> OWA: Adding Two-Factor Authentication to Outlook Web App
OWA: Adding Two-Factor Authentication to Outlook Web App
This guide shows how you can set up Outlook Web App two-factor authentication (OWA 2FA) using the Protectimus Cloud MFA service or Protectimus On-Premise MFA Platform.
Adding multi-factor authentication to the Outlook Web App protects users’ accounts from unauthorized access and such hacking attacks as brute force, data spoofing, phishing, social engineering, keyloggers, etc.
ATTENTION! .NET Framework 4.7.x is required.
1. Get Registered and Configure Basic Settings
PLEASE NOTE! An SSL certificate trusted on your network must be used to integrate OWA with the On-Premise Platform. An auto-generated certificate created during installation cannot be accepted by the Exchange Server. We recommend using a certificate issued by AD CS via certsrv.
- Register with the Protectimus Cloud Service and activate API or install the Protectimus On-Premise Platform.
- Add Resource.
- Add Users.
- Add Tokens or activate Users’ Self Service Portal.
- Assign Tokens to Users.
- Assign Tokens with Users to the Resource.
2. Install the Protectimus OWA 2FA Сomponent
- Download the Protectimus OWA 2FA installer here.
- Run the installer as administrator.
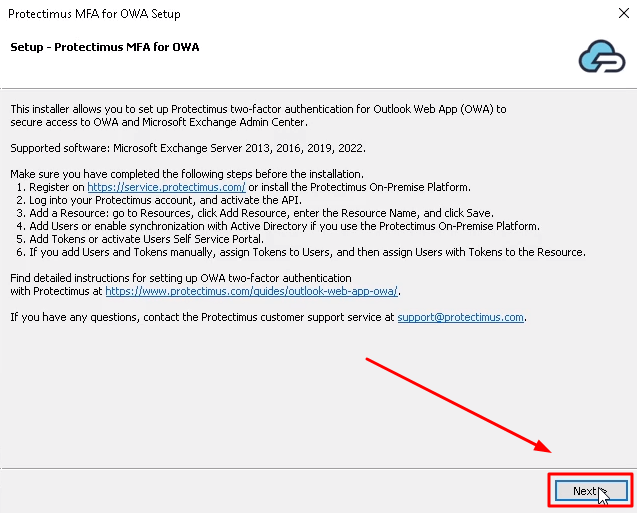
- You will see a welcome screen, click Next to continue.
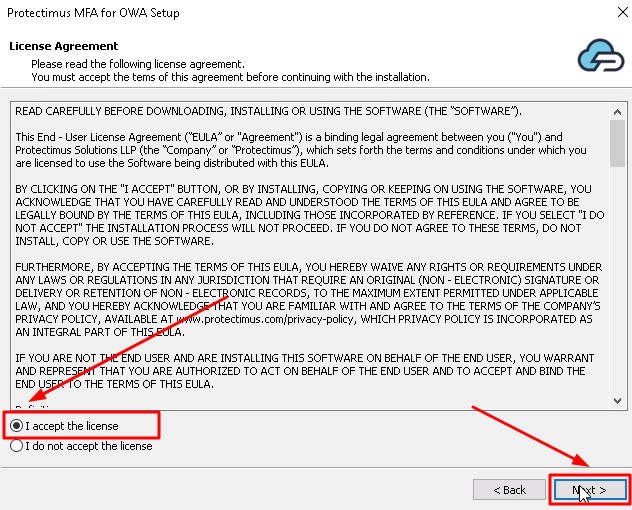
- Read and accept the terms in the license agreement and click Next to continue the installation.
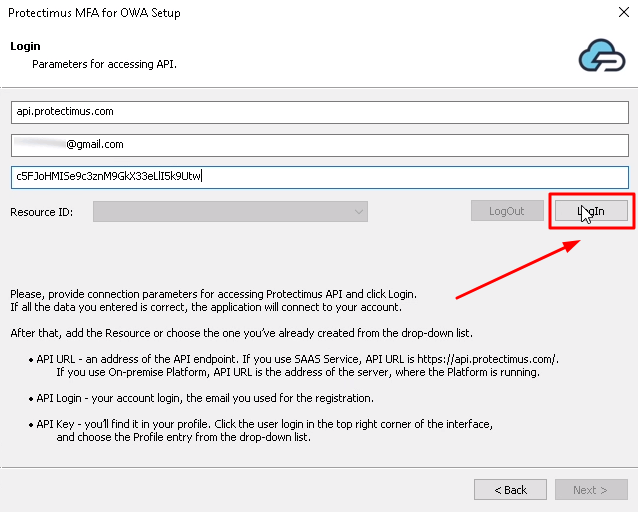
- Enter API URL, Login, and API Key and click LogIn.
These parameters stand for:- API URL – an address of the API endpoint. If you use SAAS Service API URL is https://api.protectimus.com/. In the case of the on-premise Platform, API URL is a server address, where the Platform is running (for example, https://localhost:8443).
- Login – the login of your account, the same as for signing in.
- API Key – you’ll find it in your profile. To access a profile, click the user’s login in the top right corner of the interface, and choose the “Profile” entry from the drop-down list.
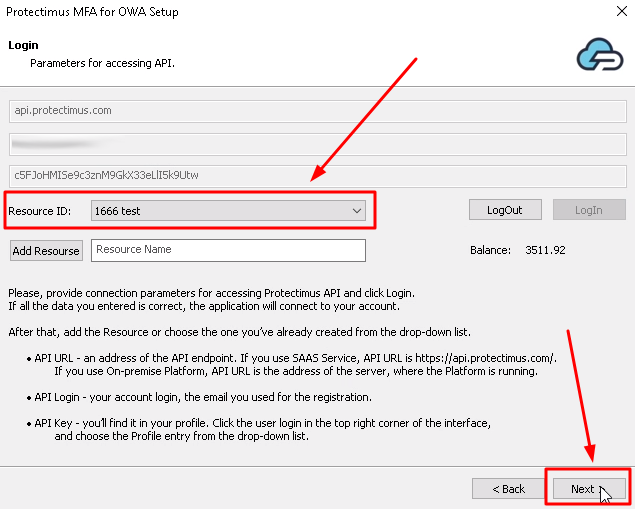
- Resource ID. Choose the Resource you’ve created before the installation. After that click Next to continue.
If you haven’t added the resource yet, add it now. Click Add Resource and enter any Resource Name you wish.
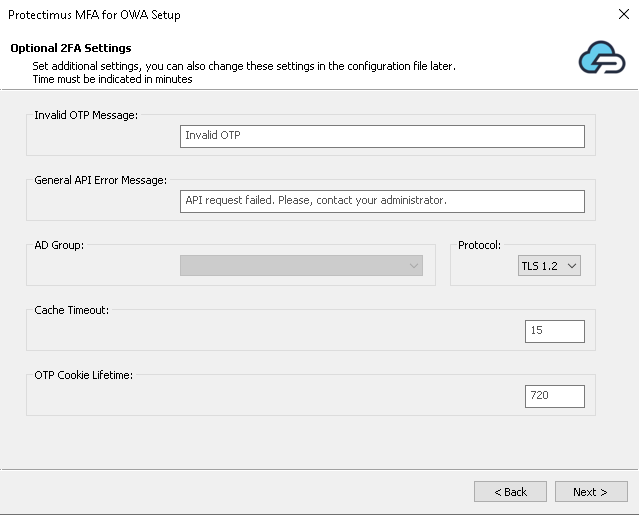
- Set additional settings:
- Invalid OTP Message – specify the message text for invalid OTP.
- General API Error Message – specify the API error message text.
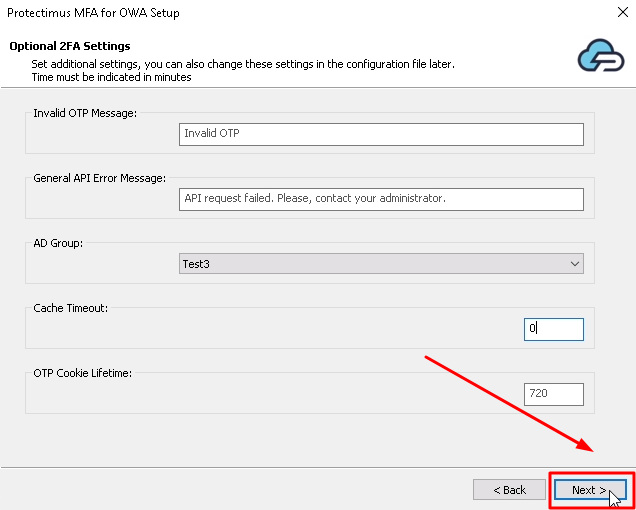
- AD Group – if you want to add two-factor authentication only for a specific AD group, select that AD group. By default, two-factor authentication will be enabled for all users.
- Protocol – specify information about the connection protocol. SSL3, TLS1, TLS1.2, and TLS1.3 are supported.
- Cache Timeout – specify how often Protectimus will contact Active Directory to check if the user requesting OWA access is added to AD. Time must be indicated in minutes. By default, the value is set to 15 minutes, which means that Protectimus will synchronize with Active Directory once every 15 minutes. If you specify a value of 0, the system will contact Active Directory every time a user logs in.
- OTP Cookie Lifetime – specify how often the end users will be asked to re-authenticate. Time must be indicated in minutes. By default, the value is set to 720 minutes (12 hours), which means that every 12 hours your users will be asked to enter their one-time passwords to continue working with OWA.
PLEASE NOTE! You can also change these settings in the configuration file later.
- Click Next to continue.
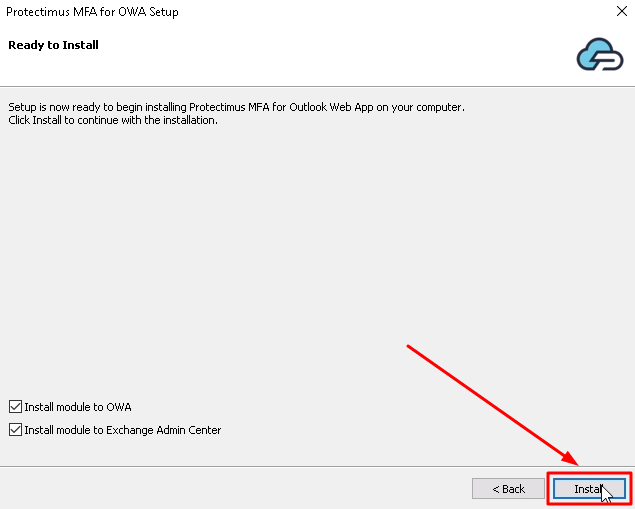
- Everything is ready for installation. Check the boxes for the modules you want to protect – OWA, Exchange Admin Center, or both of them. Then click Install.
3. Log in to Outlook Web App or EAC with Protectimus 2FA
- Open your Outlook Web App or Exchange Admin Center.
- Enter your Username and Passcode, and then click Login.
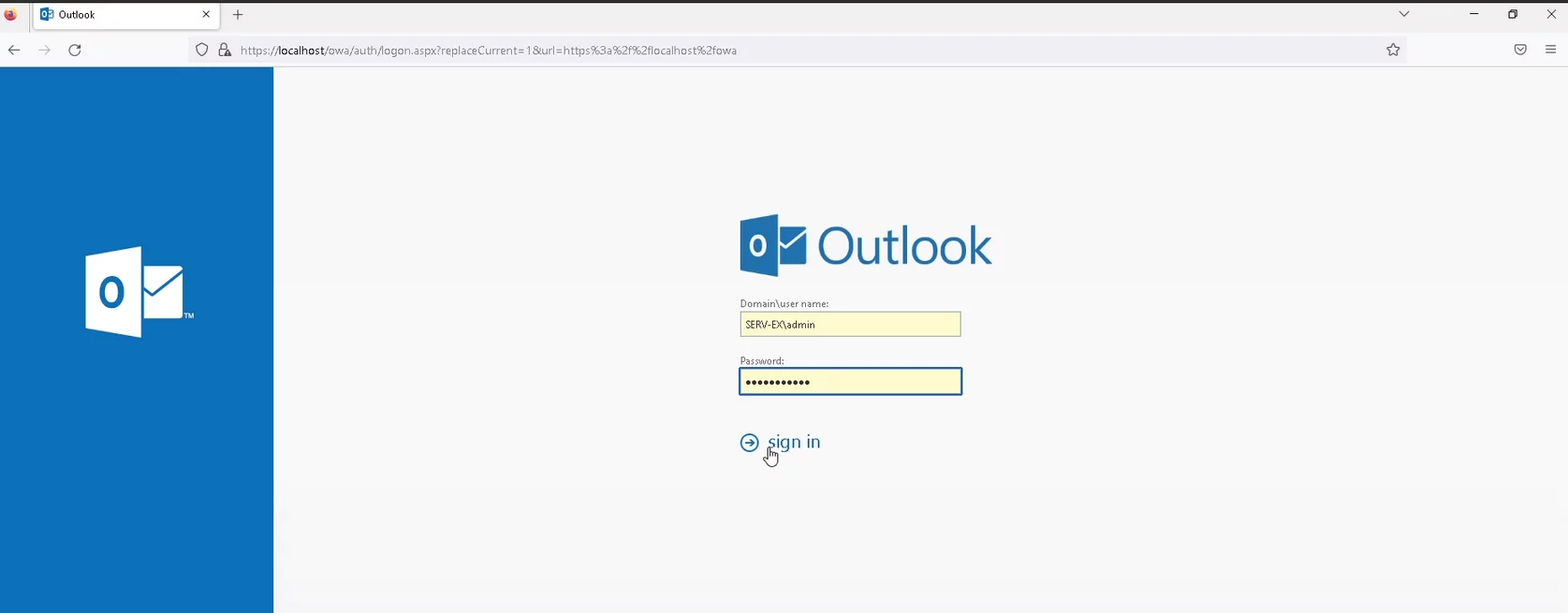
- Enter the one-time password from the two-factor authentication token.
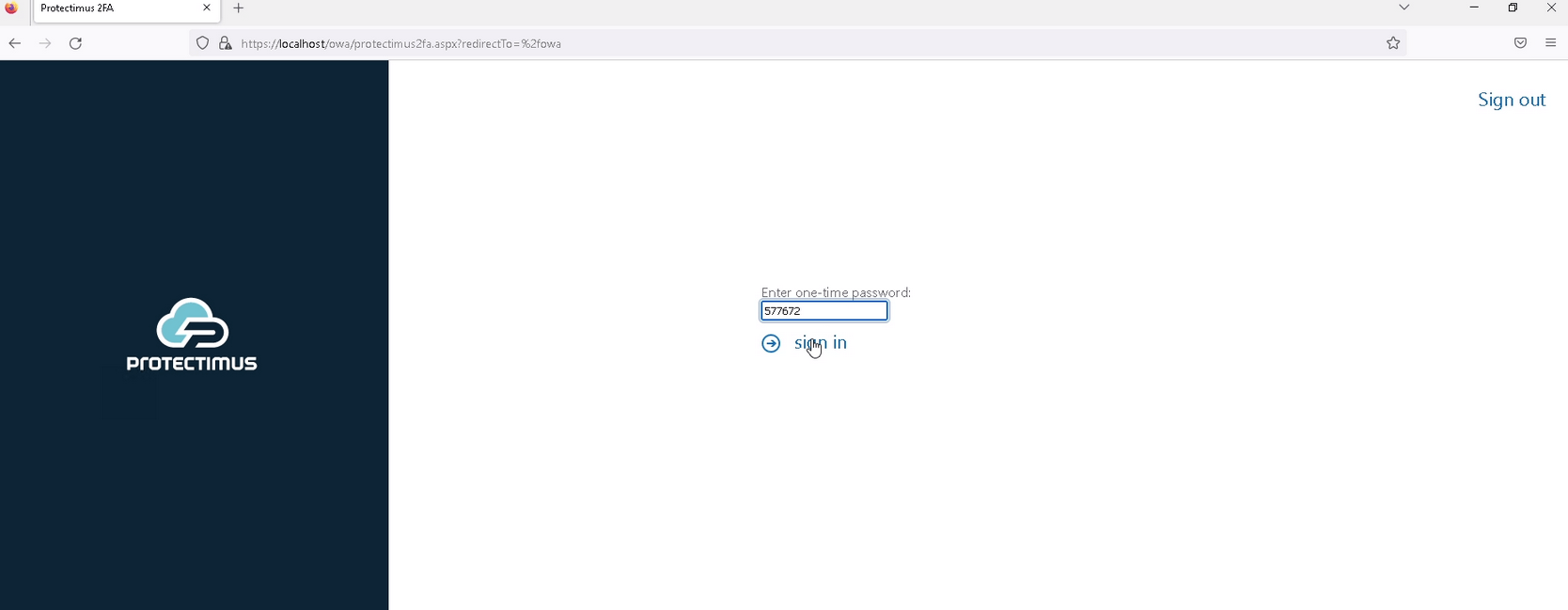
PLEASE NOTE! If you use an OCRA token, use the challenge you will see on the authentication page to generate a one-time password.
4. How to Change Settings
You can change any settings, including API URL, API key, Resource ID, Group settings and other optional settings, in the config file.The configuration file is usually located at the following path: C:\Program Files\Microsoft\Exchange Server\V15\ClientAccess\Owa
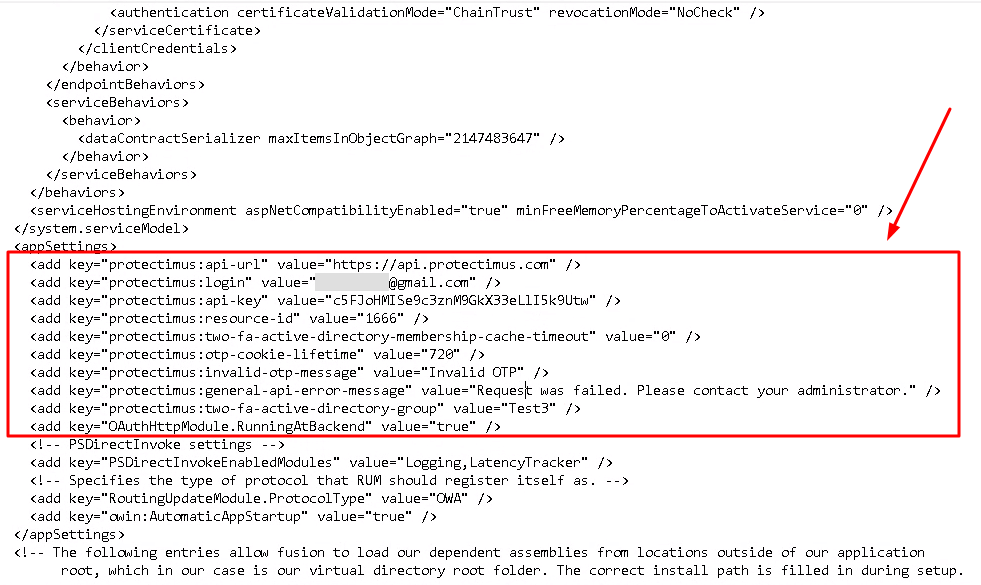
Integration of Outlook Web App with Protectimus 2FA solution is now complete. If you have other questions, contact our customer support service.
5. Username Format Configuration
The user login in the Protectimus service should be in the format of user@domain or DOMAIN\user, where user is the username in AD, and domain is your corporate domain.To transmit the user login in the desired format to the API, you can use the following parameter in the configuration file:
<add key="protectimus:is-owa-old-format" value="true" />The protectimus:is-owa-old-format parameter can have two values: true or false.
| PARAMETER VALUE | FUNCTION |
|
When the user enters the login in the format DOMAIN\user (netBiosName), the login is converted to the user@domain format (UserPrincipalName). |
|
When the user enters the login in the format user@domain, the login is converted to the DOMAIN\user format. |
|
The user’s login, entered during login, is transmitted to the API in its original format. |
Additionally, the user can enter the login in the format user@domain if the value is set to true, or DOMAIN\user if the value is set to false. In this case, no conversion will be performed as the login is already in the “correct” format.
Last updated on 2025-03-16
