Read on to learn:
- the keystroke logging definition,
- types of this malware you can come across,
- how keylogger software is spread,
- ways to check for keylogger
- ways to protect yourself from all the types of keyloggers and spyware.
Keylogger definition
Key logger, keystroke logger, also called system monitor, is a perfectly legal surveillance technology. When installed with your own hands on your own computer or smartphone, that is. Corporations commonly use this tool to track and troubleshoot tech issues and surreptitiously monitor their employees. Parents can use this software to monitor the ways their kids use the Internet too. There are known episodes when governments used the technology to collect and analyse info for crime solving.
So what is keystroke logging? As the name suggests, keylogging is a process of recording every key clicked on a keyboard (both desktop and mobile). Keystroke logging technology allows for gathering info on login credentials, web browsing, basically, everything that involves typing, and then sending the collected info, often encrypted, to a server, where it can be decrypted and read.
| Read also: How Does Brute Force Attack Work
Types of keyloggers
There are two ways to divide all the keyloggers into types. First one takes into consideration the way the recording is performed. With this approach all the keylogging can roughly be divided into the following types:
- Form-grabbing
- Memory-injection
- API-based
- Kernel-based
- Hypervisor-based
The second approach divides them into software and hardware ones, and it’s much easier to understand.
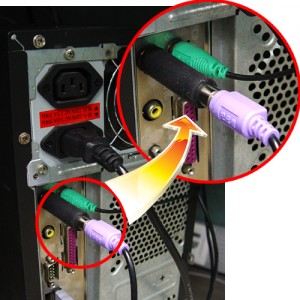
Hardware keyloggers
As the name suggests, hardware keyloggers are physical devices. These devices can be either inconspicuous looking plug-in types that are inserted into the keyboard port, or modules embedded into the keyboard or the internal computer hardware.
Either way, the criminals will have to gain access to the victim’s computer to plant the device. And to collect it to read the info later, since most of these devices do not transmit the gathered information back to the hackers.
Software keyloggers
Software keylogging is much easier to do. There’s no need to install a physical device, so no need to break into an actual office or home. All the criminals have to do is infect the victim’s computer, which is much easier done than you might think.
Unlike a lot of other malware, keylogging software is not harmful to the infected systems. Their whole point is to stay hidden, operate under the radar and silently and continuously send logs of every action done with the keyboard back to the hacker.
The most commonly used software keylogger is memory injection soft. This is essentially a Trojan virus altering the system memory to bypass security.
Another popular software records every form submitted online from the infected computer. So if you submit a form to create, say, a bank account, the hacker will know every piece of data you submitted.
| Read also: Social Engineering: What It Is and Why It Works
How keyloggers spread
Like any other virus, software keyloggers are spread online and can be sneakily installed without the victim ever noticing something amiss. The most common ways to get infected are described below:
- Phishing. Clicking on a link or opening an attachment from a phishing email.
- Visiting a malicious site. A keylogger is installed with a webpage script here.
- Trojan virus in the software you install. As we already mentioned above, the most typical method of infecting a computer with a keylogger is through a Trojan. As you might already know, a typical Trojan is disguised as some kind of useful utility. When a victim of the Trojan attack downloads the files and installs them, the malware is slipped on the system along with the utility the victim was actually looking for. In other instances, the actual utility is not there, the program the victim was looking for does not work, only the malware is installed. This last method is obviously not very effective for a keylogger.
Once the keystroke logging software is installed, it collects every keystroke made on the infected computer and a separate software sends the collected info to the hacker. Very rarely do the hackers get the data directly, if they do they are very easy to track. Most commonly, the data is encrypted and sent over to a public message board, where it can be downloaded anonymously by the hacker.
| Read also: Phishing, Vishing, Smishing, Pharming – What Is the Difference
Keylogger detection
Since keylogging technology is widely used legitimately, it is frequently overlooked by the anti-malware software, so a keylogger scanner or some kind of automated keylogger detector is not a very viable option.
Keylogger detection is not easy to do, keylogger viruses are meant to stay hidden after all. The best keylogger detectors are your eyes and common sense. If the browser is slower than you are used to, if you get errors on web pages load or images, if you stumble over keystrokes that get stuck or do not show up as you type, these are all signs that indicate that it’s time to try to detect keylogger.
How to check for keyloggers? The most obvious and straightforward way is to check the running processes in the Task Manager. Sure, there are obscure names on most of them, but you can always google the names you do not recognise, chances are, someone has already stumbled upon a keystroke logging software with the same name.
Remember that keylogging software is designed to be invisible, it stands to reason that you won’t find any keyloggers among the apps that run on the screen. So look into the processes running in the background and on start-up. It is a good idea to disable any programs you do not remember installing, just make sure to check the names for anything that might turn out to be essential for the system (google them all).
Another good place to check is the computer’s internet usage. You need to check for any suspicious programs that use the web. To do that go to the computer settings and find Data usage option in Network & Internet tab. Check the names of every unfamiliar program that sends data to the web.
Finally, check and disable every browser extension you do not remember installing or never use.
| Read also: Man In The Middle Attack Prevention And Detection
Keylogger protection
Keylogger protection starts with common sense. Always be suspicious of any attachments and emails from unknown senders. Never ever give your personal information to anyone unless there’s a good reason to. A virtual keyboard and password managers might be useful too since you won’t give the keyloggers anything to log.
But the most effective way is to use two-factor authentication whenever possible. This is the best keylogger protection software you can get, these one-time passwords are time-sensitive and will be no good for the hackers even if you do get infected with a keystroke logger.
Read more:
- The Pros and Cons of Different Two-Factor Authentication Types and Methods
- 10 Most Popular Two-Factor Authentication Apps Compared
- 10 Steps to Eliminate Digital Security Risks in Fintech Project
- Ransomware – to Pay or Not to Pay
- 9 Must-Follow Gmail Security Rules
- The Most Common Ways of Credit Card Fraud
- 10 Windows Computer Safety Tips
Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from our team.

Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from Protectimus blog.
You have successfully subscribed!