This article discusses two-factor authentication apps, which feature different functionalities, are based on different principles but serve one purpose – reliable protection of access to sensitive information. Today, we will try to review some of the most popular applications for one-time passwords generation from the Google Play market and two hardware OTP tokens that can replace two-factor authentication apps. There are a lot of convenient or security-oriented features that the apps’ and OTP tokens’ authors offer. Let’s finally figure out some of the pros and cons of each.
Turn on all security features like two-factor authentication. People who do that generally don’t get hacked. Don’t care? You will when you get hacked. Do the same for your email and other social services, too.
Robert Scoble
Top 3 Most Popular 2FA Applications
1. Google Authenticator
Google two-factor authentication app is probably the most popular and best known among 2FA evangelists. It’s free, handy, and offered on many websites by default. Let’s have a look at its features:
- User-friendly. Google Authenticator has decisive, easy to use, clear UI (user interface) that even a child would find informative. Besides, it should be noted that the software works on almost all versions of Android and takes no more than 2 MB, which is significant for owners of phones with a small amount of RAM.
- TOTP and HOTP algorithms. Google Authenticator app supports both Time-based One-Time Password (TOTP) and HMAC-based one-time password (HOTP) OTP generation algorithms, which allows using it with more resources. TOTP is more widespread and reliable – this is an algorithm in which time is used as one of the parameters for one-time passwords generation. Though there are still websites using HOTP algorithm where the counter is used to compute the passwords. The lifetime of all OTP passwords generated according to TOTP or HOTP algorithms is 60 seconds, i.e. every minute a new password is created.
- No need for network connection.The use of such OTP generation algorithms allows Google Authenticator to work without the network connection. The same one-time passwords would be generated on your smartphone without access to the Internet or cellular network and on the authentication server (in client-server paradigm), if the one-time passwords match, you get access to your account.
- Many accounts in one place. You can use one app for all your accounts on different websites as well as for your multiple accounts on one website. This is very convenient when compared with SMS authentication, but mind that you may have a lot of troubles when losing or wiping a phone if you don’t take care of Google Authenticator backup.
Are there any drawbacks in Google Authenticator?
Here we have some black clouds above the app:
- There is no built-in possibility to backup your data. It means that the users must renew information each time they change the phone or account.
- They say it’s not quite convenient to use this app if you turn on 2-factor authentication for more than 4 websites. Four one-time passwords are enough to occupy the whole screen and if you have, for example, 12 accounts, you won’t see all passwords at a glance.
Google two-factor authentication app could be the most known one, but let’s be honest – there are many other analogs on the market today.
| Read also: Will Google’s Authentication without Passwords Be Safe?
2. Protectimus Smart OTP
A free two-factor authentication app with cloud backup for iOS and Android devices.
So far this is the best free authenticator on the market which provides ample opportunities:
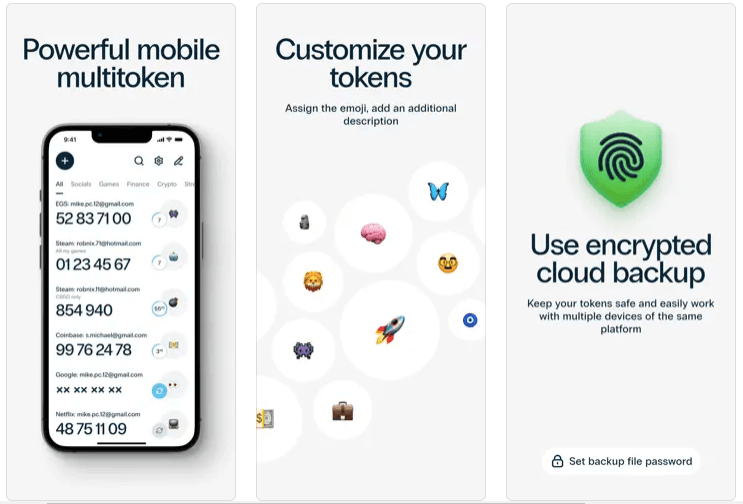
- Cloud backup of all enrolled tokens.
- Ability to transfer tokens to a new phone;
- Ability to import tokens from Google Authenticator;
- Support of biometric authentication for the users of smartphones with fingerprint scanners and FaceID.
- PIN protection. A possibility to protect the application from an unauthorized access with a PIN-code.
- Any authentication algorithm you need is available. Supports different OTP generation algorithms (HOTP, TOTP, and even OCRA).
- 6 and 8 digits long OTPs. The ability to change the length of a one-time code from 6 to 8 characters.
- Convenient distribution of OTP tokens by folders.
- Customization of tokens with different emojis and descriptions.
- Push notifications support.
- Data signature function (CWYS). Protectimus SMART OTP application supports one of the most advanced multifactor authentication features – Confirm What You See (CWYS). This feature is mainly used by payment systems or banking institutions as it allows signing transfers with one-time passwords generated on the basis of payment details. Thus, not only the secret key and time or counter but also such details as transfer amount, currency, addressee, etc. are used when generating the OTP password. Even if such one-time password is intercepted by the fraudster it remains useless as it remains valid only for the payment initiated by the user.
- Multiple language support: English, French, German, Spanish, Russian, and Ukrainian.
| Read also: Detailed Information on Data Signing
3. Authy 2-Factor Authentication
Being based on a similar working principle, Authy stands out with some interesting and extremely useful features:
- Desktop version. It does not matter if you have a smartphone, or just want to use the application on your computer – you have such a choice. The developers took care of the convenience of desktop users.
- Cloud backup. The application allows the user to backup data and store them in a protected cloud. So in case, you lose your smartphone or accidentally (or not) delete all the data from it, the application will help you restore access to the previously linked accounts in a few clicks.
- Passcode protection. Also, a distinctive feature can be considered the incorporation of a master PIN – you can block the application so that it cannot be used by some indecent person.
- Multi-device synchronization. You don’t need to scan the same QR code with the secret key with all your devices, for the user convenience Authy offers multi-device synchronization feature.
Are there any drawbacks in Authy?
- Part of the authentication method that it uses is SMS which is technically against best standards for 2FA.
- Multi-device synchronization feature may entail a risk. As password protection of the app is not obligatory, you are never sure if some of your devices aren’t used behind your back.
- If you already use another app and would like to transfer all your tokens to Authy, there are a lot of guides on the Internet teaching how to do this quickly and easily but all of them require a rooted phone. Please, note, getting root access can significantly damage the security of your apps and make the device prone to getting viruses and errors.
| Read also: The Pros and Cons of Different Two-Factor Authentication Types and Methods
Other Popular Two-Factor Authentication Apps
Microsoft Authenticator
Like other listed applications, Microsoft Authenticator is the two-factor authentication app for keeping a great level of security for all your accounts and sensitive data. This application will be an indispensable assistant if you are using a Microsoft account or have a Windows 10 OS on your smartphone.
- Verification codes. The application can be used as a software token to create an OAuth verification code. In this mode, the principle of operation of the app remains the same as for all 2FA applications of this kind.
- Notifications. In this mode, the application sends notifications to your device every time you try to access your account from an unknown environment. To confirm the entry it’s enough to choose “Verify”, to block it choose “Deny”.
Are there any drawbacks in Microsoft Authenticator?
- Some users have troubles with app’s functionality, certificates and data exchange across phone-server.
- As well as in Google Authenticator there is no possibility of backup and the see one-time passwords only for 4 accounts at a time.
| Read also: How does 2-factor authentication work?
FreeOTP Authenticator
For open-source fans, there is an interesting and, most importantly, simple, and at the same time functional application FreeOTP Authenticator.
- Works for many services.The program works with many popular services: Google, Facebook, GitHub; it’s also available for iOS and Android. Though we can say this about almost every application in this list.
- Low weight. FreeOTP Authenticator “weights” only 500 KB which is one of its main advantages. Some of its competitors require up to 6MB smartphone’s RAM.
- Open-source. Open-source solutions often offer not to become attached to proprietary servers\services, but use free analogs. This is the case with the FreeOTP. The application maintains HOTP and TOTP integration.
Are there any drawbacks in FreeOTP Authenticator?
- The app definitely requires smoother and more user-friendly interface.
- There is no backup or restore feature.
- Guess for some users it might be a critical case at some point: the app is not available on desktops.
| Read also: Top 7 Tips How to Protect Yourself from Phishing Scams
Sophos Authenticator
Sophos Authenticator is similar to any other 2-Factor Authentication – supports both TOTP and HOTP one-time passwords generation algorithms, works offline, supports a wide range of services: Google, Dropbox, Facebook, etc. but also has a number of differences that help it stand out among the similar applications:
- Different hash algorithms support. Sophos Authenticator supports various hash algorithms: SHA-1, SHA-256, and SHA-512.
- High flexibility. It’s possible to choose any desirable one-time passwords lifetime – not just 30 or 60 seconds, it can be any number of seconds you wish.
- 6 and 8 digits long OTPs. The app gives a possibility to generate codes of different length – 6 or 8 digits.
Are there any drawbacks in Sophos Authenticator?
- The common issue for the majority of two-factor authentication apps is the absence of backup.
- Besides, here we have another critical issue: sometimes the app not working correctly with VPN connection (especially through IPSec) and with RADIUS through the wireless connection.
| Read also: Mobile Authentication Pros and Cons
Authenticator Plus
The application which in the free version is similar to the Google Authenticator in features, but surpasses it in the paid version. The most standing out capabilities of the paid version:
- Automatic backups. The paid version provides a possibility of creating automatic backups on different cloud platforms (Dropbox, Google Drive).
- Convenient organization. You can create your own categories and change the location\grouping shortcuts for the most frequently used applications.
- Multi-device synchronization. There is a possibility to synchronize Authenticator Plus across all the devices you use which is quite user-friendly.
- Encryption and PIN. This 2FA app is additionally protected with the PIN code and all the user’s data are reliably encrypted with 256-bit AES encryption.
Are there any drawbacks in Authenticator Plus?
- The greatest drawback is that all best features are available only in the paid version.
- There are many complains about the absence of user support and manuals, besides, there are some troubles with the barcode scanning on the Amazon Fire and Kindle Fire smartphones.
| Read also: The Evolution of Two-Step Authentication
LastPass Authenticator
Yet another program with interesting authentication option – one-tap verification (push notifications). The application works with both with LastPass account and with third-party vendors.
The app provides such two-step verification approaches as:
- One-tap push notifications. This feature allows logging in LastPass, Dropbox, Google, Facebook or Evernote account without entering the one-time password but just with the tap on push notification in the LastPass Authenticator app.
- Compatible with a smartwatch. LastPass authenticator is Android Wear compatible so you can get one-time passwords or push notifications directly on your smartwatch.
- Cloud backup. Cloud backup option is available, though it’s not automatic.
Are there any drawbacks in LastPass Authenticator?
- To use the convenient one-tap notifications option even with Google, Facebook, Dropbox or Evernote you must create a LastPass account. Besides, you’ll have to install a special LastPass extension in all the browsers you use.
- The one-tap push notifications are available only for few websites, it would be better to expand the list of supported resources.
- The app generates only 6-digits long OTP passwords.
| Read also: Dutch Scientists: SMS Verification Is Vulnerable
SoundLogin
SoundLogin is an absolutely new approach to 2-factor authentication. Developers believe that sound can provide safety. The application uses sound as the second authentication factor, encoding and decoding it into one-time passwords.
- Improved security. The application tries to be as safe as possible and does not transmit any user data – the processing of the encoded signal is performed locally.
- User-friendly. With this app, the users skip the inconvenient step of entering one-time passwords to the login form manually. It’s enough just to point the smartphone to the computer microphone and the app will fill the form on the site automatically.
- Innovative. The technology is quite new and certainly interesting, it’s always fascinating to try something new.
- Extracts and transforms OTPs from other apps and SMS. SoundLogin can extract one-time passwords from incoming SMS messages and other authentication apps like Google Authenticator or FreeOTP, encode them and send them to the browser for further processing.
Are there any drawbacks in SoundLogin?
- Of the minuses, it should be noted that this technology is not yet stable, but it is quite suitable for those who are interested in the newest technologies today.
- Works only for the devices with microphones and requires SoundLogin extension on your browser.
| Read also: Two-Factor Authentication with Background Noise: Is It Safe or Not
Yubikey
Yubikey is a hardware OTP token by Yubico that provides 2FA capabilities by pressing just 1 button. The OTP token is made in the form factor of the USB drive with a button.
- Works autonomously. With hardware OTP tokens you don’t need to worry about internet connection, cellular network or battery charge.
- Supports FIDO U2F standards. Yubikey hardware tokens work with FIDO U2F standard, supported by almost all popular services (Google, Facebook, Github, etc.)
- User-friendly. It’s enough to insert the token into USB input and tap the button to fill in the authentication form.
- Wonderful support. The company provides extensive technical support. The device is highly accessible, practical, and simple in nature.
Are there any drawbacks in Yubikey?
- Requires USB. You can’t use these tokens to login on any device without USB drive. Moreover, often users forget their tokens in USB inputs and someone can take advantage of such forgetfulness.
- USB connection is also an opportunity for malicious software.
- There are a lot of websites that don’t support U2F standard and consequently Yubikey tokens.
- This tiny hardware device is easy to lose and then you’ll have many troubles restoring access to the account.
- The prices on such tokens are quite high, up to $50.
| Read also: Hardware or Software Token – Which One to Choose?
Protectimus Slim NFC
Another hardware OTP token that was designed as a more reliable alternative to two-factor authentication apps is Protectimus Slim NFC. It is a contactless universal programmable hardware token that can be used probably with any website you need: Google, Dropbox, Facebook, Github, MailChimp, etc.
- Contactless. In contrast to software tokens and even USB-tokens Yubikey, using Protectimus Slim NFC
- You can be absolutely sure that it’s not and never will be infected with any malicious software and the passwords generated on this stand-alone device cannot be intercepted.
- You can use it with any device, regardless of whether there is a USB in it or not.
- You or your accountant won’t forget to take it out from the computer.
- Easy to set up. It’s programmed via NFC with the help of free application Protectimus TOTP Burner in few simple steps. So every user of NFC enabled smartphone can order such OTP token, download the necessary app, and program the token with the secret key from almost any website he’d like. The whole process takes about 3 minutes, and you don’t need to register on any third party service. Besides, there is a bunch of setup guides for different websites available on Protectimus blog, which makes the setup process even more convenient.
- Re-programmable. If you don’t want to use the token with one website you can just disable 2FA there and add it to a new website programming it with another secret key. The procedure can be performed countless times.
- Your own design. You can order a custom branding even for one token.
- Nice price. It’s 40% cheaper than the closest competitors.

Are there any drawbacks in Protectimus Slim NFC?
- It’s not too expensive but it’s still not free. For its part, the manufacturer tried to make a token live as long as possible. New models with EPD (e-ink) displays can work up to 7 years when used properly. Not so great a price for years of confidence in your safety.
- You need an NFC enabled smartphone to program the token. Though if your smartphone doesn’t support NFC you can always ask your colleagues of friends to help you with programming the device. It’s not dangerous as the secret keys are not stored in the app.
- Protectimus Slim NFC doesn’t support multiple secret keys, you can use one token with one account at a time.
- Supports only 16-32 symbols long secret keys and has 6 digit display. Some websites’ have longer secret keys or OTP passwords.
| Read also: How to Program Protectimus Slim NFC Token
Conclusion: Which Two-Factor Authentication App or Token Is the Best
To summarize all the above, let’s take a brief view on some pros and cons of the listed above apps:
| Application | Pros | Cons |
| Google Authenticator | Classic easy-to-use 2FA app with TOTP and HOTP algorithm support | Lack of modern functions like PIN, synchronization across devices, and backups |
| Protectimus Smart OTP | Encrypted cloud backup, easy tranfer of OTP tokens to a new phone, import of tokens from Google Authenticator, PIN protection, biometric authentication protection, 6-8 digit codes, data signature function, push notifications support, convenient distribution of OTP tokens by folders and customization of tokens with emojis and descriptions | |
| Authy | Desktop version, cloud backups, and master PIN | Multi-device synchronization feature may entail a risk |
| Microsoft Authenticator | Windows mobile version, verification codes | Some working and data exchange issues, no backup |
| FreeOTP Authenticator | Low weight, open-source and supporting lots of services | No desktop app, rough user interface, no backup |
| Sophos Authenticator | Big amount of supported services and encryption algorithms | Some VPN and RADIUS issues, no backup |
| Authenticator Plus | Automatic backups and synchronization, encryption and PIN | All the best functions are only in the paid version |
| LastPass Authenticator | One-tap push notifications, cloud backup | Small amount of supported services, only 6-digits long OTP passwords |
| SoundLogin | New technology on the market | Not yet stable, works only for the devices with microphones and requires SoundLogin extension on your browser |
| Yubico Authenticator | FIDO U2F, hardware tokens | Requires USB to work, USB connection is also an opportunity for malicious software, the prices on such tokens are quite high, up to $50, there are a lot of websites that don’t support U2F standard |
| Protectimus Slim NFC | Contactless, re-programmable, easy setup, custom branding for one token, nice price | NFC is required to program the token, supports only 16-32 symbols long secret keys and has 6 digit display |
Read more
- 9 Must Follow Gmail Security Rules
- 4 Reasons Two-Factor Authentication Isn’t a Panacea
- Out-of-Band Authentication
- Which messaging apps are trustworthy
- 10 Steps to Eliminate Digital Security Risks in Fintech Project
- 10 Basic BYOD Security Rules
- Social Engineering: What It Is and Why It Works
- Biometric Authentication Pros and Cons
Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from our team.


2018-08-10
Yubikeys aren’t just for U2F. The Yubikey 4 series and Yubikey Neo support standard OATH-TOTP one-time passwords when used with the Yubico Authenticator app, so they are compatible with all of the same websites as Google Authenticator. The Yubikey Neo can store 28 TOTP accounts, and the Yubikey 4 can store 32. The Yubikey Neo supports NFC on Android phones – no USB required.
2018-09-03
There are many other app that deserve this comparison,I tried almost all the app mentioned above,app provide basic functionality and nothing more. In the search of best authentication app I found a app named TOTP aithenticator. This app provides many additional features that app other app lacks like :
Support of widget,notification manager,personalized icon support,24*7 app support.
2020-03-12
Do you mind if I quote a few of your articles as long as I provide credit and sources back to your site? My blog is in the exact same area of interest as yours and my visitors would genuinely benefit from a lot of the information you present here. Please let me know if this ok with you. Appreciate it!
2020-03-12
Hi Audry! Sure, feel free to quote our articles on your blog. We are glad that the info we share is useful for you and your audience.
2020-04-05
Microsoft authencator now supports backup to icloud on my iPod touch running iOS 9.3.5
Would you consider updating this article to give them credit for that?
2020-06-28
It’s hard to come by well-informed people about this topic, however, you seem like you know what you’re talking about! Thanks|