The basic idea behind any type of multi-factor authentication is communication between an MFA device and a server. An MFA server can be set up either on-premise (locally within your company’s infrastructure) or in a cloud. Both approaches have their pros and cons. In this post, we aim to give you a comprehensive comparison of cloud multi-factor authentication vs on-premise 2FA solutions to help you choose the best 2-factor authentication for your business.
How 2-Factor Authentication Works
Unlike single-factor authentication, which requires only a passcode, multi-factor authentication requires two, or all three of the next determinants:
- Something you know, which is your user password;
- Something you possess, which is your MFA security device or token;
- Something you are, or your biometrics for TouchID, FaceID, and the like.
For MFA authentication to validate the user’s identity, the user’s token and multi-factor authentication server are required to share a secret key. So, any OATH 2FA authentication will work like this:
- The server and the user share a secret seed.
- The user logs in the application or website protected with MFA and enters the user login credentials.
- What happens next rests on the 2FA algorithm used. Either the user’s token mixes its secret key with the running time (TOTP), or with a counter (HOTP), or utilizes the challenge/response algorithm (OCRA). The token then provides the end-user with an OTP to enter on the protected website.
- The server goes through the same key+counter/time/challenge process and compares both values. If the values received from the token and the server are the same, the user is granted access.
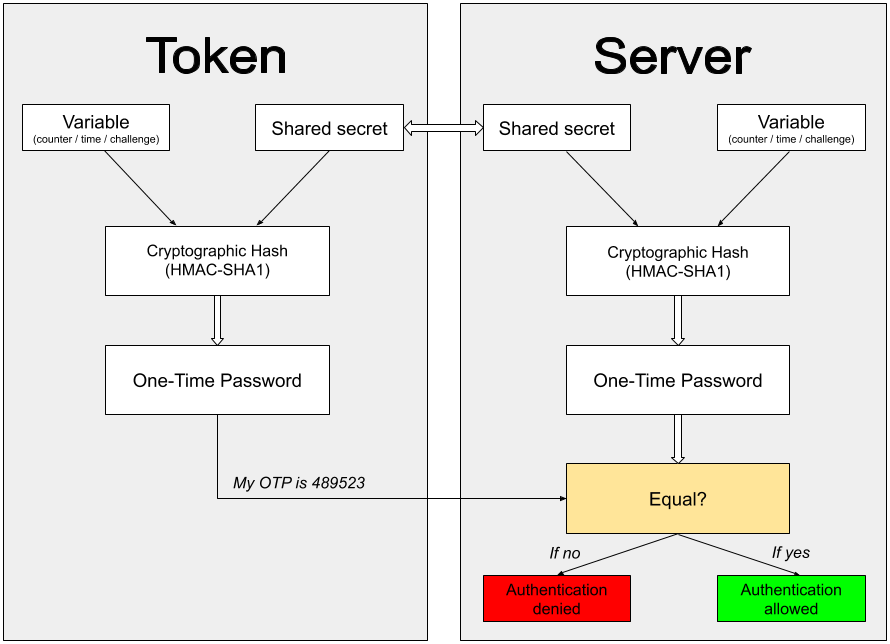
And, as we’ve already established, a two-factor authentication vendor can set up an MFA server either in the cloud or locally in the client’s environment. Now let’s look closer into cloud vs on-premise multi authentication.
| Read also: Two-Factor Authentication Solutions Comparison: Google Authenticator vs. Protectimus
On-Premise 2FA Pros and Cons
Most 2-factor authentication providers offer on-premise solutions to those clients who need full control over all their systems and operations and have rigorous security policies. Local multi-factor authentication software installation allows the utmost protection for your server and your users. An on-premise 2FA server does not require any connection to the Internet and other outside networks, thus you can set it up on an isolated network.

With on-premise 2FA not only do you have the fullest control over the system’s operations, databases, and all the sensitive data, you also have full knowledge of the platform’s equipment. This gives you many advantages, starting with the confidence in the system’s efficiency, and ending with the ability to quickly fix any issues if they occur.
Naturally, local MFA setup comes with all the reporting tools you might require, including those for gathering stats, managing users and secret keys, etc. And if you need any custom features Protectimus team can add them for you.
We can not say for every 2FA provider on the market, but the Protectimus On-premise Platform is very versatile. The platform runs on any major operating system like Windows, Linux, FreeBSD, etc. And it supports Google Chrome, Mozilla Firefox, Internet Explorer. We comply with every industry standard and uphold all the major OTP algorithms (HMAC, HOTP, TOTP, OCRA).
Of course, there are drawbacks. You will have to spend quite a lot of time, money, and effort to set up the environment for an on-premise 2FA server. You will then have to maintain it, which requires time and qualified human resources.
| Read also: Active Directory Two-Factor Authentication with Protectimus DSPA
Cloud-Based Two Factor Authentication Pros and Cons
For a smaller sized business, there are a lot of pros in cloud-based authentication solutions. Cloud authentication service, often referred to as SAAS authentication, does not require quite as many resources as an on-premise multifactor authentication service. You do not have to set up an environment for it, get expensive equipment, and hire experienced personnel to maintain it all. A cloud service MFA server component is ready to use out of the box.

Two-factor authentication SAAS is fast, modern, and convenient. The integration cloud service from Protectimus offers is very quick and painless, all you need to do is register and start the integration.
Another plus to cloud MFA is the cost of the service itself, you pay only for the things you actually use. Protectimus two-factor authentication cloud service can be deactivated at any time. You can also modify the service plan whenever you find it necessary.
As with the on-premise solution our cloud two-factor authentication service comes with all the tools you will need for reporting, monitoring, and managing.
Of course, as with everything else, there are downsides. You have to be absolutely sure about your cloud service provider. If your business has government security regulations to consider, cloud might not be within those regulations. You do not have any control of the equipment, downtime, and other unforeseen issues. We at Protectimus do everything to make sure our SAAS authentication and authorization service runs 24/7 with no hiccups, but no one is completely immune.
| Read also: Duo Security vs Protectimus
Conclusions
Both on-premise and SAAS MFA server solutions are easy to integrate, both support every 2FA algorithm and all types of tokens, both options are secure. So how do you choose which one to go for?
Consider the size of your company, the resources you are ready to part with, the amount of control you require, and the customizations you might need.
| Cloud-based authentication service | Local MFA server |
|---|---|
| Cost-effective. With cloud service, you pay only for the options you use. Up to 10 tokens for one resource is free. | Customizable. If you need any specific features or security measures we are ready to add them for you. |
| Ready-to-use. There is no need to set up an environment for the MFA server. | Full control. Everything is set up on your own equipment, you have the fullest control of all operations and sensitive data. |
| Quick integration. Implementing 2FA for your resource takes mere minutes. | Quick integration. The integration is as fast as with the SAAS solution. |
| Supports all MFA algorithms and tokens. | Supports all MFA algorithms and tokens. |
| Additional security. The on-premise platform can be installed in an isolated network. You can add firewalls or other additional security features. |
What Else to Read
- How to Add Two-Factor Authentication to Outlook Web App (OWA)
- Remote Work: How to Transition Team to Working From Home During the COVID-19 Pandemic
- Best Protectimus MFA Features for Financial Services Cybersecurity
- 2FA Chatbots vs. SMS Authentication
- 2FA Security Flaws You Should Know About
- Time Drift in TOTP Hardware Tokens Explained and Solved
- Two-factor authentication for Windows 7, 8, 10
- Office 365 MFA Hardware Token
- Hardware Tokens for Azure MFA
Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from our team.

Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from Protectimus blog.
You have successfully subscribed!