Authentication & Verification
Classic 2FA / MFA
MFA for AD, LDAP, Databases
Wi-Fi Authentication
Electronic Visit Verification
Popular Integrations
Popular Integrations
Programmable hardware TOTP token in a card format that fits any authentication system
Classic hardware TOTP token with SHA-1 algorithm support
Programmable hardware TOTP token in a key fob format that fits any authentication system
Classic hardware TOTP token with SHA-256 algorithm support
Programmable hardware TOTP token in a card format that fits any authentication system
Classic hardware TOTP token with SHA-1 algorithm support
Programmable hardware TOTP token in a key fob format that fits any authentication system
Classic hardware TOTP token with SHA-256 algorithm support
A free 2FA authenticator app with cloud backup, easy token transfer to a new phone, PIN and biometric authentication protection
Free OTP delivery with chatbots in messaging apps
Delivery of one-time passwords via SMS messages
Free delivery of one-time passwords via email
Free one-time passwords delivery via push notifications
A free 2FA authenticator app with cloud backup, easy token transfer to a new phone, PIN and biometric authentication protection
Free OTP delivery with chatbots in messaging apps
Delivery of one-time passwords via SMS messages
Free delivery of one-time passwords via email
Free one-time passwords delivery via push notifications
Get Started
Classic 2FA / MFA
API Documentation
Software Development Kits
Get Started
Classic 2FA / MFA
API Documentation
Software Development Kits
Please Note:
- The certificate of Certification Authority (CA) has to be installed on the clients machines in your domain to integrate the On-Premise Platform with such solutions as OWA.
- The Common Name (CN) for which the certificate was issued has to be accessible in your domain to integrate the On-Premise Platform with such solutions as OWA.
Prerequisites:
- AD CS installed with Web Enrollment feature.
- You need to have access to the Web Server template in certsrv.
- Keytool and OpenSSL tools are required.
openssl genrsa -out test-server.key 2048openssl req -new -key test-server.key -out test-server.csrhttp://CA-Server-Name/certsrv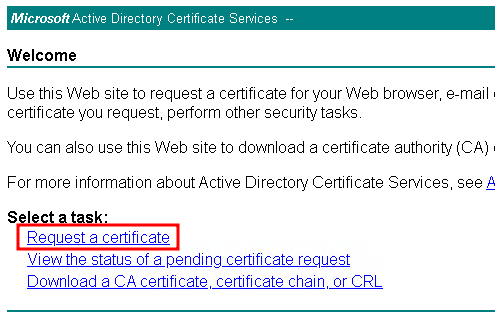
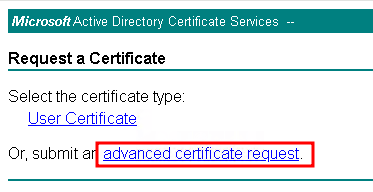
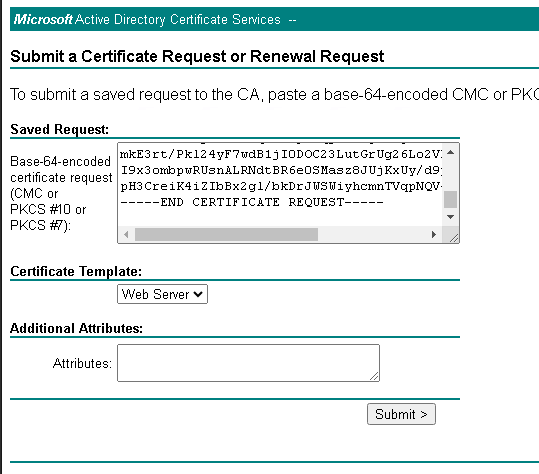
To import the issued certificate, follow the instructions in the “2. How to Import Trusted SSL Certificate” section.
openssl pkcs12 -export -in test-server.cer -inkey test-server.key -out test-server.pfxkeytool -importkeystore -srckeystore test-server.pfx -srcstoretype PKCS12 -destkeystore “C:\Program Files\Protectimus\Platform\keystore.jks” -deststoretype JKS| PROPERTY NAME | PROTERTY STANDS FOR |
|
Port on which your application listens for HTTPS requests. Typically, platform uses port 8443 by default. |
|
Type of keystore used to store SSL certificates and private keys. Types: JKS, PKCS12. |
|
Password required to access the keystore. |
|
Full path to the keystore file containing SSL certificates and private keys. Please note that the keystore file should be located in the ..\\Protectimus\\Platform folder, in the same place as the .war and .properties files. The path should be indicated with double backslashes, for example C:\\Program Files\\Protectimus\\Platform\\keystore.jks. |
https.port = 8443
https.keystore.type = JKS
https.keystore.password = **********
https.keystore = C:\\Program Files\\Protectimus\\Platform\\keystore.jks| PROPERTY NAME | PROTERTY STANDS FOR |
|
SMTP server’s hostname or IP address. |
|
Port number for SMTP server. |
|
Username or email account for authentication. |
|
Password associated with the username or email account. |
|
Allows you to set the address from which emails will be sent to the user. |
smtp.host = smtp-server.com
smtp.port = 25
smtp.user = user@example.com
smtp.password = **********PLEASE NOTE! Additionally, you can configure settings for SMSC and ALIBABA as well.
| PROPERTY NAME | PROTERTY STANDS FOR |
|
SMPP server login. |
|
SMPP server password. |
|
Host or IP address of the SMPP server. |
|
Port for the SMPP server. |
|
Encoding for SMPP messages. |
|
Source or sender address for SMPP messages. |
smpp.server.login = login
smpp.server.password = **********
smpp.server.host = smpp.example.com
smpp.server.port = 12000
smpp.message.encoding = UTF-8
smpp.from.address = ProtectimusProtectimus Ltd
Carrick house, 49 Fitzwilliam Square,
Dublin D02 N578, Ireland
Ireland: +353 19 014 565
USA: +1 786 796 66 64
Protectimus Ltd
Carrick house, 49 Fitzwilliam Square,
Dublin D02 N578, Ireland
Ireland: +353 19 014 565
USA: +1 786 796 66 64


