> Deploying Two-Factor Authentication on F5 BIG-IP APM VPN
Deploying Two-Factor Authentication on F5 BIG-IP APM VPN
This guide shows how to enable multi-factor authentication (MFA / 2FA) for F5 BIG-IP APM VPN with the help of the Protectimus two-factor authentication system.
Protectimus two-factor authentication system integrates with F5 BIG-IP APM VPN via RADIUS authentication protocol. In this scenario, the Protectimus Cloud 2FA Service or On-Premise 2FA Platform takes the role of a RADIUS server, and the F5 BIG-IP VPN performs of a RADIUS client.
The scheme of work of the Protectimus solution for F5 BIG-IP APM VPN 2FA is presented below.
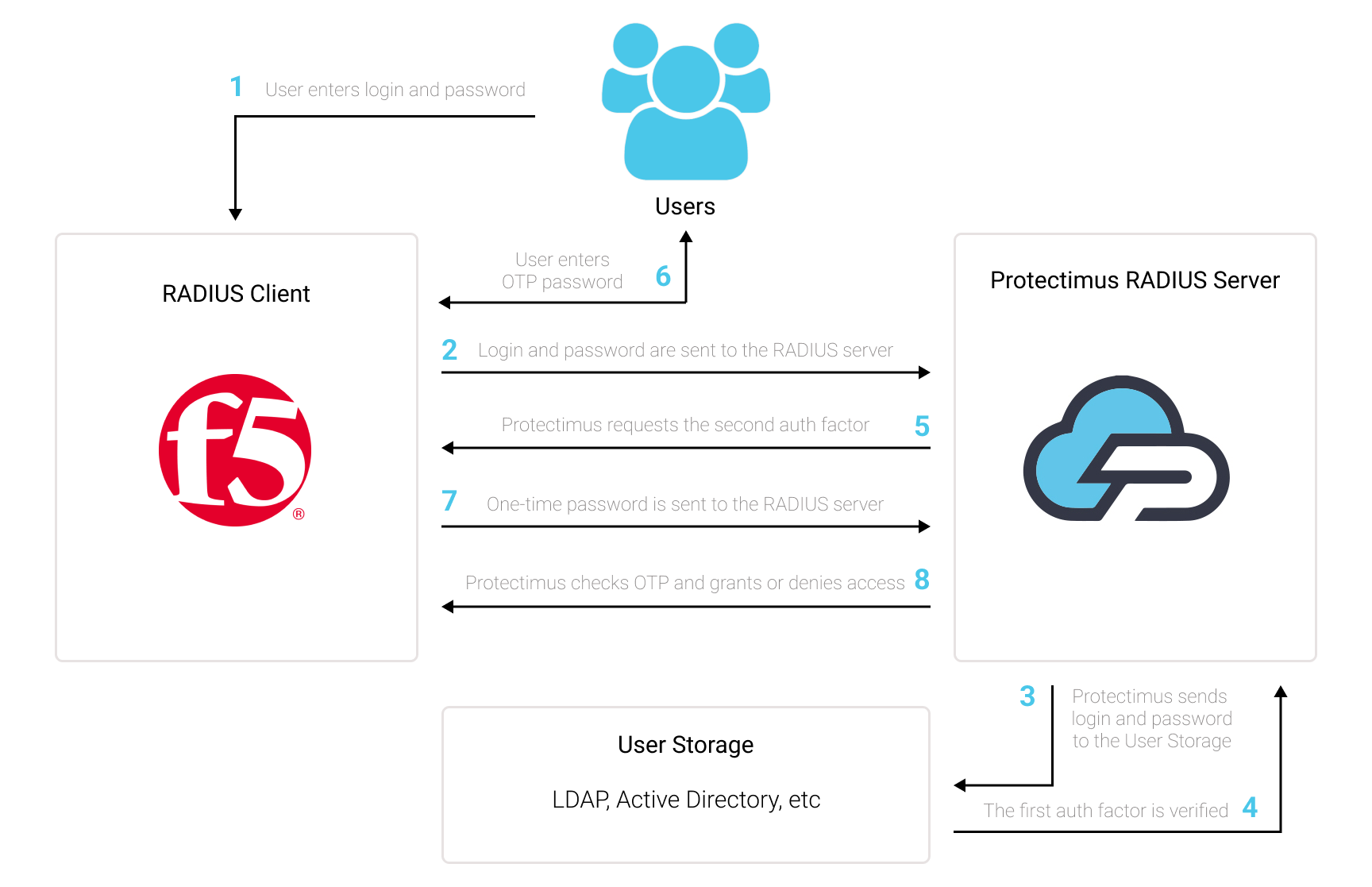
1. How F5 BIG-IP APM VPN Two-Factor Authentication Works
Protectimus Two-Factor Authentication Solution for F5 BIG-IP APM VPN allows you to add an extra layer of security to your F5 BIG-IP VPN logins.When you add 2FA/MFA for F5 VPN, your users will use two different authentication factors to get access to their accounts.
- The first factor is login and password (something the user knows);
- The second factor is a one-time password generated with the help of a hardware OTP token or an app on the smartphone (something the user owns).
To hack an F5 BIG-IP APM VPN protected with two-factor authentication, a hacker needs to get a standard password and a one-time password at once. And they only have 30 seconds to hack a one-time password. It is almost impossible, which makes two-factor authentication so effective against brute force, data spoofing, keyloggers, phishing, man-in-the-middle attacks, social engineering, and similar hacking attacks.
2. How to Enable 2FA for F5 BIG-IP APM VPN
You can set up multi-factor authentication (2FA) for F5 BIG-IP VPN with Protectimus using the RADIUS protocol:
- Get registered with Protectimus SAAS Service or install the On-Premise 2FA Platform and configure basic settings.
- Install and configure Protectimus RADIUS Server.
- Add Protectimus as RADIUS Server for F5 BIG-IP APM VPN.
2.1. Get Registered and Configure Basic Protectimus Settings
- Register with the Protectimus Cloud Service and activate API or install the Protectimus On-Premise Platform (if you install Protectimus Platform on Windows, check the RProxy box during the installation).
- Add Resource.
- Add Users.
- Add Tokens or activate Users’ Self Service Portal.
- Assign Tokens to Users.
- Assign Tokens with Users to the Resource.
2.2. Install and Configure Protectimus RADIUS Server
Detailed instructions for installing and configuring the Protectimus RADIUS Server for F5 BIG-IP APM VPN two-factor authentication using RADIUS are available here.2.3. Add Protectimus as RADIUS Server for F5 BIG-IP APM VPN 2FA
- Log into the F5 BIG-IP administrator dashboard.
- Navigate to Access –> Authentication –> RADIUS.
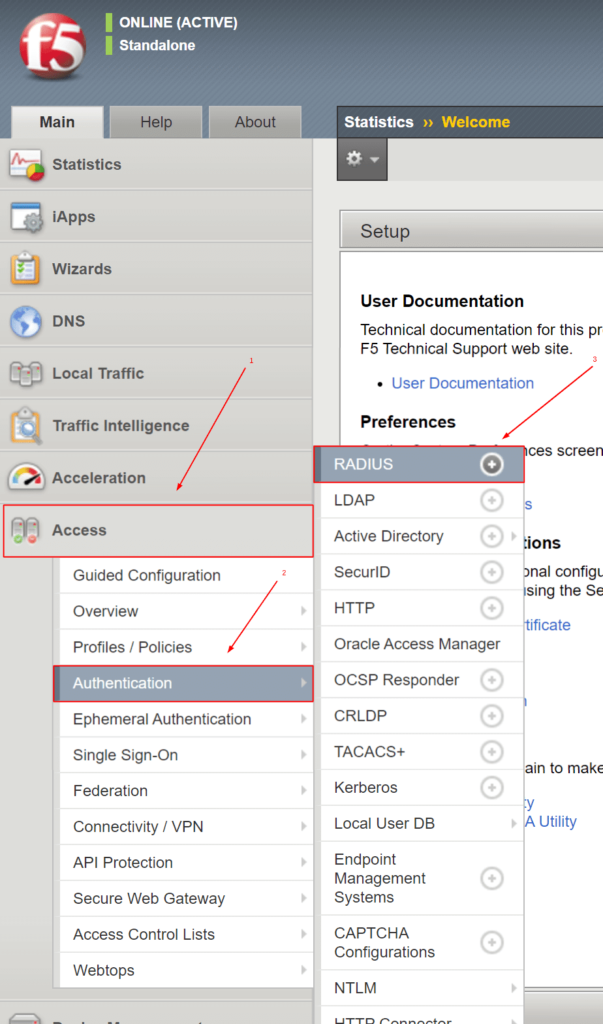
- Click the Create… button to add a new RADIUS server.
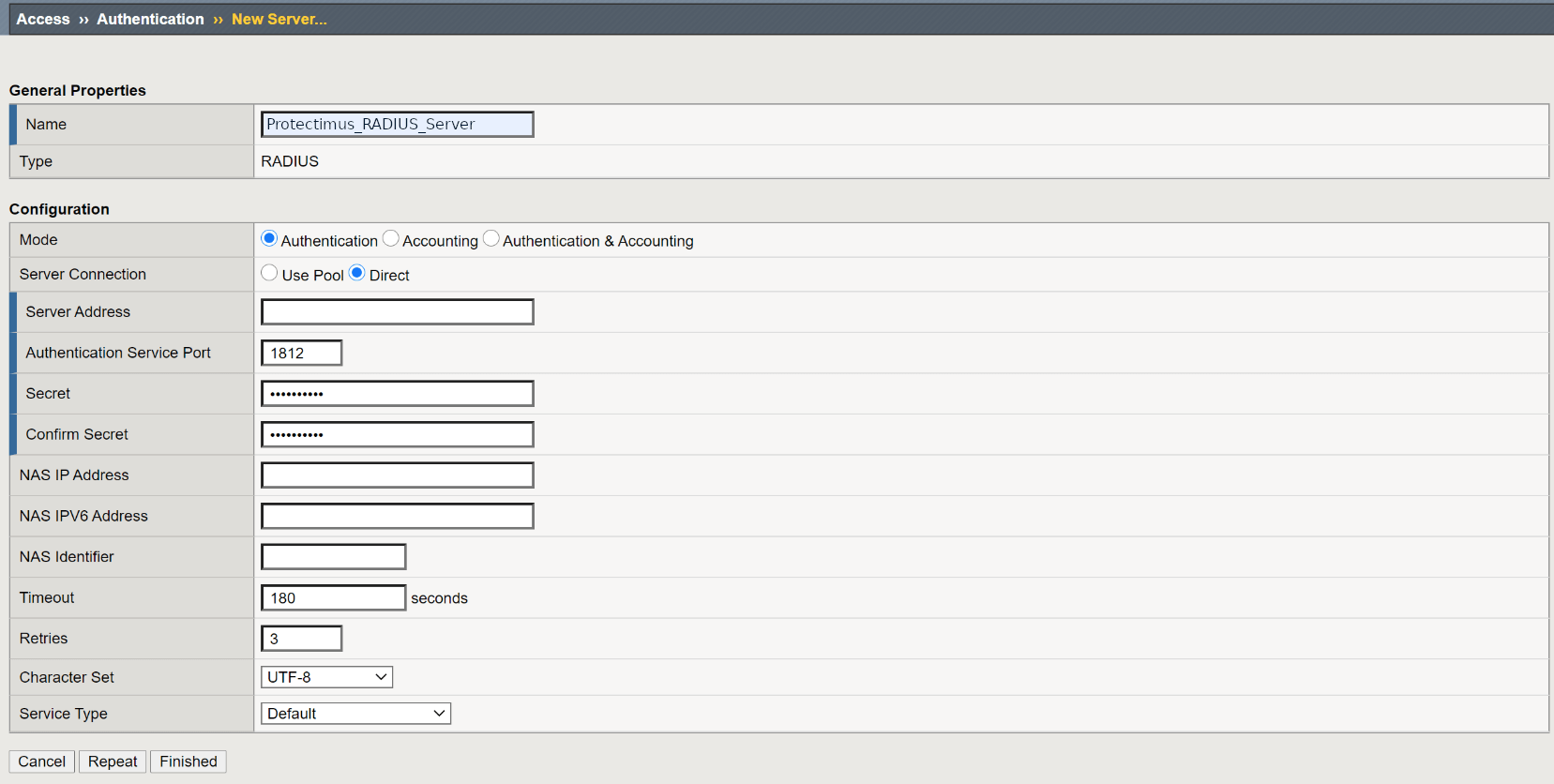
- Then fill in the form referring to the table and image below, and click Finished to save your settings.
| Name | Type any name for your RADIUS server – enter Protectimus_RADIUS_Server or any other name you wish. |
| Mode | Authentication |
| Server Connection | Direct |
| Server Address | Enter the IP of server where the Protectimus RADIUS Server component is installed. |
| Authentication Service Port | Indicate 1812 (or whichever port you configured in the Protectimus radius.yml file when configuring Protectimus RADIUS Server). |
| Secret | Indicate the shared secret you created in the Protectimus radius.yml file (radius.secret property) when configuring Protectimus RADIUS Server |
| Confirm Secret | Confirn the shared secret. |
| Timeout | Set to 180 seconds. |
| Retries | Set to 3. |
| Character Set | Set to UTF-8. |
| Service Type | Default. |
2.4. Modify the F5 BIG-IP APM Access Policy
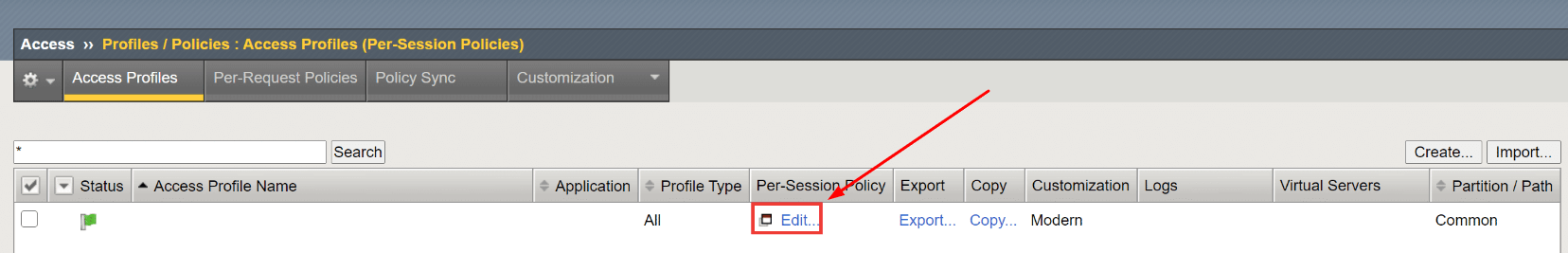
- Navigate to Access –> Profiles/Policies –> Access Profiles (Per-Session Policies).
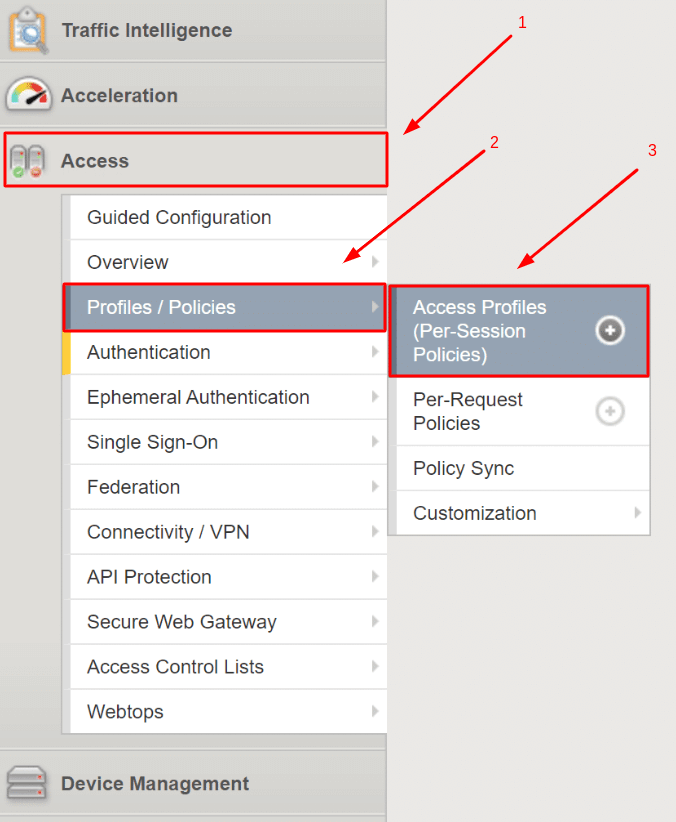
- Click Edit… to modify your F5 BIG-IP APM access policy.
- You will see the Access Policy editor. Click + (Plus) on the arrow to the right of the Logon Page.
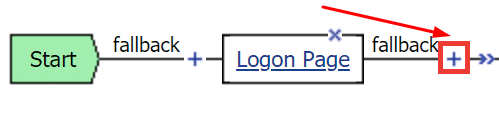
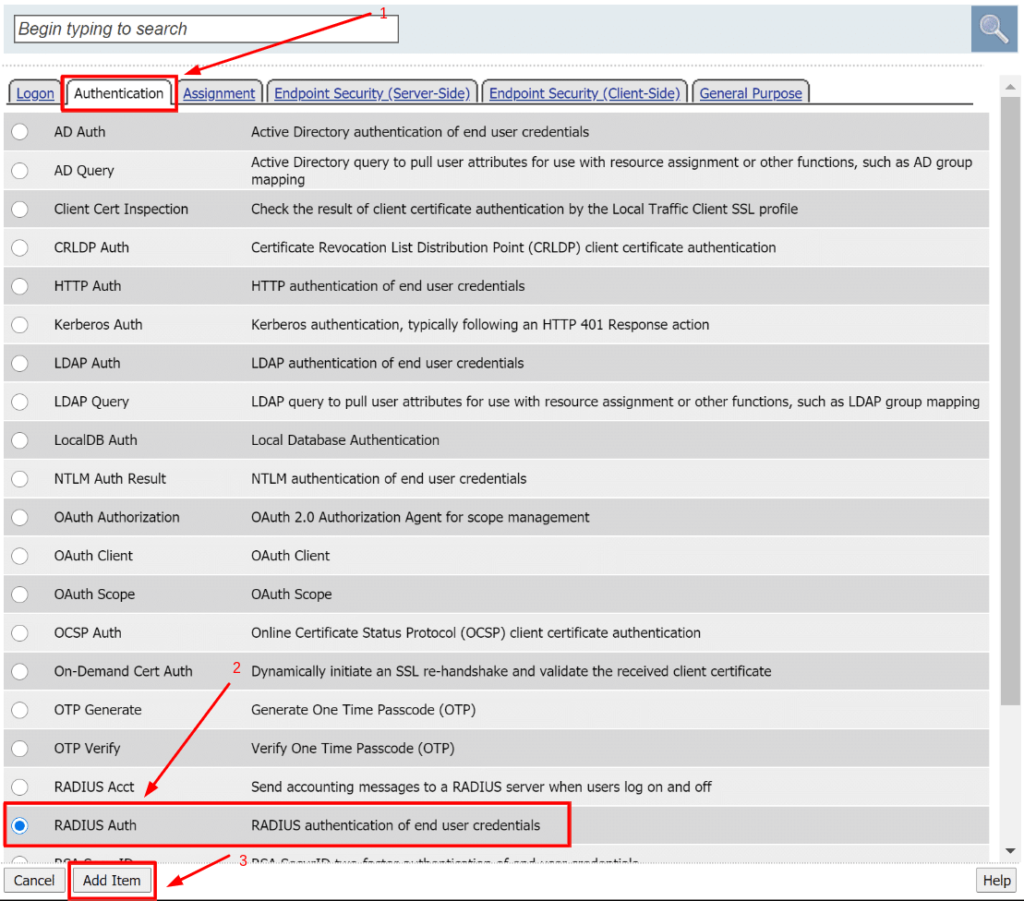
- In a new window, select the Authentication tab. The select RADIUS Auth and click the Add Item button.
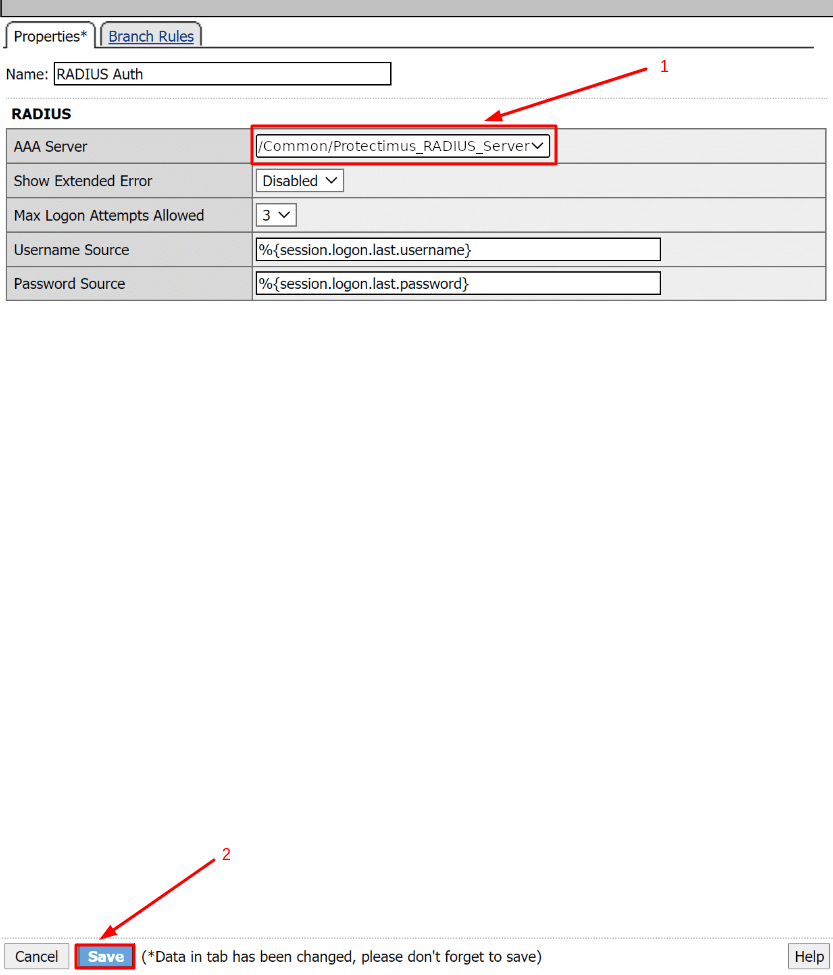
- In the AAA Server dropdown, select Protectimus_RADIUS_Server – the server you have created previously. Then click Save to save the changes.
PLEASE NOTE!
If you have a former authentication method (e.g. Active Directory) you can either remove it or keep it.
You can keep your former authentication method and use Protectimus after or before that authentication method.
To remove it, click X, select Connect previous node to Successful branch, and click Delete.
- Click Close to return to the Access Profiles page. Check your profile and click Apply. The status flag next to your profile should change to green.
Integration of two-factor authentication (2FA/MFA) for your F5 BIG-IP APM VPN 2FA is now complete. If you have other questions, contact Protectimus customer support service.
Last updated on 2025-03-17
