It’s hard to imagine the modern rhythm of everyday life without gadgets, to which we are so accustomed. The first computer could perform only a limited number of functions. Its length was about 17 meters, the height of more than 2.5 meters, it weighed 4.5 tons and covered an area of several dozen square meters. Half a century later multifunctional gadgets became a thousand times smaller in size and instantly perform tasks that the original creators of computers could not even imagine possible.
Twenty years ago, mobile phones were introduced on store shelves for the first time, and now this device/gadget has become an inseparable part of everyday life. Recently, the era of smartphones began and turned mobile phones in the so-called mini-computers, the use of which makes possible to open the car, unlock the doors and carry out contactless payments without any additional devices.
Smartphone – a gadget that replaced computers
For example, branded smartphones authorized by MasterCard for NFC-payments MTS 965 give owners the opportunity to make payments by simply holding the phone to the payment terminal which supports the technology of wireless payments MasterCard PayPass. Only if one wants to buy expensive goods, a PIN code is required.
Modern technologies allow the usage of smartphones for such important tasks as two-factor authentication, turning them into full-fledged tokens. A striking example is a free app for smartphones Protectimus SMART, which is available for iOS and Android platforms, and was created to protect accounts on the Internet websites. The app makes possible to select the algorithm for generating and creating multiple OTP tokens on one device and supports data signing function CWYS (Confirm What You See), which allows protecting the payments from the latest hacker attacks such as replacement, Automated Transfer System, data modification.
However, while all the forces were thrown to the technological progress chase, little attention is paid to the critical issue of the universal mobile devices protection from unauthorized access. But if you do not take care of protecting your smartphone from unauthorized access, you can lose a lot – from the money in the bank account to personal photographs and correspondence.
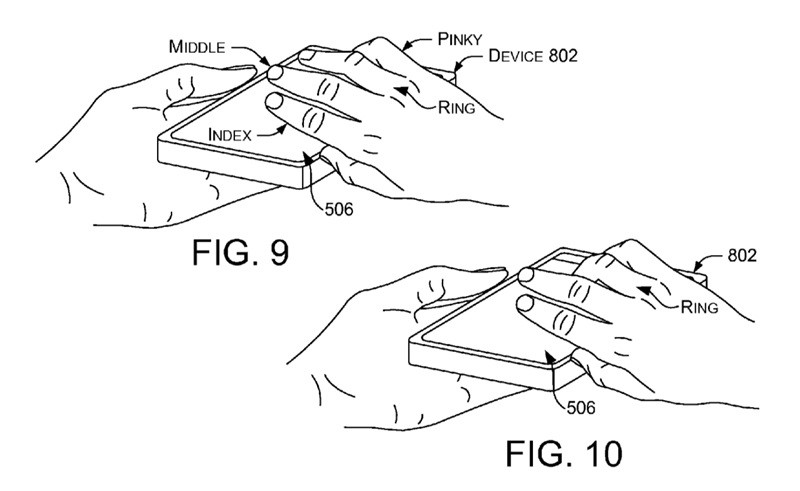
Authentication through fingers gestures
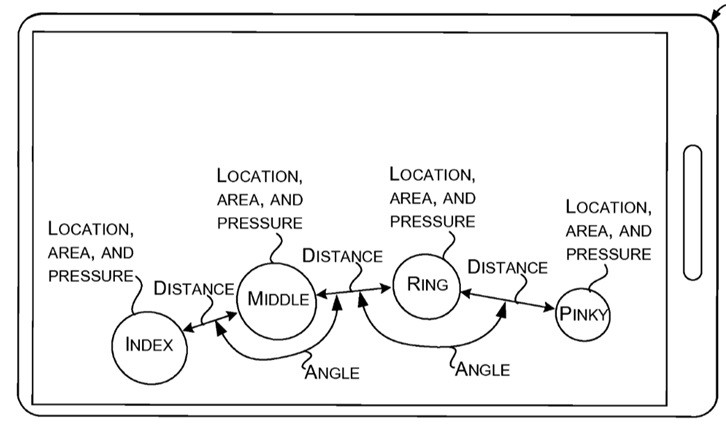
In August 2015, Microsoft patented a new system for the authentication on electronic gadgets with touch screens through the gestures of four fingers (except the thumb) or, in other words, gesture-based authentication. To be more precise, the authorization of users would be hold with the help of secret gesture which is stored in the device memory. While making it, the system detects a number of different factors: duration of touching the screen, the force of pressing, the size of the contact area with a display, the length and arrangement of the fingers, the angles between them, and other biometric data of the person. During re-authorization, the system correlates the data with the stored user’s unique digital pattern of a gesture and allows or denies the access to the device. Microsoft claims that this technology can be used for any device, such as mobile phone, TV with the touch screen, etc.
This authentication system can prove itself a reliable armor for touchscreen phones, and bundled with the app for smartphones Protectimus SMART – to minimize the risk of compromising your device to protect personal information and restrict access to your money.
Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from our team.

Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from Protectimus blog.
You have successfully subscribed!