HOTP algorithm, or HMAC based one-time password algorithm, was first published by OATH as RFC 4226 back in 2005. What is OATH? OATH or Initiative for Open AuTHentication is an organization which specified, put together and published the OATH OTP algorithms that lie at the heart of MFA (multi-factor authentication). It is time we look closely at these algorithms, specifically — OATH-HOTP.
HOTP algorithm is what allows creating one-time passwords by utilizing a secret key and a counter. Today we will look at how OTP works, what role HMAC algorithm plays in it and look at both what is HOTP and TOTP.
A table of contents for your convenience:
- What does OTP mean
- What is HMAC
- What is HOTP
- HOTP synchronization problem
- HOTP security problem
- HOTP vs TOTP
- Protectimus tokens with HOTP algorithm
What does OTP mean
First, let’s discuss the OTP meaning. One time or one-time password is usually a string of randomly generated digits that works for one login or transaction only. These dynamic passwords, unlike the static ones, are hard to bypass or hack, since the hacker will need access to both something you have (OTP generating device, like cellphone or hardware token) and something you know (like pin code).
OTPs are the best protection against such common hacks as phishing, bruteforce, keyboard logging, man-in-the-middle attacks.
Here’s an OTP password example:
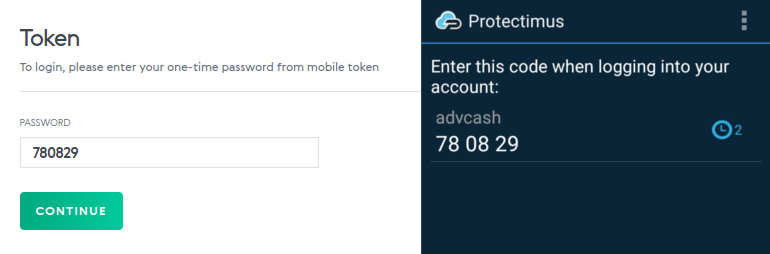
What is HMAC
What is hash
Hash is the mathematical algorithm used by HMAC-based one-time passwords. Simply put — it is a math function that turns one value into another, or condenses data to a specific size.
Here’s an example. If this passage was run through a hashing algorithm:
the result, known as a hash value (SHA-1, hex), would be this:
2faff97be86cbbf921b8e5b9e1c74b82af080016
At the same time, if we change the slightest detail in the source text, for example, remove quotation marks, the hash value will be completely different:
D0f8e2703fb647ce0504f6222c04f473f9f88a94
No matter what the volume of the source information is, be it a Moby-Dick or just a phone number, its hash value is always a string of symbols of a predetermined size. Comparing a hash and the hash value is far easier for a computer than comparing original files. So the hash value from the example would be a convenient tool for a computer to compare, identify or run calculations against data and files.
Hashing is used for a variety of purposes, among them is compression, cryptography, data indexing, checksum generation. Also, it’s impossible to decode the source information from the hash, what differs hashing from encryption. Thus, it is an especially good fit for cybersecurity purposes.
| Read also: Identification, authentication, and authorization – what’s the difference
What is MAC
Message Authentication Code, or MAC, is a crypto checksum for data transferred through insecure channels. With MAC applied the receiving party can verify the authenticity of the message simply by establishing that the sender has the secret key. In case the sender does not have the correct seed, the MAC value would be wrong and the recipient would know the message was not sent from the legitimate sender.
First of all, the sender and the recipient share a secret key (also called a seed) and agree to use the same MAC generation algorithm.
Before sending the message, the sender generates the Message Authentication Code passing the message (Message) with the shared secret (Key) through the MAC generation algorithm. Then they send the message and the received MAC to the recipient.
When the recipient gets the message, they also generate the Message Authentication Code in their turn, passing the message they just received (Message) and the shared secret (Key) through the same the MAC generation algorithm. If the MAC they get matches the MAC they received from the sender, it means that the message is legitimate.
Here’s what a MAC function work would generally look like:
- A sender sends a Message and MAC (Message, Key), M1
- The recipient gets both inputs
- The recipient makes their own MAC (Message, Key), M2
- If M2 does not equal M1, data was compromised
- If M2 equals M1, data is valid
| Read also: The Pros and Cons of Different Two-Factor Authentication Types and Methods
So what is HMAC
HMAC, as you might have guessed already, stands for hash-based MAC. HMAC authentication passcode is procured by running a hash (in multi-factor authentication HMAC-SHA1 function is more frequently used, less often SHA-256) over the initial data and the shared secret key.
You already know how hash and MAC functions work separately. When put together the HMAC algorithm both ensures the sent data was not tampered with and that it was sent from a legitimate source by comparing the hash value and the shared key. The key is generated in a key exchange process and only the two parties that were involved in the exchange can know it, so only these two can get the exact same output when working the message’s MAC with the seed.
| Read also: The Evolution of Two-Step Authentication
What is HOTP
HOTP (HMAC based OTP algorithm) is also often referred to as event-based one time pass. HOTP authentication requires two inputs. The first one is the seed shared by the server and the HOTP token, this is a constant that validates the OTPs. The second one is a counter, which is a variable stored on the server and the token (these two are, naturally, synchronized). The token’s counter scales up each time the button on the device is clicked, the server counter scales up with each validated OTP.
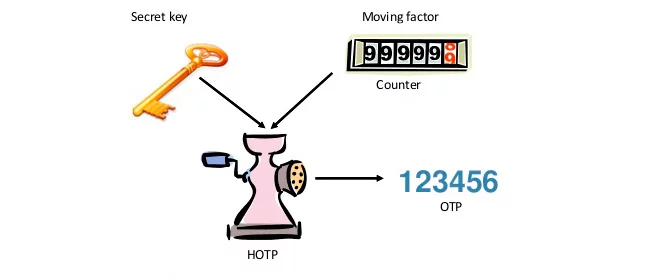
HOTP is calculated by first creating an HMAC hash from the seed and counter. The result output is too long though, it’s a 160-bit long string. Thus, next, it is shortened to a reasonable 6 or 8 digits, which is the OTP displayed on the token.
HOTP is the original OTP algorithm. HMAC encryption used here makes it virtually impossible to decode the secret key or reproduce the password. But, of course, there are drawbacks to HOTP, and we will look at them next.
| Read also: 2FA Security Flaws You Should Know About
HOTP synchronization problem
We’ve briefly mentioned this above — the counter required for HOTP algorithm to work is incremented on the OATH token each time the button is clicked, while the server counter is incremented only when a password is successfully validated.
Essentially, what occurs is — the server remembers the last counter value which resulted in successful validation (let’s name it C). When a new OTP is to be confirmed the server will try C + 1, + 2, +3, etc until it gets the one that matches. Or until it arrives at what is called “a look-ahead window”.
The user may click the HOTP generator button a few times between login attempts, this is accounted for. What is not accounted for is that these few times might top the look-ahead window. The server assumes the client will not click the button more than 80-100 times (the recommended look-ahead window) in succession before attempting to log in.
And here lies the problem — if, for example, a child gets their hands on your token and clicks the button one time too many, you will have a useless token and failed login.
| Read also: Time Drift in TOTP Hardware Tokens Explained and Solved
HOTP security problem
Every HOTP code is valid until it’s used, or until a subsequent one is validated by the server. So a criminal does not even have to steal the token, all they need to do to gain access to your OTP protected account is to write down a few codes. If they have the time they might even press the button 100+ times and you’ll never know what hit you.
| Read also: Best Protectimus MFA Features for Financial Services Cybersecurity
HOTP vs TOTP
TOTP, or Time-based OTP, is basically a branch of HOTP. And it has a huge advantage over HOTP — instead of the HOTP counter, TOTP tokens use time (UNIX time plus time-steps). Like with HOTP the user and server share a seed on setup. Unlike with HOTP — after that, the OTPs are generated using the number of time steps from the UNIX time. Usually, the time step is set to either 30 or 60 secs.
OATH HOTP-compatible tokens generate OTPs that do not have an expiration period. And we have already come to the conclusion that this creates a major security vulnerability. TOTP passcodes, on the other hand, have the advantage of being valid for a limited time period — the time step. So if the generated pass is not used within the 30-60 seconds it expires and can not be used for login.
So when considering TOTP vs HOTP the obvious choice is TOTP, simply because it is more secure.
| Read also: TOTP Tokens Protectimus Slim NFC: FAQ
Protectimus tokens with HOTP algorithm
Taking into account the cons of the HOTP algorithm, mentioned above, we decided not to use or sell hardware HOTP tokens. But the HOTP algorithm shows itself useful when it comes to software OTP delivery methods.
We use the HOTP algorithm for SMS authentication, 2-factor authentication via chatbots in messaging apps, and email authentication. As it takes some time to deliver a message with a one-time password via any of these channels, a TOTP-password, only valid for 30 or 60 seconds, might be delivered too late, and the user won’t be able to login their account with this OTP. HOTP password remains valid until used, that’s why using the HOTP algorithm is a much better approach in this situation.
By the way, unlike most other popular 2FA applications, our software 2-factor authenticator Protectimus Smart also supports the HOTP algorithm along with TOTP and OCRA.
Read more:
- TOTP Algorithm Explained
- OCRA Algorithm Explained
- Two-factor authentication for Windows 7, 8, 10
- Active Directory Two-Factor Authentication
- Electronic Visit Verification with Hardware Tokens
- SMS Authentication: All Pros and Cons Explained
- How to Backup Google Authenticator or Transfer It to a New Phone
- Detailed Information on Data Signing
- 4 Reasons Two-Factor Authentication Isn’t a Panacea
- Duo Security vs Protectimus
Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from our team.

Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from Protectimus blog.
You have successfully subscribed!