Providing our services, we often highlight that Protectimus is a coordinate partner of the OATH Initiative and that all our tokens and two-factor authentication software are OATH-certified. Not everybody is aware, however, of what the Initiative for Open Authentication (OATH) is and what its major goals are. That’s why we decided to clarify all the details concerning the OATH definition – its tasks, algorithms, and overall contribution to open authentication which is so important and useful today.
Table of contents:
- What is OATH?
- The Major Goals of the OATH Initiative
- OATH Authentication Algorithms
- The Efficiency & Importance of OATH Open Authentication
What is OATH?
In a nutshell, OATH – Initiative for Open Authentication – promotes the industry-wide implementation of strong authentication based on a single reference architecture that is developed jointly by the industry leaders using open standards.
This will allow establishing strong authentication as a highly-available standard supported by any device in any network. In the long run, the Initiative can help significantly reinforce the security of users and service providers worldwide.
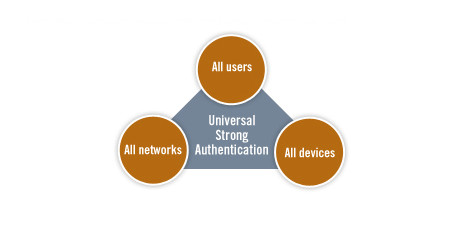
What is OATH-certified? OATH certification, basically, means supporting the Initiative’s standards and creating cybersecurity solutions on the basis of these standards. Protectimus, for instance, offers a two-factor authentication solution that is fundamentally based on the principles of open authentication and uses the OATH authentication algorithm HOTP, TOTP, and OCRA.
Now that we got the basic OATH meaning figured out, let’s discuss its major goals.
| Read also: Identification, authentication, and authorization – what’s the difference
The Major Goals of the OATH Initiative
Being essentially a collaborative effort in advancing modern authentication principles and making them more secure and reliable, the Initiative for Open Authentication makes the whole process more cost-efficient and transparent. It simply makes two-factor authentication open-source.
Any company can build its custom 2-factor authentication system based on a single standard that is highly reliable and backed up by the leading companies in the industry.
The major goals of the Initiative can be listed as follows:
- making online transactions safer and more secure for both users and service providers through implementing two-factor authentication;
- enhancing the common security standards with a collaborative-based, open-source strong authentication standard;
- lowering the costs and efforts required for integrating strong authentication in user systems;
- making authentication devices such as OATH tokens, smart cards, etc. more common and accessible;
- turning existing mobile devices such as tablets, laptops, and smartphones into OATH software tokens;
- advocating the distribution of OATH two-factor authentication algorithms and software throughout numerous network endpoints, like Wi-Fi hotspots, servers, connected hardware, network switches, etc.
| Read also: The Pros and Cons of Different Two-Factor Authentication Types and Methods
OATH Authentication Algorithms
Based on its universal goal of standardizing strong authentication, which includes the establishment of protocols, algorithms, and data/input formats of a single standard, OATH authentication requires the underlying “pushing” powers.
The collaborative efforts thus spawned three fundamental RFCs (Request for Comments) that describe the respective algorithms for one-time password generation:
- RFC4226 for the event-based HOTP algorithm;
- RFC6238 for the time-based TOTP algorithm;
- RFC6287 for the challenge-response OCRA algorithm.
OATH HOTP
HOTP (HMAC based one-time password algorithm) is an algorithm aimed at generating one-time passwords based on the mix of a secret key (a shared value) with a counter (variable).
A secret key consists of a line of symbols that the authenticating server shares with the user device. A counter defines the event of the OTP generation and the number of these events increases with every new OTP created. This accumulation of events serves as a convenient variable in the algorithm.
The algorithm processes a secret key and a counter, hashes them, and truncates the result into a 6-8 character one-time password which is displayed on your HOTP OATH token screen.
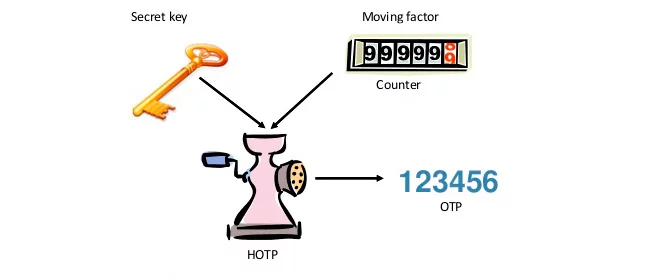
The event-based nature of the algorithm means that:
- you can request the OTP at any time without waiting;
- you can use it at any time (now or later) once it’s generated;
- the protection from the replay attack is already realized through constantly increasing counter;
- one of the OATH security nuances with HOTP algorithm is that phishing software can easily get a hold of HOTP one-time passwords by collecting them, since they can be used long after their initial generation.
| Read also: HOTP Algorithm Explained
OATH TOTP
The TOTP algorithm (Time-based One-Time Password Algorithm) is pretty much identical to the above, with the essential difference in that it uses a running time interval as a variable instead of the counter. Thus, it mixes a secret key with a current time interval, which means that the server and token time must match.
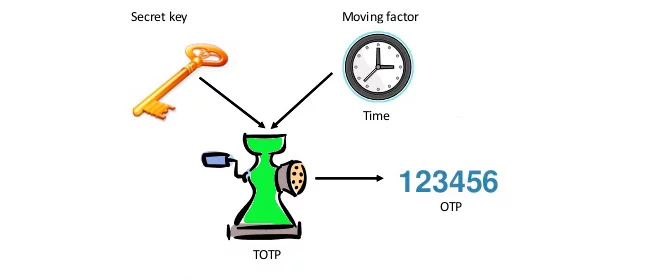
The time-based nature of the OATH TOTP algorithm means that:
- it can only be used within a certain time frame, usually 30-60 seconds (unlike the HOTP algorithm);
- you can only generate one OTP in the set time interval;
- it’s much harder to phish the TOTP one-time password since the OTP can only be used within a certain period of time, after which it becomes obsolete;
- it requires server-side protection from the replay attacks that would restrict authentication with the same one-time code within the same time interval.
| Read also: TOTP Algorithm Explained
OATH OCRA
The OCRA algorithm (OATH Challenge-Response Algorithm) generates one-time codes based on a secret key and a certain challenge received from the server (this is a variable). Also, a combination of the time interval and challenge can be used as a variable in OCRA.
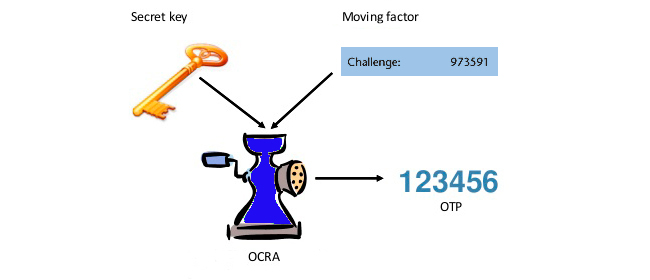
OCRA algorithm allows using data signing like Confirm What You See (CWYS) feature to reinforce the OATH security and the payments’ security in particular. The CWYS function allows using definite parameters, like the amount of transaction, user’s current balance, the currency, etc. as a variable in the OCRA algorithm for the further creation and verification of one-time passwords.
Such one-time codes are valid only for the operations whose data were used as a variable. Thus, if the hacker intercepts the one-time code, they won’t be able to use this code for their own fake operation. This grants even greater reliability of the OCRA algorithm, which means that it should be used in the areas that require the strongest protection.
The time and event-based nature of this algorithm is kind of a combination of all the goods HOTP and TOTP provide, namely:
- you can only use the generated OTP within a certain interval of time;
- you can request the OTP at any time without waiting;
- the limited use time of the OTP makes it harder to phish;
- using unique data as a challenge provides replay protection;
- Using OCRA algorithm and data signing you’ll definitely protect users from all kinds of phishing, man-in-the-middle attacks, as well as some banking Trojans, injections, data spoofing, and replacement attacks.
| Read also: OCRA Algorithm Explained
The Efficiency & Importance of OATH Open Authentication
In terms of overall access security, OATH provides some truly outstanding two-factor authentication algorithms that are easy to access, affordable, and multipurpose. These algorithms are well-tried-and-tested by industry experts and are open-source so that their inspection for flaws and errors can be carried out transparently by the specialized companies.
Ultimately, OATH cybersecurity can never be a black box implementation (unlike closed-source and vendor-provided solutions) and offers some highly-efficient protection from brute force, keyloggers, phishing, pharming, man-in-the-middle attacks, DNS cache poisoning attacks, trojans attacks, man-in-the-phone attacks, browser poisoning attacks.
Read more:
- Active Directory Two-Factor Authentication
- Two-factor authentication for Windows 7, 8, 10
- Hardware Tokens for Azure MFA
- Office 365 MFA Hardware Token
- Electronic Visit Verification with Hardware OATH Tokens
- Programmable TOTP Tokens Protectimus Slim NFC: FAQ
- 2FA Chatbots vs. SMS Authentication
- 2FA Security Flaws You Should Know About
- How to Backup Google Authenticator or Transfer It to a New Phone
- Best Protectimus MFA Features for Financial Services Cybersecurity
Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from our team.

Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from Protectimus blog.
You have successfully subscribed!