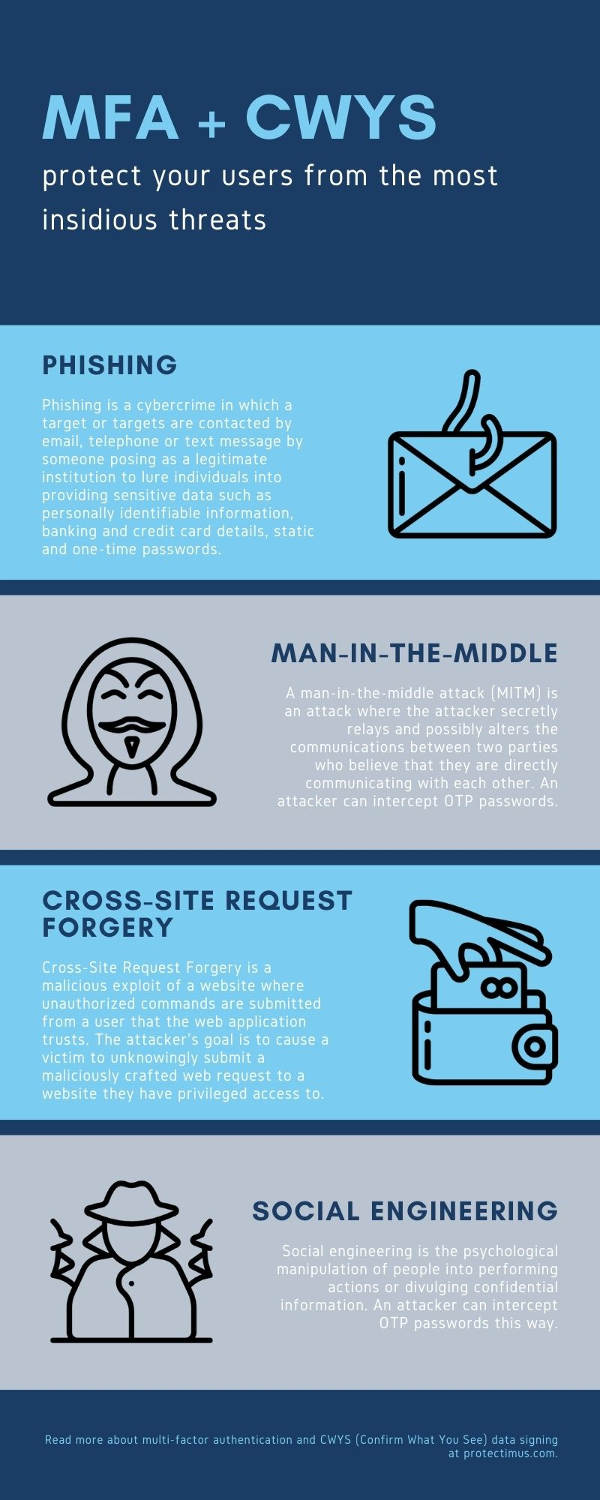
MFA or multi-factor authentication by definition is a technology that limits access to a user account unless the user presents two or more pieces of evidence that prove that they are who they claim to be, moreover, the evidence must be of different natures: something they know, something they have or something they are. Overall, the process is regarded as helpful, as it is a solution to many security threats including phishing, brute force, keyloggers, some cases of social engineering and MITM attacks. However, some persistent MFA myths make companies hesitant to use it, and we’re ready to debunk some of the most common ones.
1. Only large companies benefit from using MFA
This misconception doesn’t make sense if you think about it. The size of the company should have nothing to do with the security measures it employs. Even small companies can acquire sensitive information that should be subject to comprehensive control and security.
Furthermore, a company doesn’t need to have a huge staff to implement multifactorial identification. There are two-factor authentication examples that are easy and cheap to carry out, monitor, and maintain. While the downsides of not using MFA authentication can be even more devastating for a small company, a security breach can result in a massive loss of reputation and trust.

2. MFA should only be required from privileged users
The idea behind this myth is that only privileged users have access to sensitive data, so they are the only ones that should be required to go through multi-factor authentication. However, this assumption is often wrong as, for example, every company employee has access to some confidential data.
A harmful side of this myth is that cybercriminals often use it to their advantage. They target non-privileged users with phishing techniques or other hacking methods. Then they can use the access gained to move around the corporate network and access private or valuable data with ease.
| Read also: Remote Work: How to Transition Team to Working From Home During the COVID-19 Pandemic
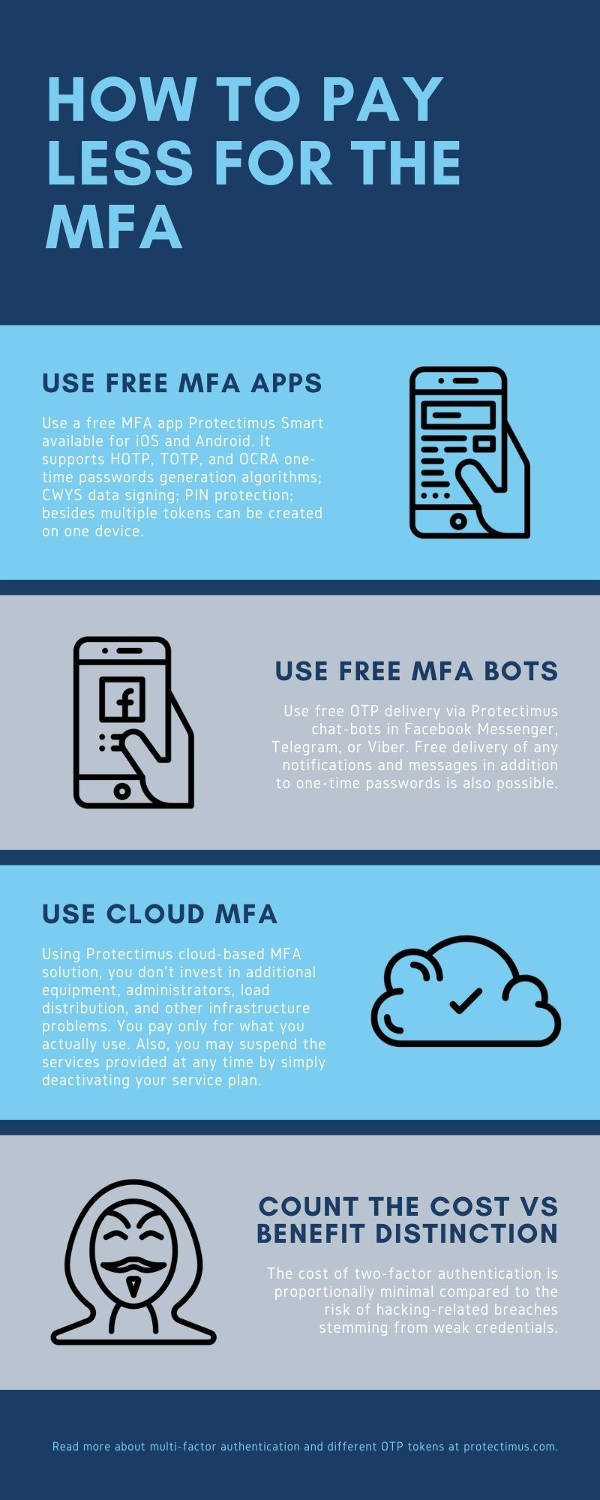
3. It is expensive to enable 2FA
This myth stems from the earlier days of 2-step verification when each hardware token cost was around $100, so while it was secure, it wasn’t cheap. Furthermore, they could be lost, rendering the process harder and even more expensive.
Nowadays, the price for hardware tokens Protectimus Two starts from USD 11,99 and goes down if the amount of order starts from 50 pieces. Moreover, there are much easier and cheaper ways of distributing one-time passwords. For example, it can be done for free through a dedicated authentication app or a chatbot in Telegram, Viber, or Facebook. Another thing to consider when calculating the price of MFA is how much you would lose without it in the case of a data breach.
4. Two-factor authentication ruins the user experience
Most companies work hard and spend a lot of money to make the user experience as smooth as possible. This is why it might seem annoying to them that just for the sake of implementation of multi-factor authentication solutions users would need to perform an extra task entering a one-time password. While this is true, two-step authentication is becoming more and more common, and users often expect to perform this extra step. Furthermore, you should remember that technology improves the user experience in terms of ensuring their data protection.
For example, one of the best solutions to this problem is intelligent identification. Often called user environment analysis or adaptive authentication, this technology improves the user experience by analyzing the browser version, operating system, and its parameters, window size, presence of certain plugins, and other parameters to identify the user. The two-factor authentication system requests one-time passwords only if the identification by these parameters is not successful. Protectimus MFA service offers adaptive authentication among its features.
| Read also: The Evolution of Two-Step Authentication
5. Multi-factor authentication is challenging to implement
As it is the case with any security measures, even the best MFA programs come with some implementation challenges. However, as technology continues to improve and develop, the implementation process becomes much easier.
For example, Protectimus provides a wide lineup of plugins that allow quick integration with just a few clicks. Among such plugins are those for Windows Logon and Microsoft RDP, OWA, ADFS, and Active Directory directly, RADIUS, Citrix NetScaler (ADC) and XenApp, RoundCube. The two-factor authentication service is available in-cloud and on-premises.
6. MFA is not a guaranteed safeguard
To be honest, no security solution provides 100% guaranteed safety against all types of security attacks. However, most two-factor authentication examples show that it is not worth time and resources for cybercriminals to break.
Furthermore, there are improvements to the MFA that make it even more impenetrable. For example, CWYS (Confirm What You See) data signing protects against many loopholes hackers use to get a one-time password. It uses data from users’ current operations to generate the OTP. This way even if the password is intercepted, the transaction made with it will be flagged as invalid.
However, if you’re still not convinced, you should remember that MFA is not the only security solution. Make it a part of your bigger safety system and employ other tactics for additional protection.
In conclusion
Multi-factor authentication is an advantageous way of securing your data. The myth and misconceptions concerning it should not stop you from applying it to your project. If you make a measured and informed decision, you will get a relatively simple, yet secure, cost-effective, and user-friendly system that will protect your data from cybercriminals. So, don’t put it off and provide confidence to your users.
Read more
- 2FA Security Flaws You Should Know About
- Time Drift in TOTP Hardware Tokens Explained and Solved
- Two-Factor Authentication Solutions Comparison: Google Authenticator vs. Protectimus
- The Pros and Cons of Different Two-Factor Authentication Types and Methods
- Active Directory Two-Factor Authentication
- Two-factor authentication for Windows 7, 8, 10
- How to Add Two-Factor Authentication to Outlook Web App (OWA)
- How to Backup Google Authenticator or Transfer It to a New Phone
Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from our team.

Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from Protectimus blog.
You have successfully subscribed!