LDAP helps organizations manage access to critical systems, but passwords alone aren’t enough to keep attackers out. Adding multi-factor authentication (MFA) to LDAP can significantly boost security. This article explains what LDAP is, the difference between the LDAP protocol and servers, and how to smartly integrate the Protectimus MFA solution for LDAP to provide stronger protection.
LDAP: What Is It?
LDAP stands for Lightweight Directory Access Protocol. This standard protocol is widely used by organizations to manage user accounts and access directory servers. LDAP facilitates communication between a Service Provider and an Identity Provider, performing tasks such as user authentication, permission management, and directory updates across a network.
Organizations value LDAP for its speed, scalability, and ease of use, relying on on-premises LDAP servers, such as Microsoft Active Directory and OpenLDAP, to run their critical business applications. When a user attempts to log in, LDAP verifies whether the authentication is successful. This makes securing LDAP with MFA essential for any business.
LDAP Protocol vs. LDAP Server: Key Differences
LDAP protocol is a tool designed for accessing and managing information in user directories. It reads and updates data stored in user directories. Meanwhile, an LDAP server refers to any server functioning as a user directory service (e.g., Active Directory, OpenLDAP, Red Hat Directory Server, IBM Security Directory Server, Novell eDirectory, Apache Directory Server, etc.).
Why Add Multi-Factor Authentication to LDAP?
LDAP servers store and organize critical information, such as user credentials and permissions. The LDAP protocol is responsible for managing user accounts and accessing the LDAP servers with critical information. Protecting user credentials and controlling access to user accounts remain key priorities in today’s cybersecurity.
Cybersecurity specialists often secure LDAP connections by wrapping the LDAP protocol in TLS/SSL (which is then called LDAPS). However, this is not enough. Multi-factor authentication (MFA), also known as two-factor authentication (2FA), is the best way to ensure that LDAP authentication is protected from any attacks aimed at compromising user accounts.
Multi-factor authentication is a must for any corporate network protection. With MFA, you add another layer of protection to password-based authentication, which almost eliminates the possibility of corporate accounts being hacked and perfectly secures user accounts from phishing, keylogging, social engineering, man-in-the-middle attacks, brute force, credential stuffing, and other similar attacks.
One more reason to add MFA for LDAP is to meet the PCI DSS, GDPR, and other similar regulations’ requirements.
How Protectimus MFA Integration with LDAP Works?
Protectimus multi-factor authentication can be integrated into your LDAP-based infrastructure in several ways. We provide an open RESTful API, SDKs, and a wide range of ready-to-use plugins for virtually any software, operating system, VPN, or VDI service that requires MFA protection within a corporate environment.
However, the easiest and most convenient solution for LDAP MFA is Protectimus DSPA (Dynamic Strong Password Authentication). It enables seamless integration of multi-factor authentication directly with an LDAP server, adding MFA to all entry points that rely on the LDAP server for authentication in a single step. Alternatively, the admin can choose to enable multi-factor authentication for a specific group of users in LDAP, rather than applying MFA to all users.
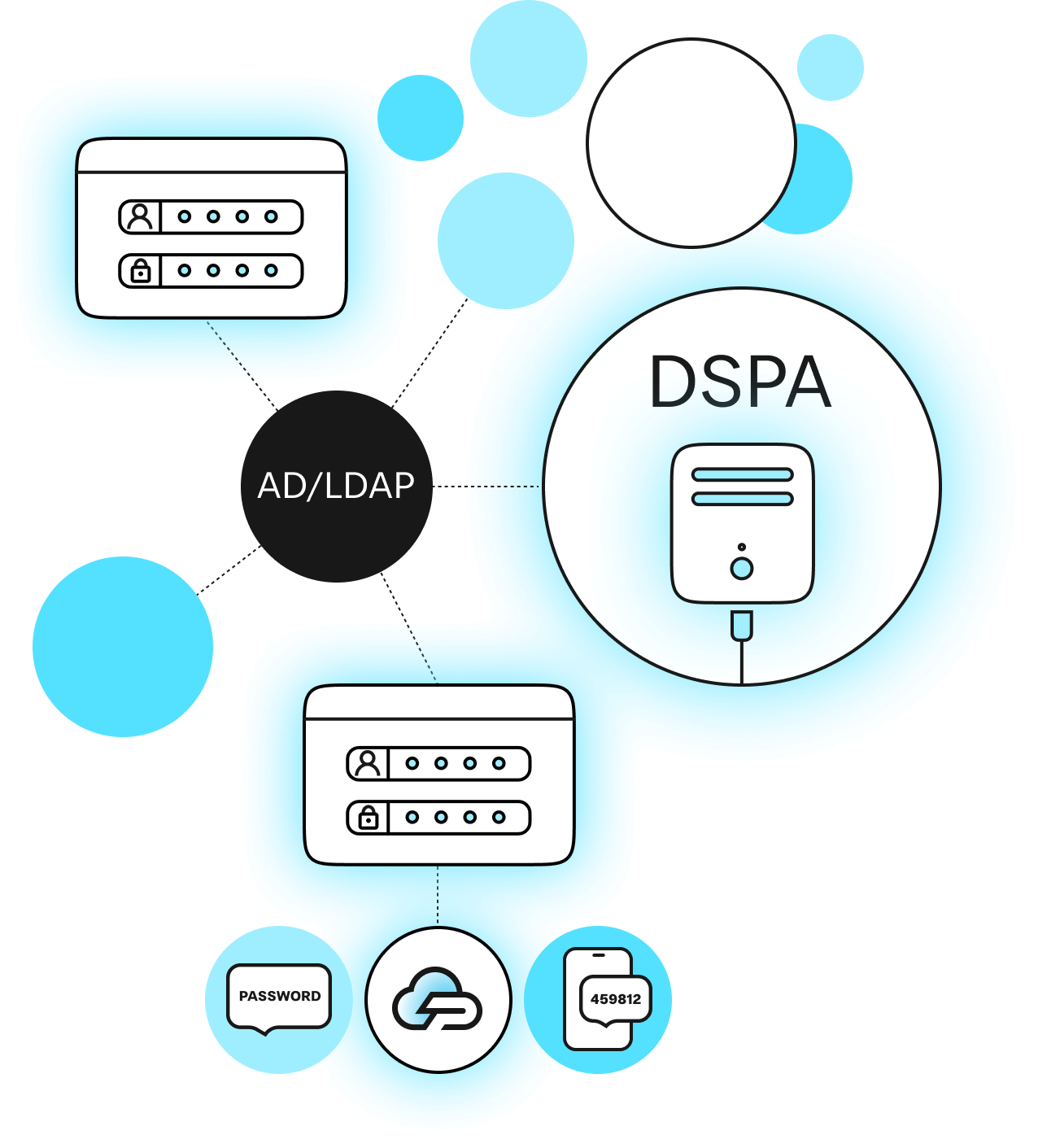
Here’s what LDAP MFA with Protectimus DSPA looks like:
You integrate the Protectimus On-Premise MFA platform with your LDAP server, which appends a six-digit one-time password (OTP) to users’ static passwords. This OTP is dynamically generated using the TOTP algorithm, ensuring it updates regularly.
For example, a password that was previously P@ssw0rd! will now become P@ssw0rd!459812, where P@ssw0rd! remains the static portion and 459812 is the time-sensitive OTP.
The administrator sets the OTP update interval, usually every 30 seconds or a multiple of that. The DSPA component ensures the six-digit OTP portion of user passwords is automatically updated according to the configured schedule, while the static password remains unchanged.
This process makes authentication both secure and user-friendly: users simply enter their static password followed by the OTP in one step. To generate OTPs, they can use the free Protectimus SMART MFA app, available for both iOS and Android.
Below, you’ll find an approximate schematic of how this LDAP MFA integration works.
Read also: Two-factor authentication for Windows 7, 8, 10
Benefits of This Approach to LDAP Two-Factor Authentication
1. Enhanced LDAP Security.
Traditional two-factor authentication setups typically secure only specific endpoints, leaving vulnerabilities that attackers can exploit. For instance, if a hacker gains access to a user’s credentials (username and password), they can interact directly with the LDAP server, often part of the Active Directory ecosystem, using tools like the Windows command prompt. In such cases, conventional 2FA measures won’t prevent unauthorized access to the directory.
Protectimus provides a robust solution by enabling multi-factor authentication for the entire LDAP infrastructure. With this approach, access to the LDAP server requires a dynamically generated one-time password (OTP), adding a critical layer of security.
2. Simplified Management for LDAP Administrators
Managing multiple MFA solutions across various accounts, services, and platforms can be a complex and time-consuming task. Administrators often need to implement separate MFA tools for different services, install additional software on user devices, and ensure regular updates.
Protectimus DSPA simplifies this process by integrating seamlessly with the LDAP server. This integration extends OTP-based protection to all services and platforms that authenticate through LDAP, creating a unified security framework. This not only bolsters overall security but also significantly reduces the administrative workload associated with managing multiple MFA systems.
| Read also: 2FA Security Flaws You Should Know About
How to Integrate Protectimus DSPA MFA with LDAP
Integrating the Protectimus platform with your LDAP server is a straightforward process. Follow these steps to configure Protectimus DSPA (Dynamic Strong Password Authentication) for enhanced LDAP security:
- Install Protectimus on-premise platform and the DSPA component.
Contact us via [email protected] to request the platform with the DSPA component for download.
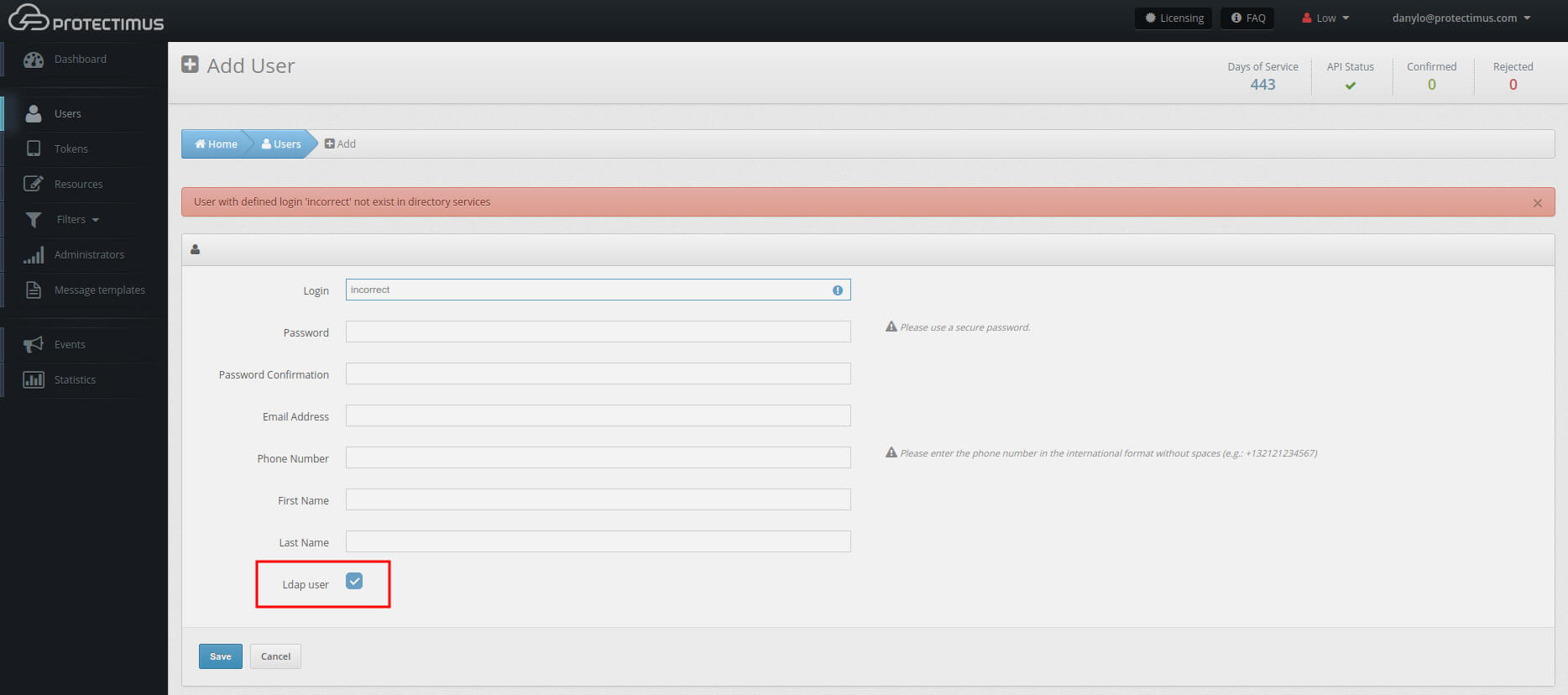
- Add users.
Make sure to check the LDAP User checkbox at the bottom. The user Login used here must match the Common Name in AD. It’s also required to specify the Email Address for each user.

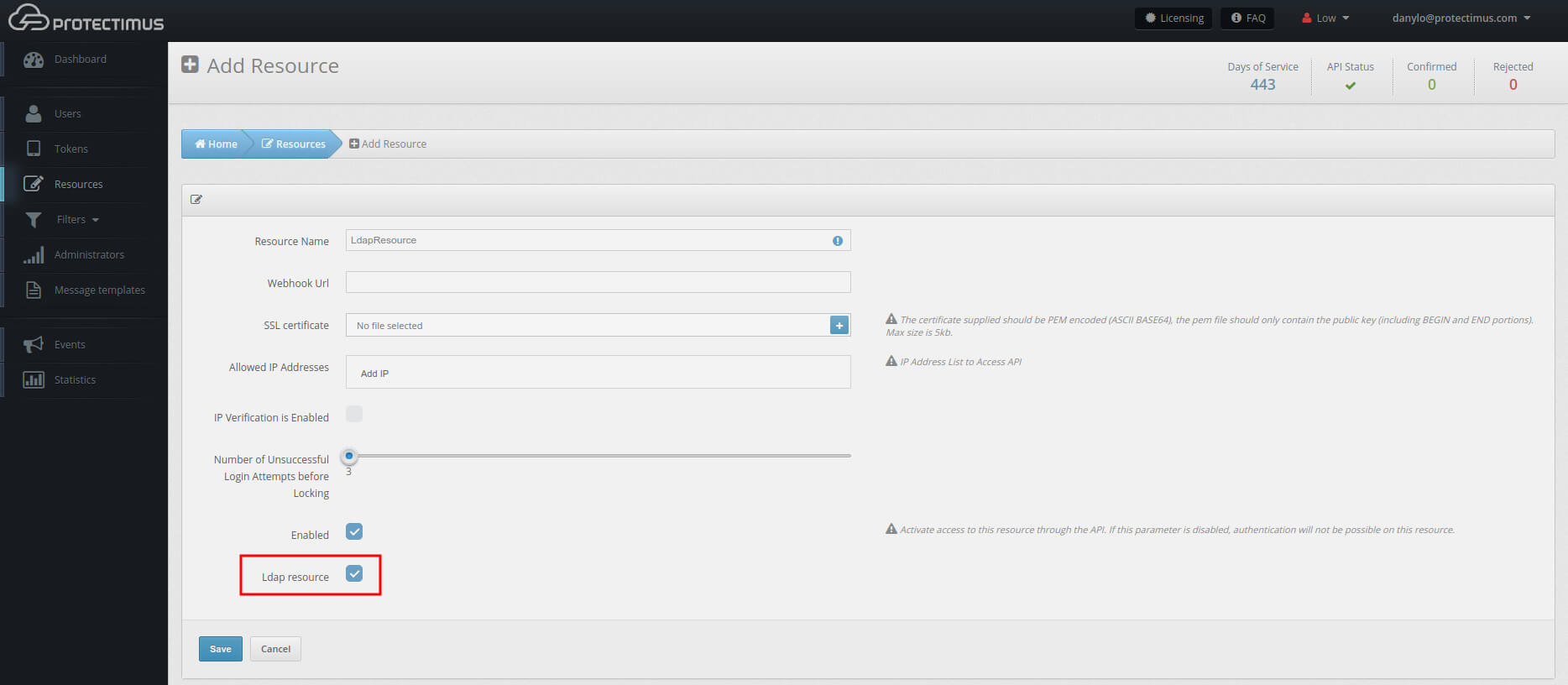
- Create a resource.
Here too, make sure to check the LDAP checkbox at the bottom.

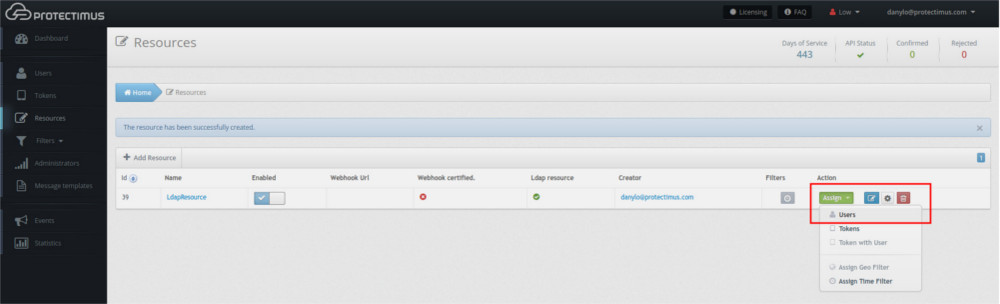
- Assign Users to the Resource.

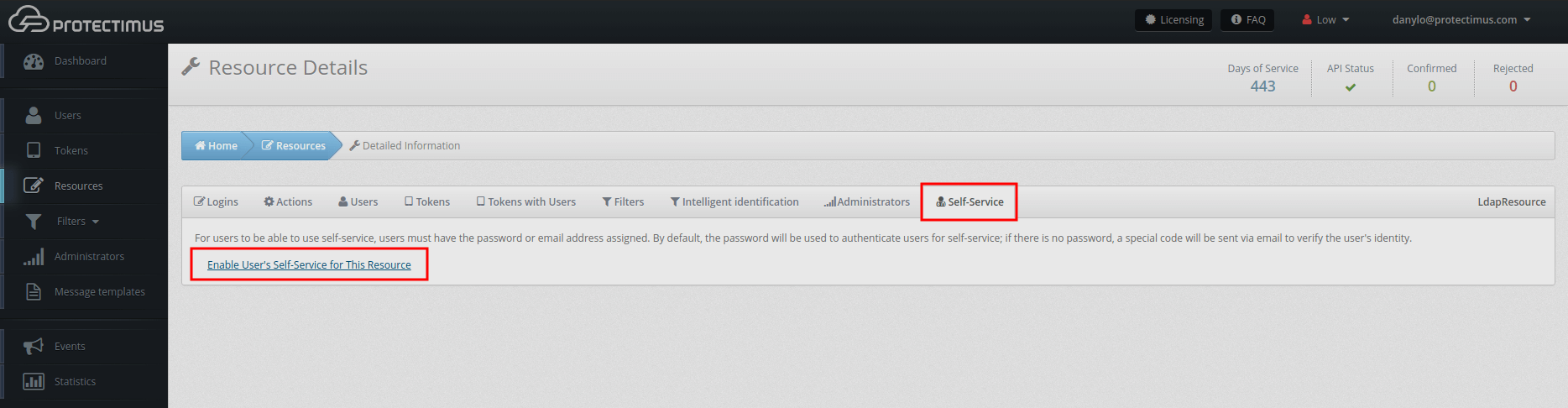
- Activate Self-Service.
Clicking on the resource name you created. Go to the Self-Service tab and click “Enable User’s Self-Service for This Resource”.You will be asked to specify the part of the address at which the Self-Service will be available to your users? For example, if you enter “protectimus”, your Self-Service address will be https://service.protectimus.com/selfservice/protectimus

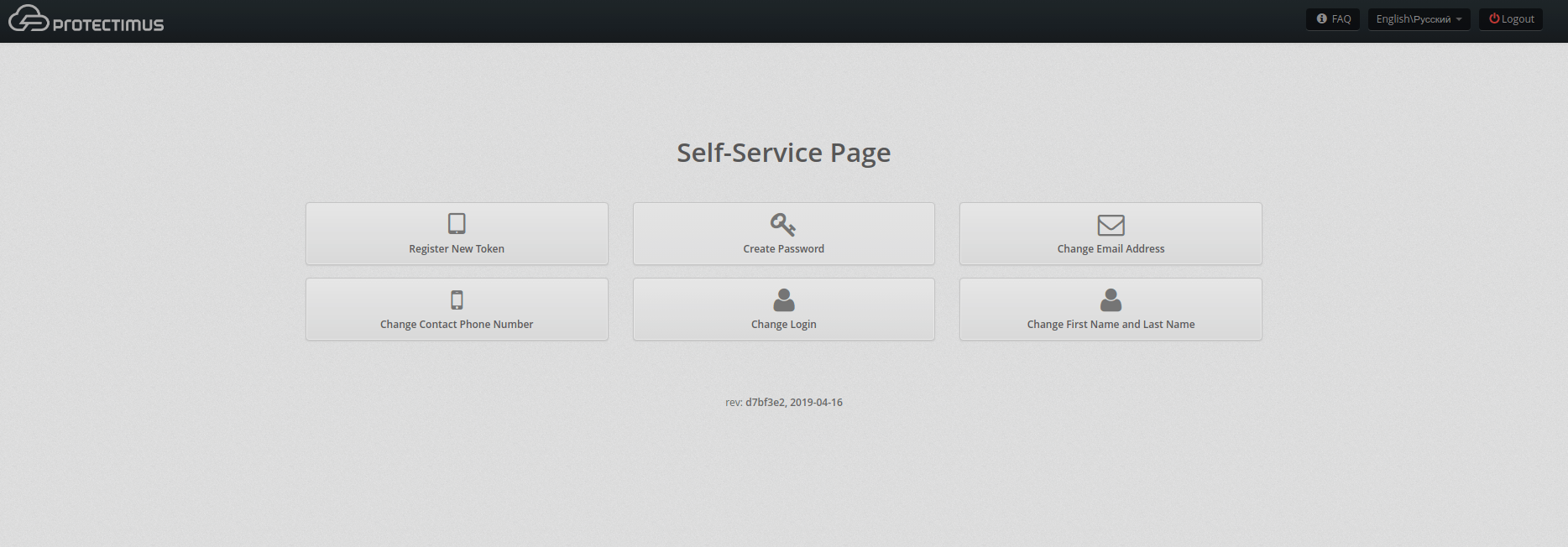
- Give this link to your users to create tokens and static passwords.
Users will need to login to the self-service page using their Logins (CN) from step 2 and the OTPs that will be sent to emails you also specified in step 2.
On the Self-Service page, the users will be asked to Register New Token (the administrator should inform the user what time step to set up) and to Create a Password (the password must match their AD static password).
By following these steps, you’ll successfully integrate Protectimus with your LDAP infrastructure, providing robust multi-factor authentication across all LDAP-dependent services.
| Read also: Detailed Protectimus DSPA integration guide
FAQ on Integrating Protectimus MFA with LDAP
How much does it cost?
The pricing depends on the number of users. The minimum cost starts at $199 for up to 99 users.
What do I need to start testing?
To begin testing, you’ll need to install the Protectimus MFA platform and integrate it with your LDAP server. The minimum technical requirements include:
- Java Development Kit (JDK): Version 8 or higher.
- PostgreSQL Database Management System (DBMS): Version 10 or later.
For the installation package and step-by-step instructions, contact us at [email protected].
Does it work only with LDAP, or can it integrate with other databases?
Protectimus DSPA supports two-factor authentication integration not only with LDAP but also with any other databases and user directories.
Leverage Protectimus DSPA to ensure robust security across your LDAP infrastructure and beyond. For more details, contact us at [email protected].
Read more:
- Protectimus MFA Prices: How to Save with Coupons, Discounts, Referrals, and Subscriptions
- Protectimus Customer Stories: 2FA for DXC Technology
- Protectimus Customer Stories: 2FA for Advcash
- Protectimus Customer Stories: 2FA for SICIM
- Time Drift in TOTP Hardware Tokens Explained and Solved
- Keycloak Multi-Factor Authentication With Hardware Tokens
- Sophos 2FA with Hardware OTP Tokens
Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from our team.

Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from Protectimus blog.
You have successfully subscribed!