> Implementing Two-Factor Authentication in Cisco Meraki Client VPN
Implementing Two-Factor Authentication in Cisco Meraki Client VPN
Integrating Protectimus’s multi-factor authentication solution enables a straightforward setup for Cisco Meraki Client VPN two-factor authentication (2FA), requiring just a few minutes to configure. By implementing MFA as an extra security layer, the Cisco Meraki Client VPN system ensures that only authorized users can access it, significantly enhancing protection against potential cyber threats.
In the current era of widespread remote work, establishing a secure remote access system is of paramount importance. Protectimus offers a multifactor authentication solution for Cisco Meraki Client VPN, guaranteeing that even if a user’s login credentials are compromised, their access to the VPN remains safeguarded. Two-factor authentication serves as a strong defense against various cyber threats, including phishing, brute force, social engineering, MITM, and data spoofing attacks, thereby ensuring the security of your organization’s data and resources.
Protectimus allows secure access to your Cisco Meraki Client VPN by providing multi-factor authentication (MFA) using the Protectimus RADIUS server.
The scheme of work of the Protectimus solution for Cisco Meraki Client VPN two-factor authentication is presented below.
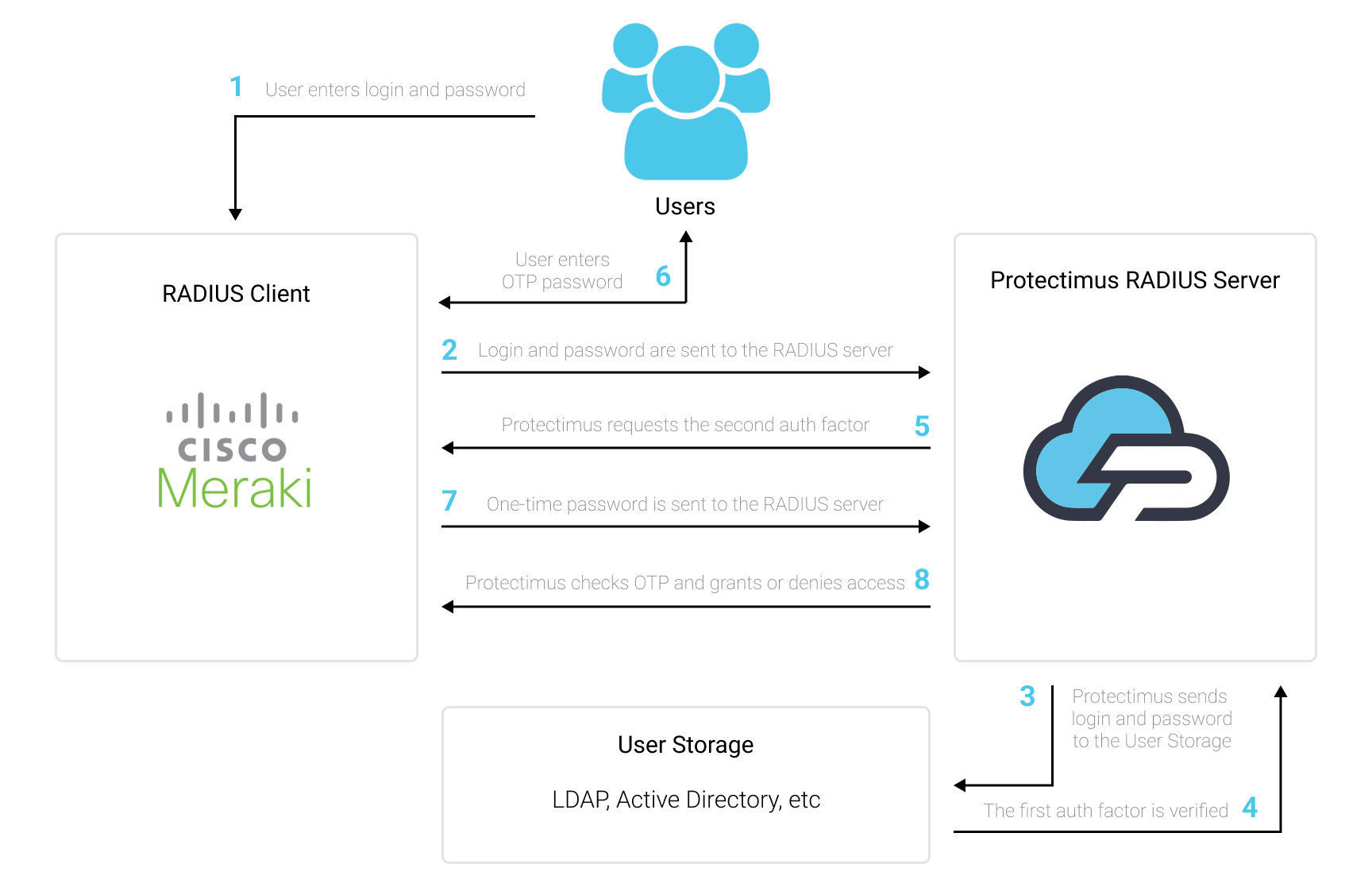
1. How Cisco Meraki Client VPN 2FA Works
Protectimus’ Two-Factor Authentication Solution for Cisco Meraki Client VPN adds an additional layer of security, effectively thwarting unauthorized access attempts to your VPN.Upon enabling two-factor authentication (2FA) on your Cisco Meraki Client VPN server, users will be required to provide two separate authentication factors to access their accounts.
When implementing 2FA/MFA for Cisco Meraki VPN, users will need to provide:
- The first factor, which is their username and password (something the user knows);
- The second factor, which is a one-time password generated using a hardware OTP token, 2FA chatbot or a smartphone app (something the user possesses).
To compromise a Cisco Meraki Client VPN protected by two-factor authentication (2FA/MFA), a hacker would need to obtain both a standard password and a one-time password simultaneously, with only a 30-second window to intercept the latter. This nearly impossible task highlights the remarkable effectiveness of two-factor authentication against most hacking attempts.
2. How to Enable 2FA for Cisco Meraki Client VPN
You can set up multi-factor authentication (2FA) for Cisco Meraki with Protectimus using the RADIUS protocol:
- Get registered with Protectimus SAAS Service or install the On-Premise 2FA Platform and configure basic settings.
- Install and configure Protectimus RADIUS Server.
- Add Protectimus as RADIUS Server for Cisco Meraki Client VPN.
2.1. Get Registered and Configure Basic Protectimus Settings
- Register with the Protectimus Cloud Service and activate API or install the Protectimus On-Premise Platform (if you install Protectimus Platform on Windows, check the RProxy box during the installation).
- Add Resource.
- Add Users.
- Add Tokens or activate Users’ Self Service Portal.
- Assign Tokens to Users.
- Assign Tokens with Users to the Resource.
2.2. Install and Configure Protectimus RADIUS Server
Detailed instructions for installing and configuring the Protectimus RADIUS Server for Cisco Meraki VPN 2-factor authentication using RADIUS are available here.2.3. Add Protectimus as RADIUS Server for Cisco Meraki VPN MFA
- In the Cisco Meraki Dashboard, navigate to Security & SD-WAN, and then select the Client VPN option.
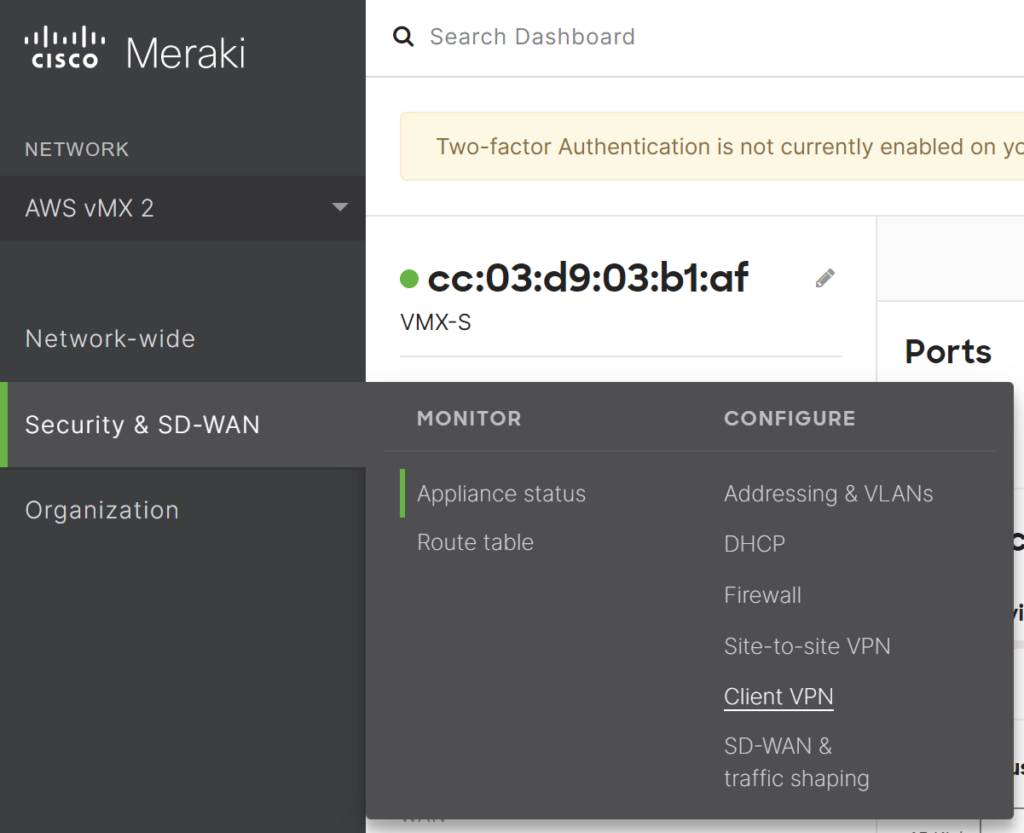
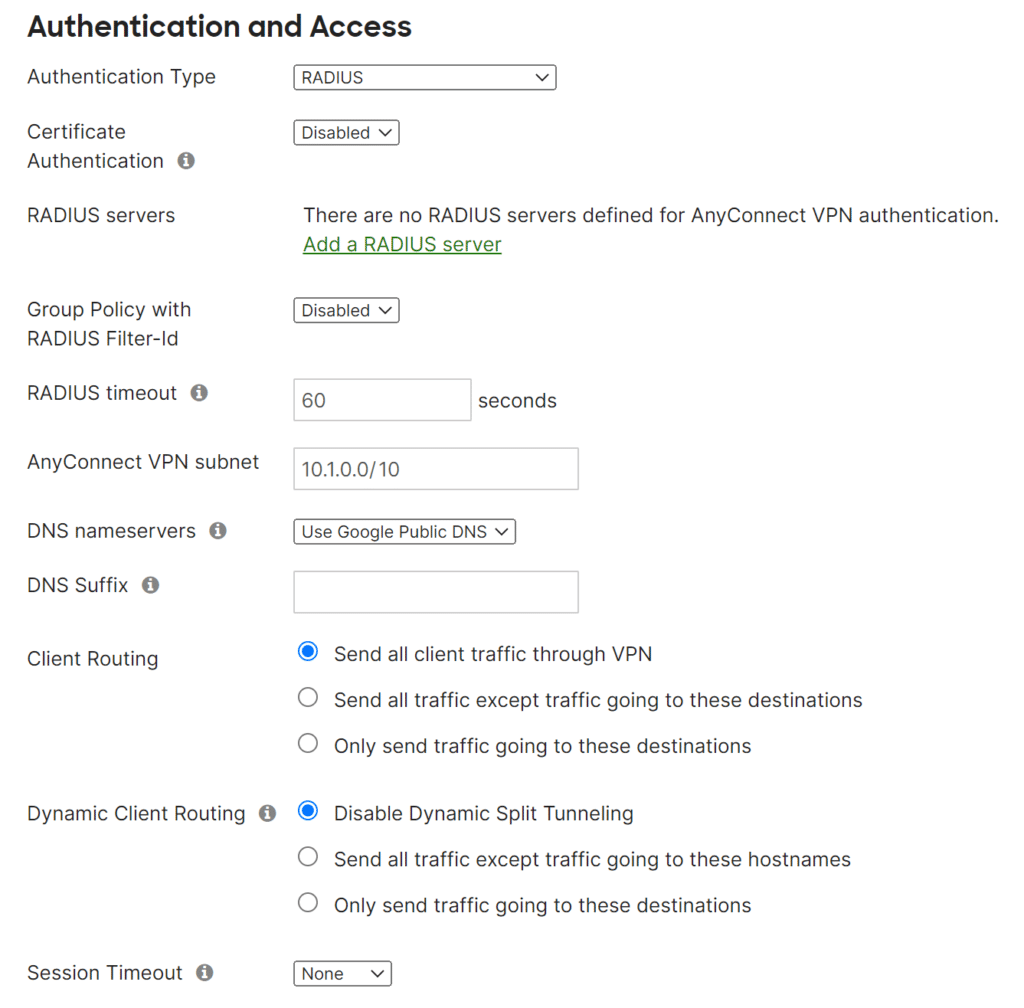
- Choose AnyConnect Settings, proceed to the Authentication and Access section, and configure the following:
- Authentication Type: RADIUS.
- RADIUS servers: The subsequent step will explain how to add a RADIUS server.
- RADIUS timeout: 60 seconds.
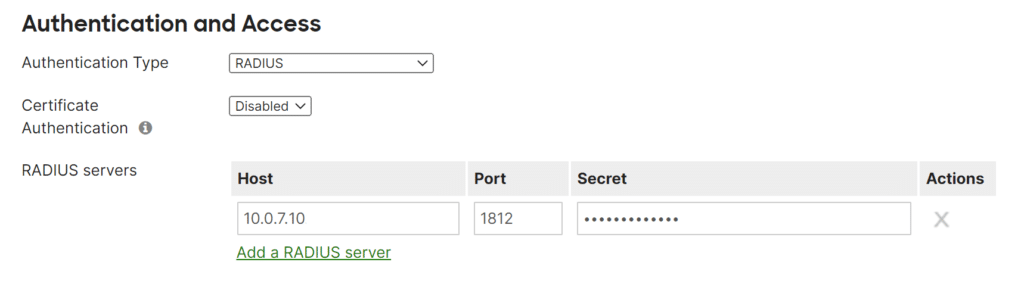
- Within the RADIUS servers section, proceed to click on Add a RADIUS server and configure the following:
- Host: Enter the IP of server where the Protectimus RADIUS Server component is installed.
- Port: Indicate 1812 (or whichever port you configured in the Protectimus radius.yml file when configuring Protectimus RADIUS Server).
- Secret: Enter the shared secret you created in the Protectimus radius.yml file (radius.secret property) when configuring Protectimus RADIUS Server.
Integration of two-factor authentication (2FA/MFA) for your Cisco Meraki VPN is now complete. If you have other questions, contact Protectimus customer support service.
