equals losing the product, equals losing the profit.
If you are using MFA with your clients, your best bet is to make it as unobtrusive as possible, and also to give away some sort of minor encouragement (for example, limited access to some premium feature) to any user who’d voluntarily apply to use it.
But the most important thing to realize is that MFA exists only to protect your business and personal or confidential data you store. Knowing without a doubt that it’s not a liability but a boon for your company will help you to make the right decision and start looking for an effective solution — today.
Read more:
- Two-factor authentication for Windows 7, 8, 10
- How to Add Two-Factor Authentication to Outlook Web App (OWA)
- Active Directory Two-Factor Authentication
- Best Protectimus MFA Features for Financial Services Cybersecurity
- Why US, Canadian, and EU Universities Choose Programmable Hardware OTP Tokens
- 4 Reasons Two-Factor Authentication Isn’t a Panacea
- 2FA Security Flaws You Should Know About
- Remote Work: Dream or a Threat?
Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from our team.


Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from Protectimus blog.
You have successfully subscribed!