> Deploying Two-Factor Authentication on Palo Alto GlobalProtect VPN
Deploying Two-Factor Authentication on Palo Alto GlobalProtect VPN
This guide shows how to enable two-factor authentication (2FA / MFA) for Palo Alto Networks VPN using the Protectimus Cloud 2FA Service or On-Premise 2FA Platform.
Protectimus integrates with Palo Alto GlobalProtect VPN via RADIUS authentication protocol to add two-factor authentication (2FA) to VPN logins.
In this scenario, the Protectimus two-factor authentication solution for Palo Alto GlobalProtect VPN 2FA performs as a RADIUS server, and the Palo Alto Networks VPN takes the role of a RADIUS client. You will find the scheme of work of the Protectimus solution for Palo Alto Networks VPN two-factor authentication below.
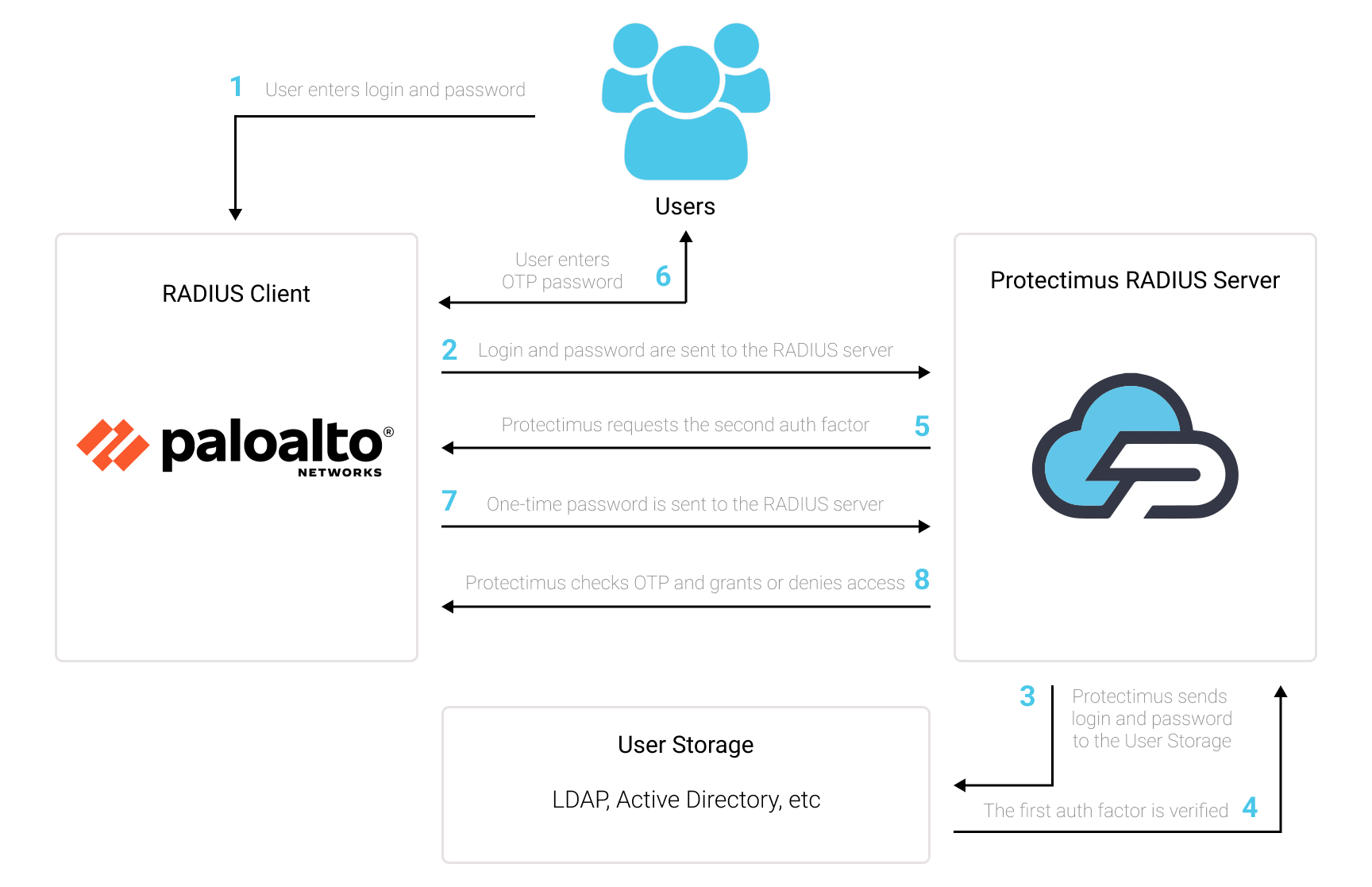
1. How Two-Factor Authentication (2FA) Works for Palo Alto Networks VPN
Two-factor authentication (2FA), also known as multi-factor authentication (MFA), is a must-have security measure for Palo Alto GlobalProtect VPN. 2FA will protect Palo Alto GlobalProtect VPN logins from such threats as phishing, brute force, data spoofing, social engineering, keyloggers, man-in-the-middle attacks, etc.And this is how two-factor authentication for Palo Alto GlobalProtect VPN works:
- When a user initiates login to the Palo Alto GlobalProtect VPN protected with two-factor authentication, first of all, they will enter the first authentication factor – their standard password and login (something they know).
- Then they will be asked to enter a second authentication factor – a one-time passcode from the two-factor authentication token (a 2FA token is something the user has – usually, it is a smartphone or a physical OTP token looking like a keyfob).
This way, to get access to the Palo Alto GlobalProtect VPN account protected with two-factor authentication, the fraudster has to get access to two authentication factors that differ in their nature. That is quite a challenging task. Moreover, a time-based one-time password remains active only for 30 seconds, which makes hacking way more complecated and almost impossible.
2. How to Enable Two-Factor Authentication (2FA) for Palo Alto Networks VPN
You can set up Palo Alto Networks VPN two-factor authentication (2FA) with Protectimus using the RADIUS protocol:
- Get registered with Protectimus SAAS Service or install the On-Premise 2FA Platform and configure basic settings.
- Install and configure Protectimus RADIUS Server.
- Configure Palo Alto Networks VPN authentication policies.
2.1. Get Registered and Configure Basic Protectimus Settings
- Register with the Protectimus Cloud Service and activate API or install the Protectimus On-Premise Platform (if you install Protectimus Platform on Windows, check the RProxy box during the installation).
- Add Resource.
- Add Users.
- Add Tokens or activate Users’ Self Service Portal.
- Assign Tokens to Users.
- Assign Tokens with Users to the Resource.
2.2. Install and Configure Protectimus RADIUS Server
Detailed instructions for installing and configuring the Protectimus RADIUS Server for Palo Alto Global Protect VPN 2FA using RADIUS are available here.2.3. Configure Palo Alto Networks RADIUS Server Profile
- Log in to the Palo Alto Networks administrative interface.
- On the Device tab, navigate to Server Profiles, then RADIUS.
- Click the Add button to add a new RADIUS server profile. You will see the following window:
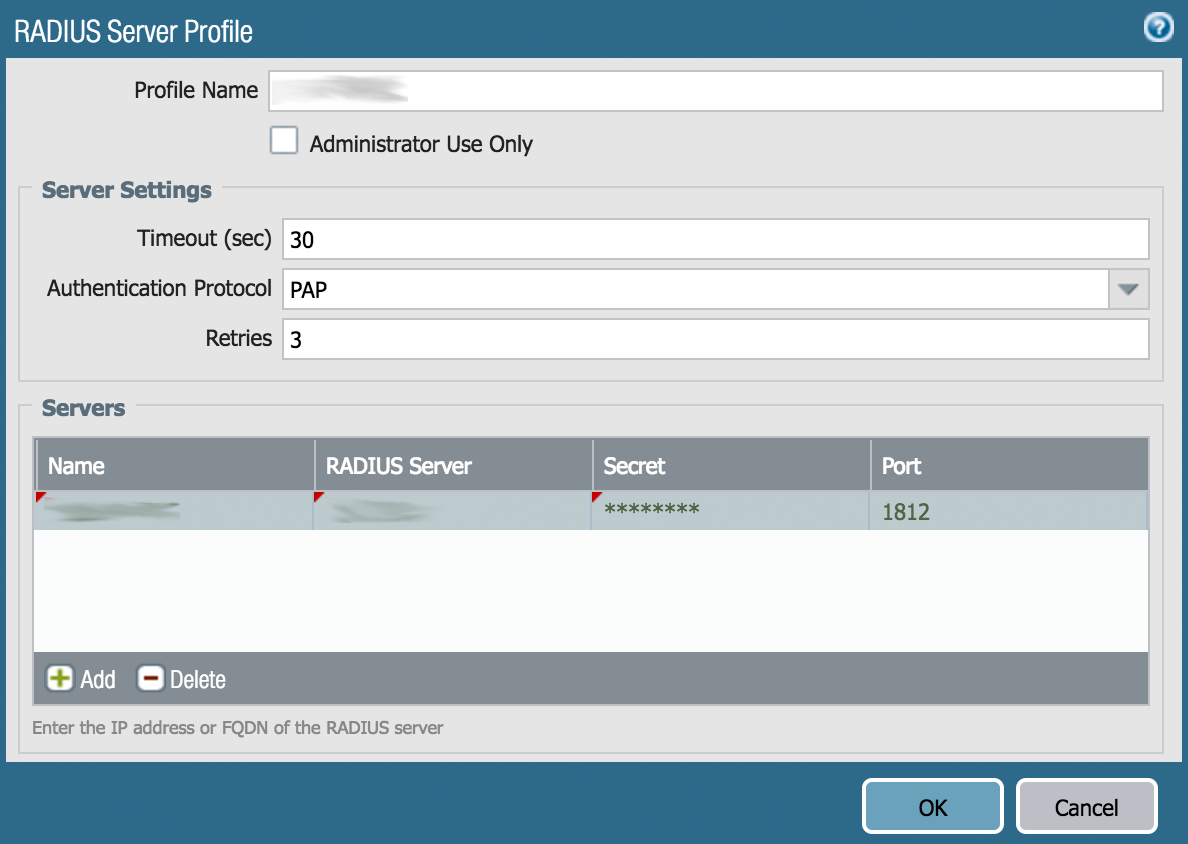
- In the Profile Name field come up with a name for your RADIUS server, enter Protectimus RADIUS or any other name you wish.
- Increase the Timeout to at least 30 seconds.
- Change the Authentication Protocol to PAP.
PLEASE NOTE! PAN-OS 7.x users must set the protocol in the CLI with this command:
set authentication radius-auth-type pap
- Click on Servers –> Add button, to add a RADIUS server. After this, enter the below information:
| Server | Type any name for your RADIUS server – enter Protectimus RADIUS or any other name you wish. |
| RADIUS Server | IP of server where the Protectimus RADIUS Server component is installed. |
| Secret | Indicate the shared secret you created in the Protectimus radius.yml file (radius.secret property) when configuring Protectimus RADIUS Server |
| Port | Indicate 1812 (or whichever port you configured in the Protectimus radius.yml file when configuring Protectimus RADIUS Server). |
- Click OK and save the new RADIUS server profile.
2.4. Create an Authentication Profile in Palo Alto Networks
- Go to the Device tab and navigate to Authentication Profile.
- Click on Add to create a new authentication profile, you will see the following window:
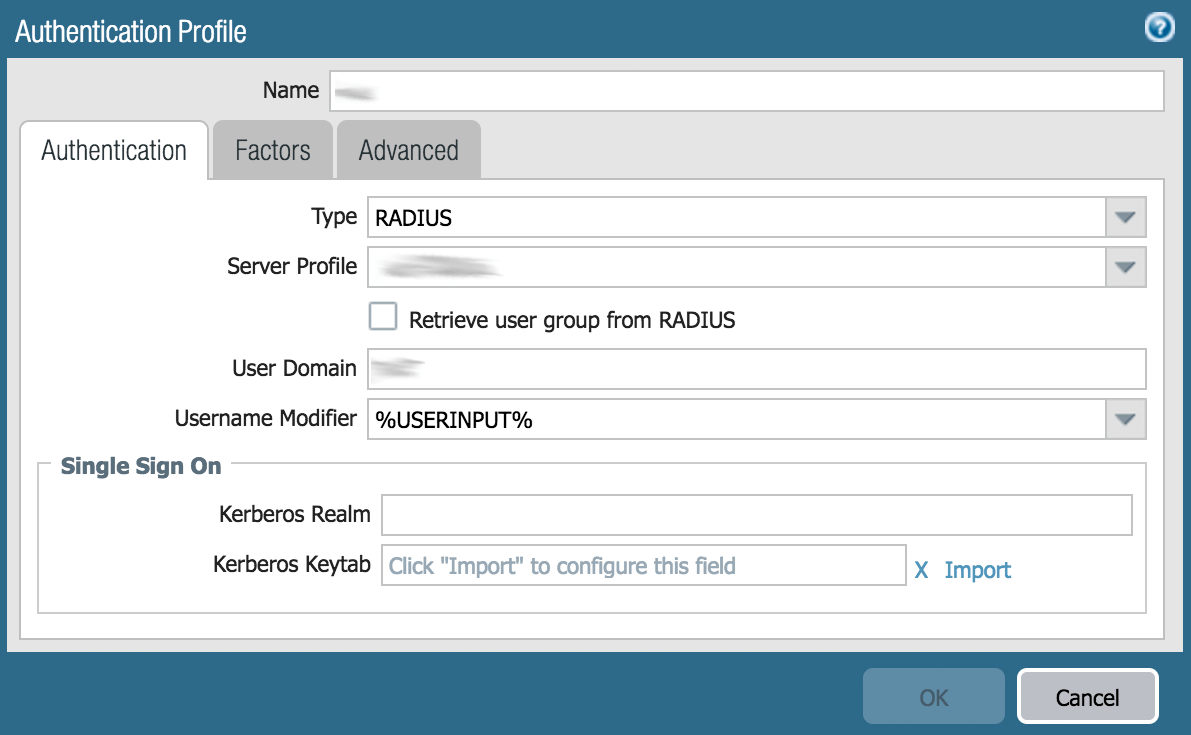
- Enter the following data:
| Name | Type PROTECTIMUS ot choose any name you wish. |
| Type | Select RADIUS from the drop-down list |
| Server Profile | Select Protectimus RADIUS from the drop-down list (or whatever name used to create the RADIUS Server Profile in Step 2.3.) |
- Keep the rest of the options on the current screen as their defaults.
- Then click the Advanced tab and select the all group or choose a specific group to which this authentication profile will apply.
- Click OK and save the Authentication profile you have created.
2.5. Assign the Authentication Profile to the GlobalProtect Portal and/or Gateway.
You can configure multiple client authentication configurations for the Palo Alto GlobalProtect portal and gateways. For each client authentication configuration, you can specify the Authentication Profile to apply to endpoints of a specific OS.This step describes how to add the Authentication Profile to the Palo Alto GlobalProtect VPN portal or gateway configuration. For additional details on setting up these components, see the PaloAlto Networks documentation on GlobalProtect Portals and GlobalProtect Gateways.
- Go to Network –> GlobalProtect –> Gateways or Portals.
- Click on your configured GlobalProtect Gateway to bring up the properties window.
- In the newly-opened window, select the Authentication tab.
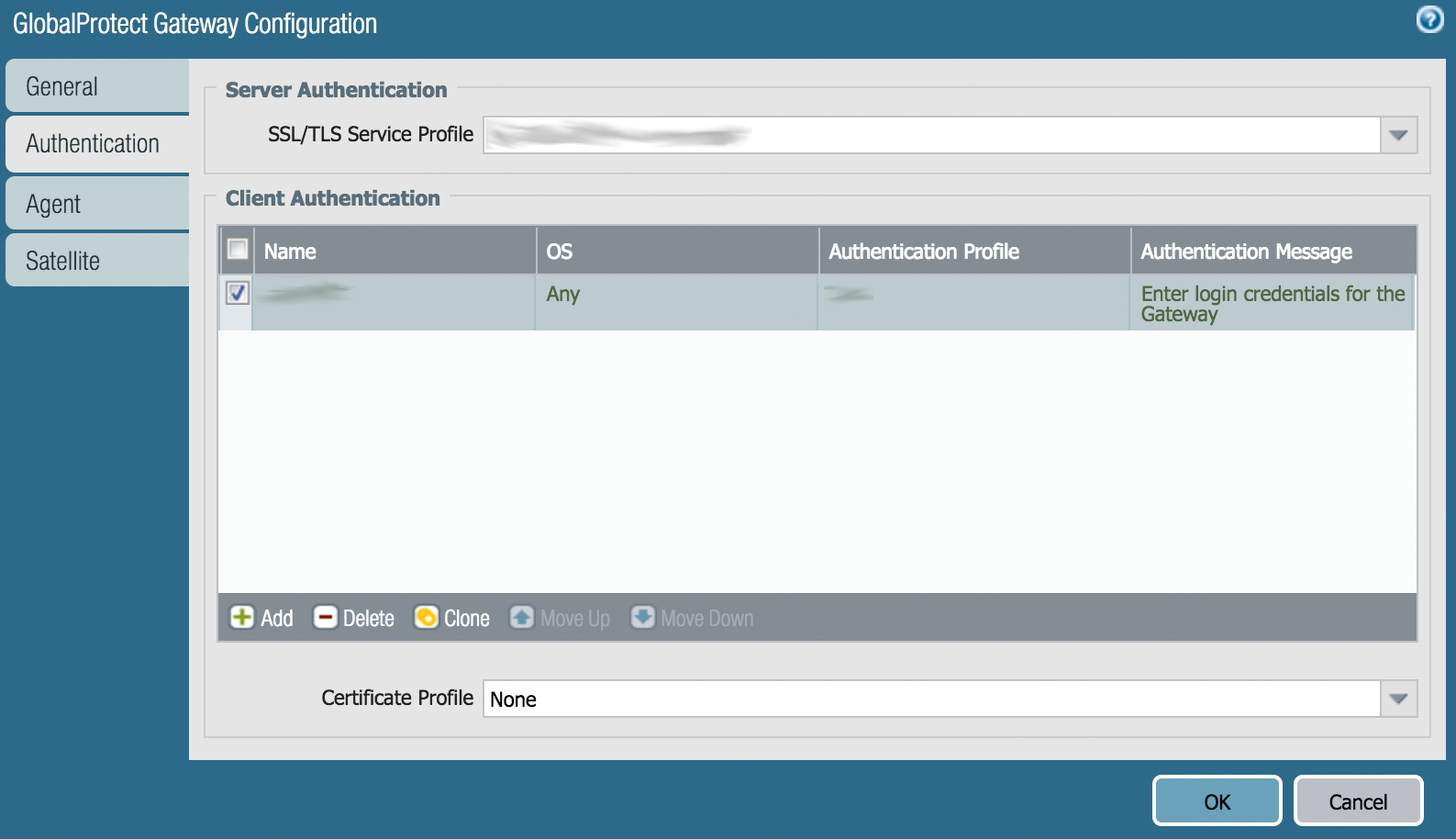
- Select an SSL/TLS Service Profile or Add a new one.
- Depending on your configuration, click the current entry under Client Authentication to modify it or create a new one by clicking the Add button.
- Fill in the Client Authentication form with the following information.
| Name | Enter any descriptive name you wish. |
| OS | Any |
| Authentication Profile | Select the Authentication Profile you have created in Step 2.4. |
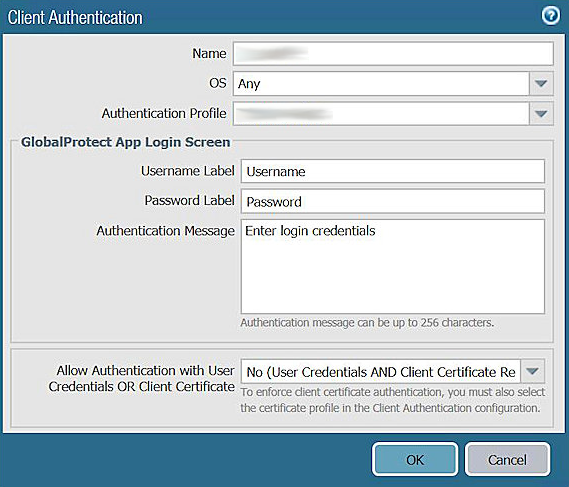
- Click OK to save the configuration.
