Recently, Cisco declared its intention to purchase Duo Security for US$2.35 billion. Naturally, this is an important event not only for Duo Security, but for the entire multi-factor authentication industry. A sale of this magnitude confirms that the demand for two-factor authentication is higher than ever before. This also shows that there is a demand for simpler, less expensive means of delivering one-time passwords, since Duo prominently advertises its rejection of hardware tokens in favor of 2FA apps, push notifications, and SMS messages (which are expensive and not secure).
Protectimus fully supports Duo Security’s efforts to simplify and reduce the cost of OTP delivery, but we remain convinced that security must not be sacrificed in the process. For example, in order to hasten the move away from SMS authentication to more modern, reliable MFA technologies, we’ve figured out how to deliver one-time passwords using chatbots on messaging services. This is much more efficient, secure, and convenient than SMS. Hardware tokens are also among the products we offer, and they can be connected to practically any site: from Google, Facebook, Dropbox, and Slack to cryptocurrency exchanges like Bitfinex, Coinbase, Poloniex, and so on.
In light of that, has Cisco made the right decision? Should they maybe have spent $2.35 billion on acquiring Protectimus instead? We’ve decided to compare the solutions from Duo and Protectimus to settle the matter objectively.
DON’T LIKE LONG READS? FIND OUR CONCLUSIONS IN A COMPARISON TABLE AT THE END OF THE ARTICLE.
1. Server-side component
Duo Security
Duo is a cloud-based 2FA solution. The choice of the SaaS model is completely logical. It makes integration fast and reduces the cost of deploying, protecting, and maintaining an authentication server. This style of interaction is convenient and easy for the client and company alike. In addition, it’s a rather modern approach to strong authentication, so it fits well with Duo Security’s concept as a modern, innovative provider of revolutionary MFA solutions.
Protectimus
Protectimus two-factor authentication solution is available not only in cloud-based form but also as an on-premise platform.
Often, we advise customers to choose the cloud-based service, since it’s convenient, fast, and modern. Clients connected to the Protectimus SaaS service don’t need to waste time and money on extra equipment, security measures, and sysadmin salaries — there’s no load balancing or other infrastructure issues to worry about. The result is rapid integration with minimal costs.
However, some companies can’t make use of cloud-based services because of strict information security rules, either from within the company or imposed by the government. For these cases, we made it possible to purchase an on-premise platform that clients can install in their own environments, allowing them to retain full control of the authentication server. Both the on-premise platform and cloud-based service are available with a subscription. Lifetime licenses for the platform can also be purchased.
You can find out more about the differences between the cloud-based service and the platform here.

2. Features
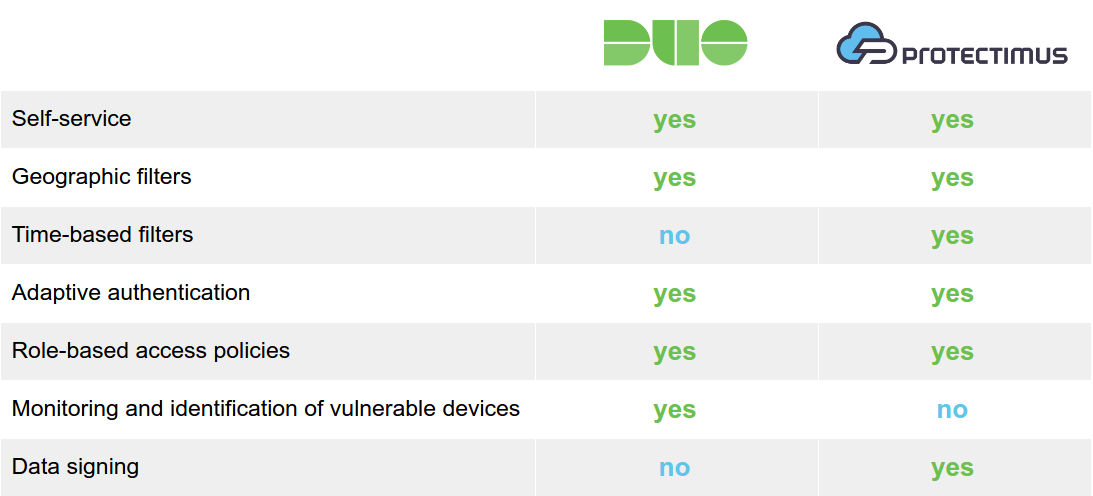
Duo Security
Note: Nearly all features examined in this section can be activated only with Duo’s most expensive payment plans, Access and Beyond. Self-service is also available in the Duo MFA basic plan.
Duo offers a range of additional features to make administration easy and increase the level of resource access protection:
- User self-service.
- Geographic filters.
- Prohibiting access from anonymous networks.
- Access control based on IP address.
- Role-based access policies allowing the administrator to impose custom (stricter) authentication requirements for users with the highest access level.
- Device access policies allowing the administrator to control which devices can access the applications. It checks the mobile devices with the Duo Mobile app installed on hygiene, operating system, browser, plugins, and whether screenlocks and biometrics are enabled, offering protection against viruses, hacking attacks, and unlocking by curious passers-by. This function was developed because Duo Security emphasizes mobile authentication, and mobile devices are rather vulnerable.
You can find out more about these features by reading “Duo Security vs Protectimus: Features.”
Protectimus
Note: All features examined in this section are available with all payment plans, including the no-cost Protectimus Free plan.
In terms of features, Protectimus two-factor authentication service is not inferior to Duo’s in any way. Features available to users in both 2-factor authentication services include:
- Self-service.
- Geographic filters.
- Adaptive authentication.
- Differentiation and delegation of authority within the system.
- Ability to assign different types of tokens to different users.
At the same time there are few features we weren’t able to find equivalents in Duo’s 2FA product:
- time-based filters;
- CWYS (Confirm What You See) data signing functionality.
The only feature Protectimus lacks thus far is the ability to scan users’ mobile devices to determine if an antivirus is installed, the OS is up to date, and Touch ID is enabled. Duo developed this functionality because of the specifics of its 2FA solution, which is geared toward software-based means of OTP delivery. However, upon request, we’re always ready to customize the system in order to provide equivalent capabilities. Customizing the Protectimus solution based on our customers’ requirements is our specialty.
You can find out more about these features by reading “Duo Security vs Protectimus: Features.”
3. Technologies
Duo Security
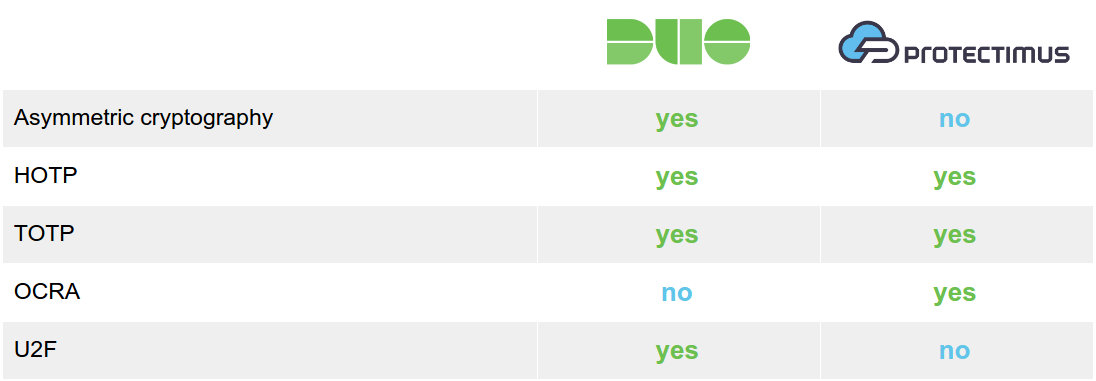
Duo’s two-factor authentication system is built on the principles of asymmetric cryptography. The private key is stored on the user’s smartphone, while the public key is stored on the authentication server. First, the authentication server communicates with the Duo Mobile application. The user confirms the action, the communication is signed with the private key, the request returns to the server, the signature is verified with the public key, and the user gains access to the resource. This is a good approach. It guarantees that even in the event that Duo Security’s servers become compromised, an attacker cannot gain access to users’ accounts. However, asymmetric cryptography only works with Duo Push.
As an alternative to push notifications, Duo offers good old one-time passwords generated based on a shared secret and a counter. The Duo Mobile app and Duo hardware tokens use the HOTP (HMAC-based one-time password) algorithm to generate OTPs. While the HOTP algorithm does meet two-factor authentication standards, it is quite outdated. The problem lies in the fact that HOTP passwords remain current until used (compared to TOTP and OCRA, under which passwords are valid for no more than 60 seconds). Suppose that a third party is able to gain control of an HOTP token for one minute. All the third party needs to do is generate and write down a series of passwords and use one of them before the account owner notices something is wrong. The actual user will no longer be able to access the account, since the HOTP token will have become desynchronized from the server.
This deficiency in HOTP algorithm is the reason for the shift toward the more modern one-time password generation algorithms: TOTP (Time-based One-Time Password) and OCRA (OATH Challenge-Response Algorithm). The moving factor in these algorithms is time (and not a counter, like HOTP’s). One-time passwords generated using the TOTP algorithm remain valid for just 30 or 60 seconds. And thanks to OCRA, the data signing functionality described in the article “Duo Security vs Protectimus: Features” is available.
Duo Security allows connecting third-party TOTP hardware tokens to its 2-factor authentication service but doesn’t recommend it as there is no functionality for time synchronization in its MFA system.
U2F tokens can also be connected to Duo’s service. You can read more about U2F here. The principles of U2F are somewhat similar to those of asymmetric cryptography, described above.
Protectimus
The Protectimus two-factor authentication solution is fully compliant with the OATH (Initiative for Open Authentication) standards. Protectimus 2FA service supports all OATH one-time password generation algorithms: HOTP, TOTP, and OCRA.
HOTP, TOTP and OCRA algorithms presuppose one-time passwords’ generation based on a shared secret and some variable. For HOTP, this variable is an event counter. For TOTP, it’s the current time, and for OCRA, it’s the time and a specific data set. The algorithms work like this: the token takes the current variable and shared secret, hashes them, and ends up with the one-time password. The user sends this one-time password to the server, which performs the same calculations in turn and compares the values. If the values match, the user is granted access to their account.
You can find out more about how one-time passwords work here.
All OATH algorithms are publicly available standards, and they have been tested for vulnerabilities by thousands of hackers. All the flaws in these algorithms have been identified, and 2FA providers learned to deal with them long ago — there will be no surprises when it comes to security. Shared secrets stored on Protectimus servers are encrypted using an HSM (hardware security module). In the event that the Protectimus authentication server is compromised, an attacker will be unable to compromise the shared secrets.
4. Authentication methods
Duo Security
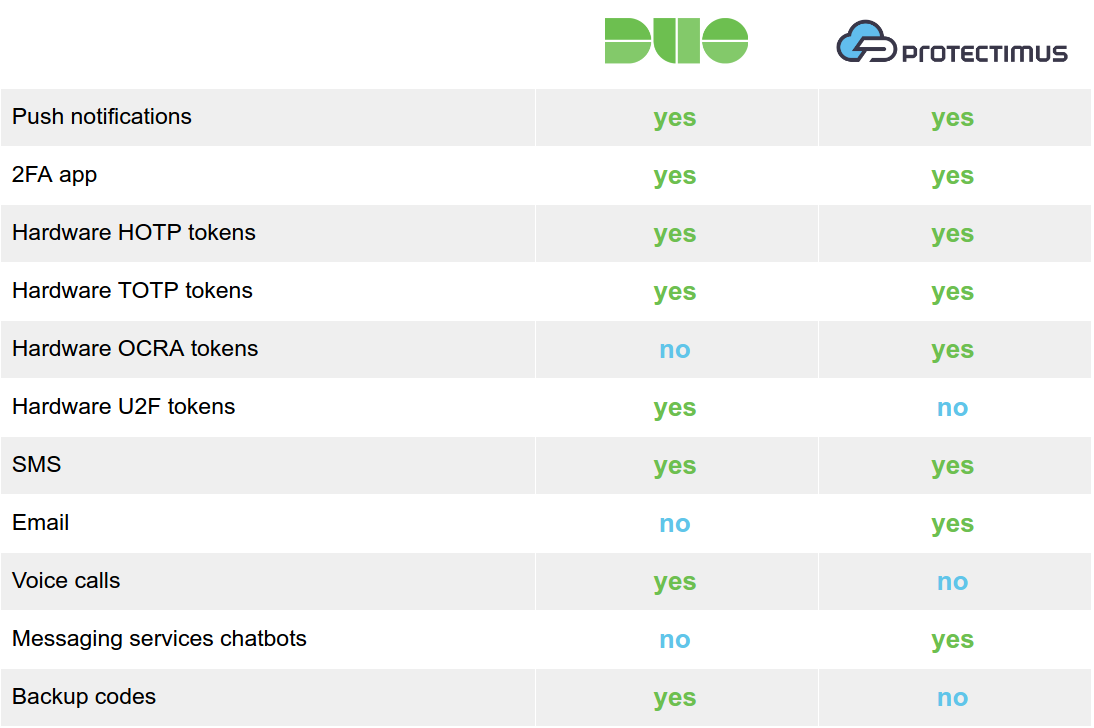
One of the reasons Duo Security’s solution has become popular is the Duo Mobile application with its push notification feature. Users need only tap an “Approve” button on their smartphones to complete the second authentication step.
The Duo Mobile app can also generate one-time passwords using the HOTP algorithm (for logging into Duo-protected accounts) and TOTP (for logging into third-party services with two-factor authentication). In addition to the app, the Duo system supports SMS messages, voice calls, hardware HOTP tokens, as well as third-party U2F and TOTP tokens.
In “Duo Security vs Protectimus: Authentication methods“, we take a closer look at all the one-time password delivery options Duo offers its users, including their strengths and weaknesses.
Protectimus
All the authentication methods Protectimus offers meet OATH standards. Protectimus customers can choose from standard, hardware-based HOTP, TOTP, and OCRA tokens with hard-coded shared secrets; reflashable Protectimus Slim NFC hardware TOTP tokens; the Protectimus Smart 2FA app with support for push notifications, HOTP/TOTP/OCRA algorithms, and CWYS data signing functionality; SMS authentication; email authentication; and one-time password delivery via messaging services.
You can find out more about each authentication type offered by Protectimus in “Duo Security vs. Protectimus: Authentication methods“.
5. Integration
Duo Security
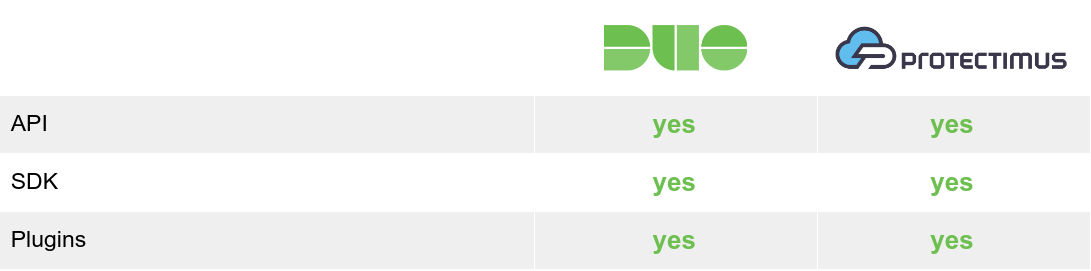
Duo provides an enormous assortment of plugins and an SDKs (Software Development Kits) for convenient integration with client systems. For paid plans, an API is also available. All documentation is provided on the company’s site.
Protectimus
An API for integration with the Protectimus service is available even with the free plan. SDKs for popular programming languages (Java, PHP, Python) and an assortment of plugins have been developed to enable integration with just a few clicks. It’s worth noting that the number of plugins available is less than that offered by Duo, but we’re always working to expand the opportunities for integration with Protectimus. All integration-related documentation is openly accessible on the company’s site.
6. Pricing
Duo Security
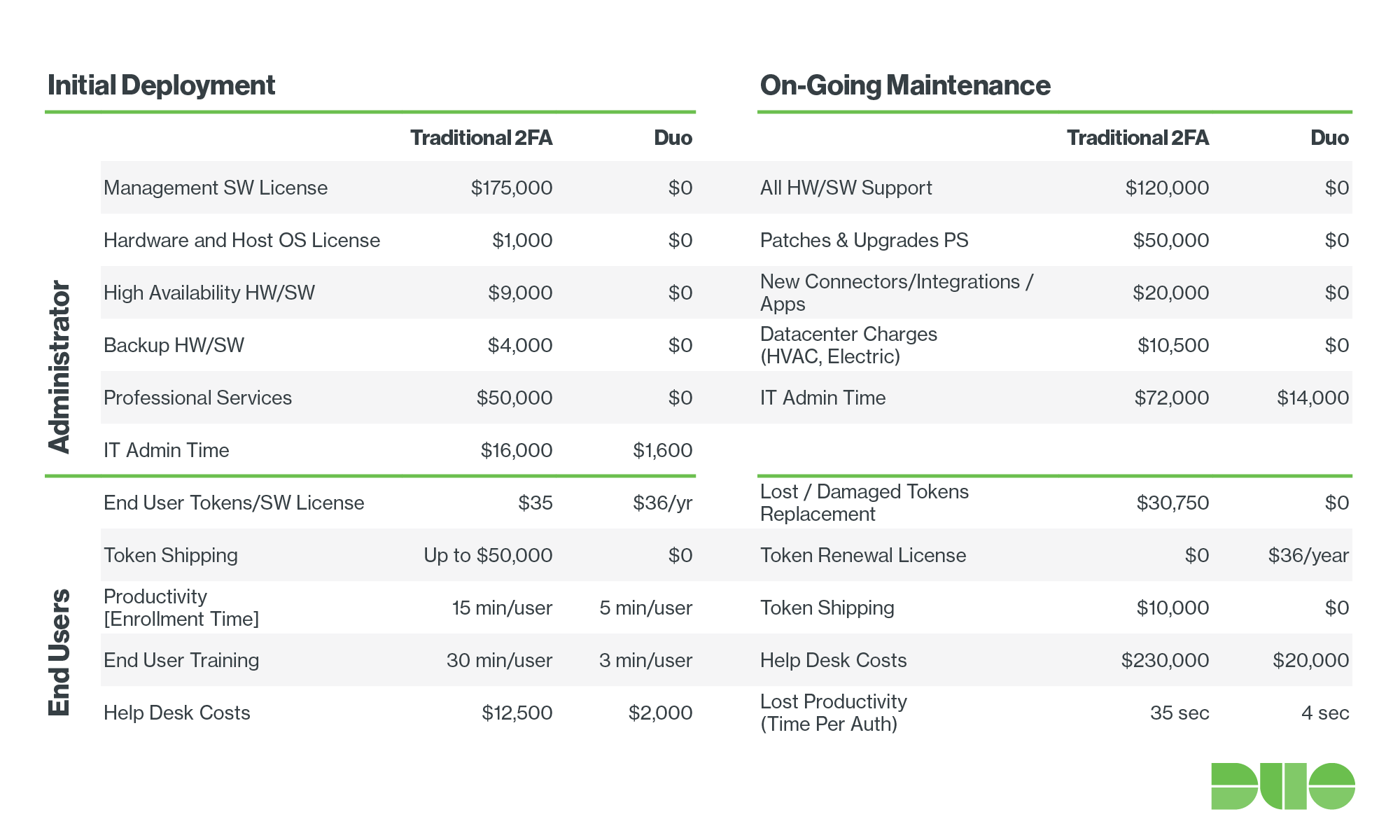
Up to 10 users can be connected to Duo Security’s strong authentication service for free. However, with this plan, not a single one of the functions listed under “Functionality” is available. Furthermore, API-based integration is not allowed. Without payment, Duo only allows you to receive one-time passwords using the app, SMS, or a hardware token. (Note: hardware tokens must be purchased separately.)
Thereafter, pricing depends on the number of features available:
- Duo MFA: US$3 per month, per user. This plan activates the self-service function and includes the ability to evaluate the security level of corporate and personal end-user devices.
- Duo Access: US$6 per month, per user. Self-service remains available with this plan. It also activates the majority of the adaptive authentication features (geographic filters, IP-based access control, blocking authentication from anonymous networks, ability to impose custom authentication rules for employees with different access levels). Vulnerable devices identification and monitoring capabilities become broader: administrators can notify users of the need to update their systems, install antivirus, etc.; block access to the system for devices that don’t meet security requirements, and track whether devices have been rooted or compromised.
- Duo Beyond: US$9 per month, per user. All of the Duo two-factor authentication system’s features are available.
While Duo’s rates aren’t cheap, their pricing does seem quite accessible if to compare to the two-factor authentication market’s “veterans” (RSA, Vasco, Gemalto, etc). No up-front payment is required to connect to the system, the quick integration saves administrators time, and there are no additional costs associated with setting up, protecting, and maintaining a local authentication server. For example, you can find a table on the Duo Security site comparing their service to that of RSA. As you can see there, integration and support with Duo’s solution is 60% less expensive.
Protectimus
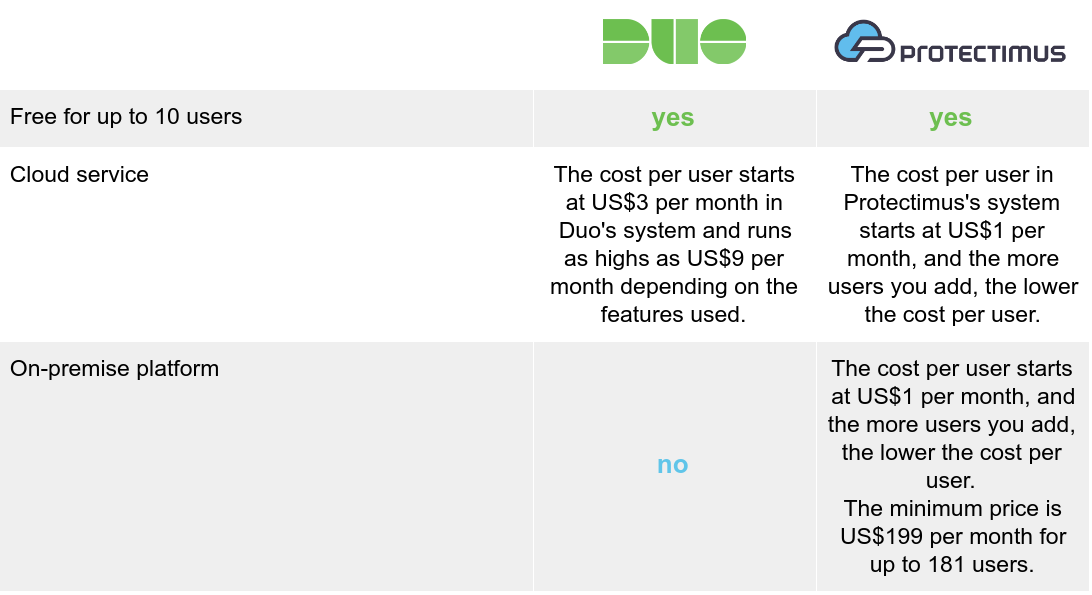
Protectimus customers receive a modern two-factor authentication solution at least as good as that of Duo and other competitors — often better — and it’s cheaper. The cost of support for a single user in the Protectimus system starts at US$1 per month, and the more users you add, the lower the cost per user. All features are available regardless of the plan you choose, even if you choose the free plan.
As with Duo, up to 10 users, Protectimus strong authentication solution is free. Customers can nonetheless access all of the Protectimus cloud service’s features. (Note: additional resources, filters, administrators, SMS, and hardware tokens must be paid for separately.)
- Starter plan: US$33 per month. This plan includes support for 1 resource and 34 users, self-service, and the ability to connect any type of token.
- Business plan: US$111 per month. This plan includes support for 2 resources, 2 filters (geographic and time-based), 1 additional administrator, 144 users, self-service, and the ability to connect any type of token.
- Custom plan: from US$1 per month, per user. This plan allows you to connect any number of users, resources, administrators, and filters. It also gives you access to the rest of the features Protectimus offers. The cost of the service depends on the number of users you connect. The more users you have, the lower the cost per user. All additional features enabled by the customer are charged separately. No matter what you do, the total cost will never be greater than US$1.50 per user, per month, making it cheaper than even the cheapest plan from Duo.
The minimum price for the Protectimus on-premise platform is US$199 for up to 181 users. The on-premise platform is available with a monthly subscription. Lifetime licenses can also be purchased. If you have questions about the service or on-premise platform pricing, contact sales@protectimus.com.
With Protectimus, customers pay only for what they get. There are no up-front costs, paid consultations, or authentication server maintenance costs (if you don’t need the on-premise platform). The cost per user is also significantly lower than that offered by any competitor.
7. Summary
In this overview, we’ve tried to touch on all the important aspects of choosing a two-factor authentication provider. As you might expect, these two systems with a modern approach to MFA offer a range of similar features. There are, however, some unique functions: Duo features end-user device security monitoring, while Protectimus offers data signing, reflashable hardware tokens, and delivery of one-time passwords in messengers.
To make it easier for you to choose a two-factor authentication solution that perfectly fits your needs and your use case, we’ve collected all of our conclusions about Duo and Protectimus in a comparison table. It looks like this contest has no winners and losers — just two strong competitors.
Features | Duo Security | Protectimus |
1. Server-side component | ||
| Available in the cloud | yes | yes |
| Available on-premise | no | yes |
2. Functions | ||
| Self-service | yes | yes |
| Geographic filters | yes | yes |
| Time-based filters | no | yes |
| Adaptive authentication | yes | yes |
| Role-based access policies | yes | yes |
| Monitoring and identification of vulnerable devices | yes | no |
| Data signing | no | yes |
3. Technologies | ||
| Asymmetric cryptography | yes | no |
| HOTP | yes | yes |
| TOTP | yes1 | yes |
| OCRA | no | yes |
| U2F | yes | no |
4. Authentication methods | ||
| Push notifications | yes | yes |
| 2FA app | yes | yes |
| Hardware HOTP tokens | yes | yes |
| Hardware TOTP tokens | yes2 | yes |
| Hardware OCRA tokens | no | yes |
| Hardware U2F tokens | yes | no |
| SMS | yes | yes |
| no | yes | |
| Voice calls | yes | no |
| Messaging services chatbots | no | yes3 |
| Backup codes | yes | no |
5. Integration | ||
| API | yes4 | yes |
| SDK | yes | yes |
| Plugins | yes | yes |
6. Pricing | ||
| Free for up to 10 users | yes | yes |
| Cloud service | The cost per user starts at US$3 per month in Duo’s system and runs as highs as US$9 per month depending on the features used. | The cost per user in Protectimus’s system starts at US$1 per month, and the more users you add, the lower the cost per user. |
| On-premise platform | no | The cost per user starts at US$1 per month, and the more users you add, the lower the cost per user. The minimum price is US$199 per month for up to 181 users. |
- ↑The Duo Mobile app supports TOTP for third-party services, also you can use third-party hardware tokens with Duo 2FA service.
- ↑Only third-party TOTP tokens.
- ↑Currently, Protectimus Bot is available on Telegram, Viber, and Facebook Messenger
- ↑API available only with paid plans
Read more
- Duo Security vs Protectimus: Features
- Duo Security vs Protectimus: Authentication Methods
- How does 2-factor authentication work?
- The Evolution of Two-Step Authentication
- The Pros and Cons of Different Two-Factor Authentication Types and Methods
- Mobile Authentication Pros and Cons
- How to Backup Google Authenticator or Transfer It to a New Phone
- Protectimus New OTP Tokens
- Why US, Canadian, and EU Universities Choose Programmable Hardware OTP Tokens
Image and logo source: duo.com
Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from our team.

Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from Protectimus blog.
You have successfully subscribed!