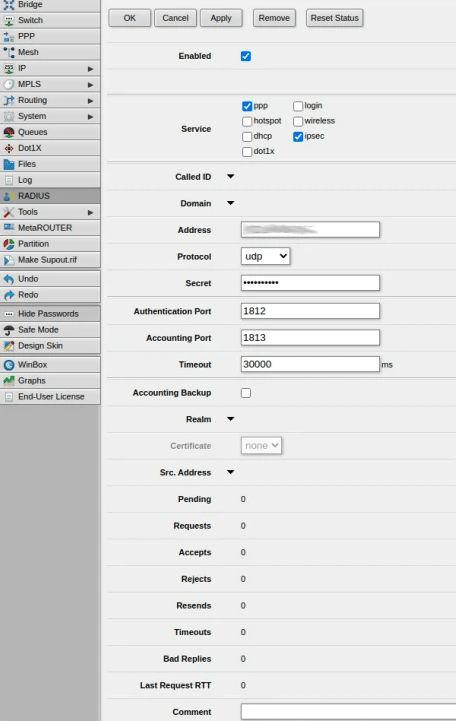
How Does Protectimus Smart 2FA App Work
Protectimus Smart OTP is a two-factor authentication app that provides an additional layer of security to your online accounts. With the Protectimus Smart OTP 2FA authenticator, you can generate one-time passwords (OTPs) on your mobile device that can be used as the second factor in the authentication process on any website that supports MFA.The Protectimus Smart 2FA authenticator offers many advantages, including:
- Encrypted cloud backup;
- Ability to transfer tokens to a new phone;
- Ability to import tokens from Google Authenticator;
- PIN and biometric authentication protection (Touch ID and Face ID);
- Support for all OATH one-time password generation algorithms (HOTP, TOTP, and OCRA);
- Delivery of two-factor push notifications;
- Data signature function (Confirm What You See) to better control your operations with funds;
- 6 and 8 digit one-time passwords;
- Multiple language support: English, French, German, Spanish, Russian, and Ukrainian;
- Convenient distribution of OTP tokens by folders;
- Customization of tokens with different emojis and descriptions.
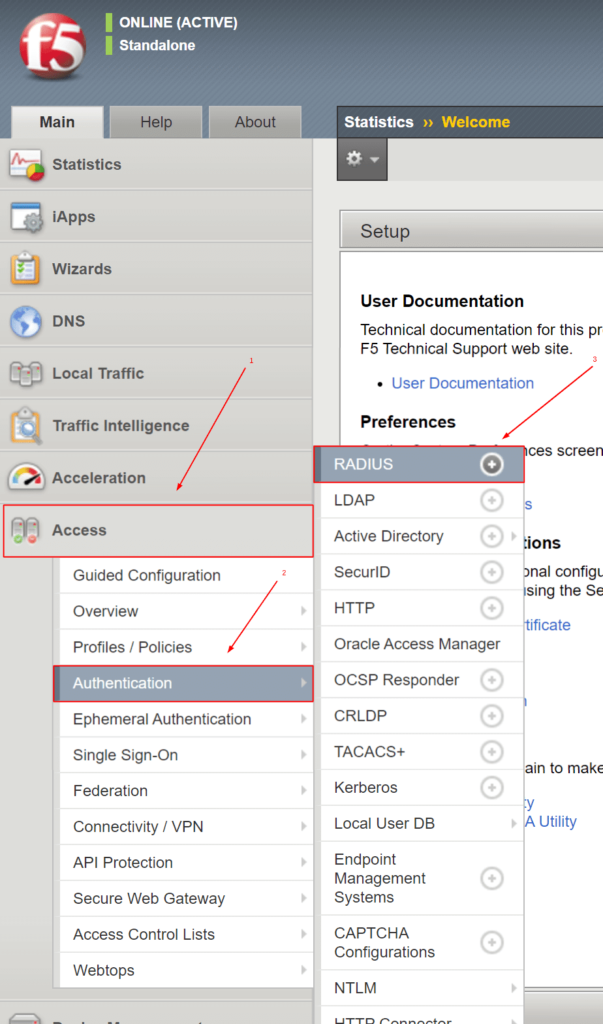
1. Getting Started With the Protectimus Smart 2FA Authenticator
- Download and install the Protectimus Smart OTP two-factor authentication app from the App Store or Google Play.
- You will see a welcome screen. Tap Continue.

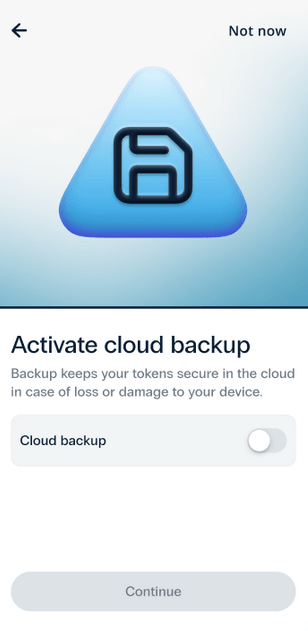
- On the next step, you will be asked to Activate Cloud Backup.
We strongly recommend using this feature to ensure that you do not lose your OTP tokens in case you lose or damage your phone, or accidentally delete the 2FA app. To activate cloud backup, select the option and press Continue.Please note! If you already have a cloud backup saved, all the tokens from your backup will be added to the 2FA app after you activate cloud backup at this stage.
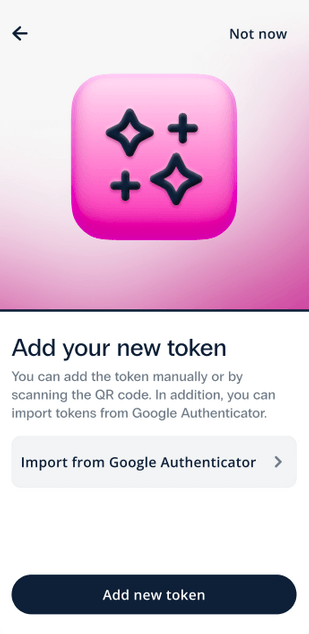
- Now you can add a new token or import your 2FA tokens from Google Authenticator.
For instructions on how to import tokens from Google Authenticator, please refer to the detailed guide here.
For instructions on how to add new tokens, please refer to the detailed guide here.
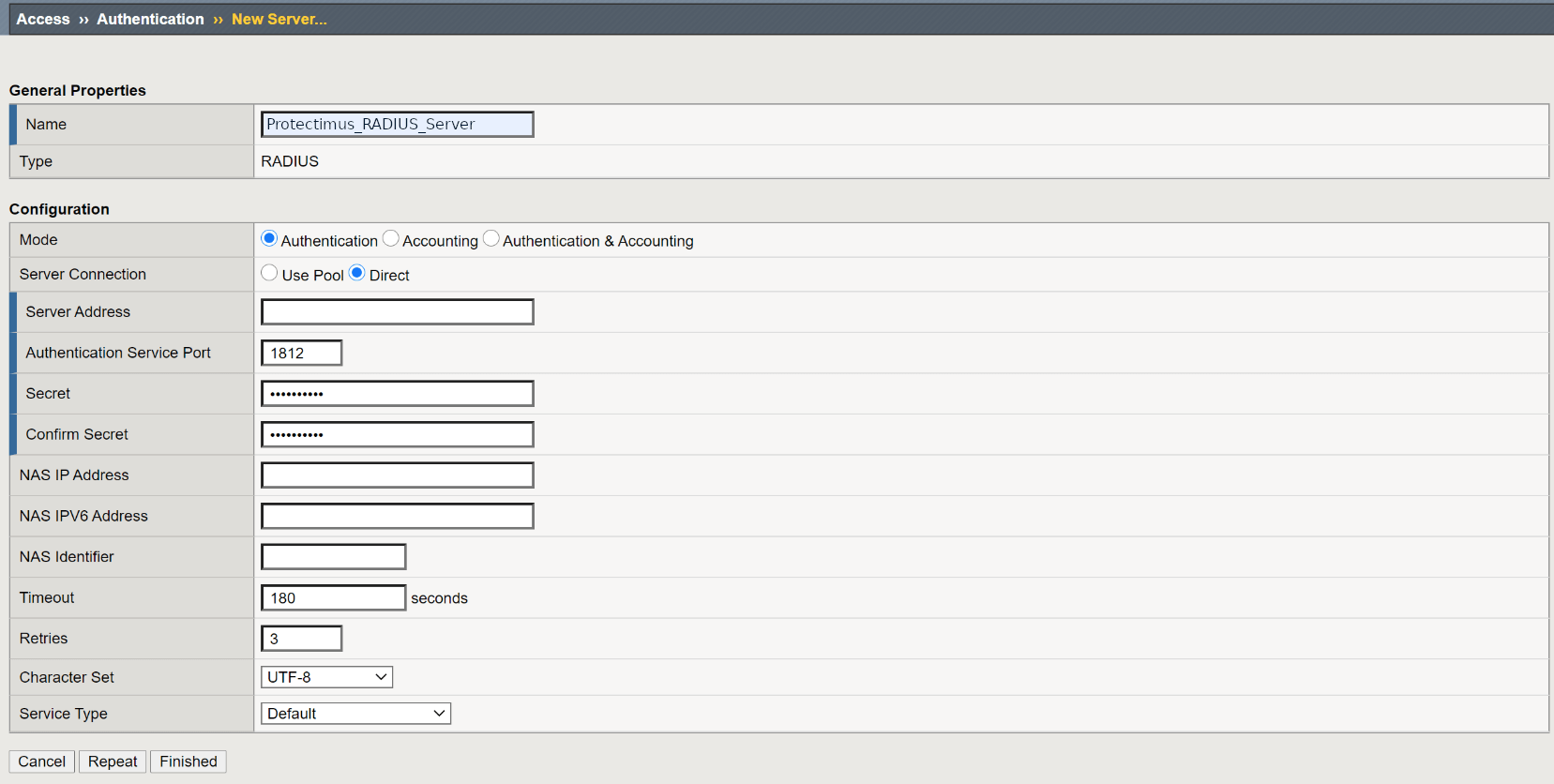
2. Adding Tokens
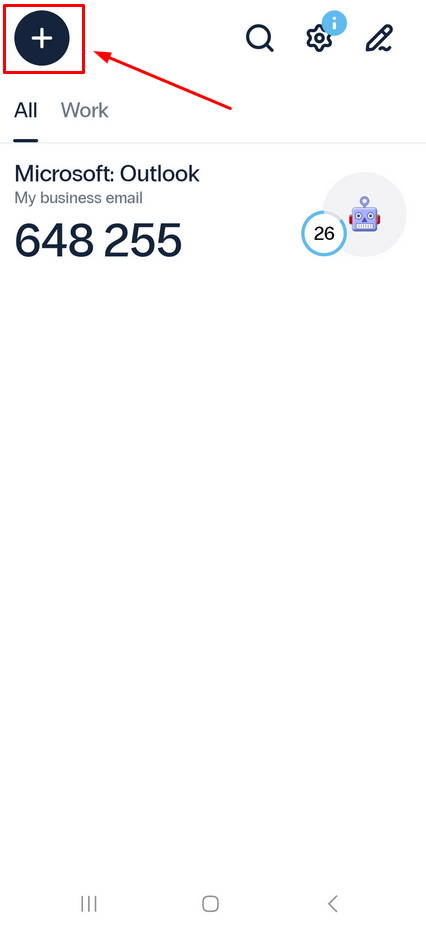
- To add a new token, open the Protectimus Smart OTP two-factor auth app and tap on the plus sign in the upper left corner.
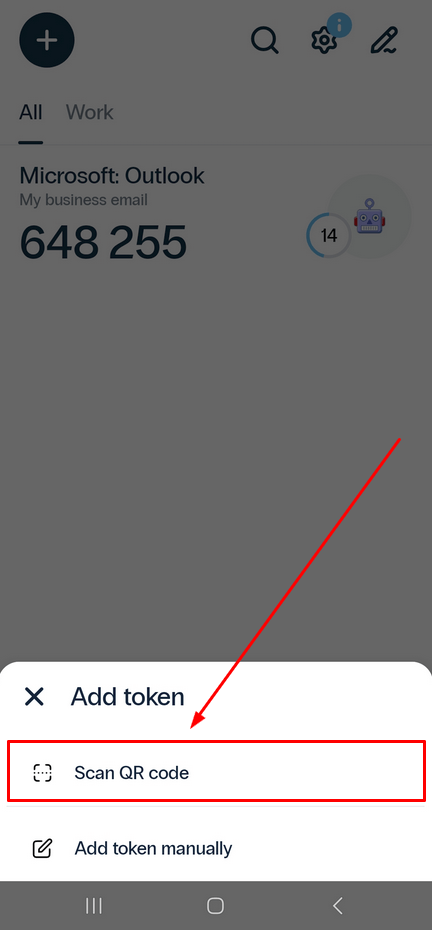
- You can choose to add the token by scanning a QR code or by entering the secret key manually.
If you choose to Scan QR code, simply point your smartphone’s camera at the code on the security settings page of the website you want to protect with two-factor authentication. The app will automatically scan the QR code and create a token.
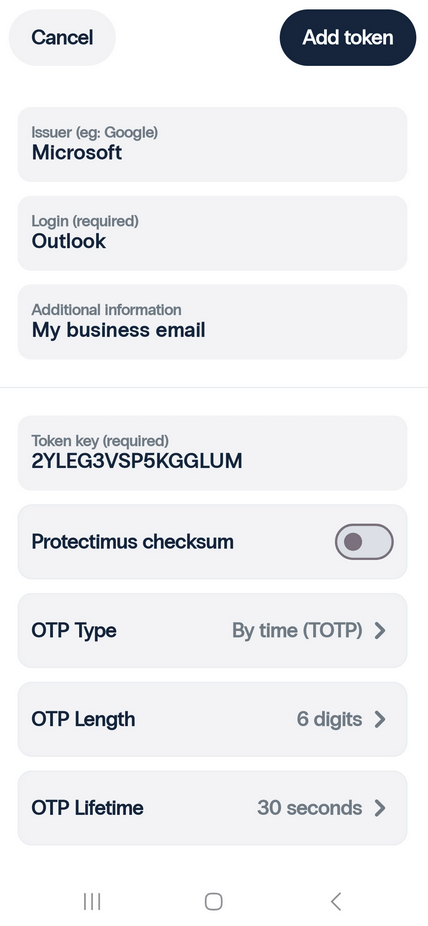
- If you choose to Add token manually, you’ll need to enter the token name (Login), the secret key (Token key), choose the OTP generation algorithm (OTP Type), the one-time passwords length, and lifetime. Then save the changes tapping the Add token button in the right upper corner.
Note that if you’re using a two-factor authentication system other than Protectimus, you should uncheck the Protectimus checksum checkbox.
3. Editing and Deleting Tokens
- To edit or delete a token, long-press on its name and choose the desired action. Alternatively, you can open the Edit Token menu by tapping the pen icon in the upper-right corner and selecting the token you want to modify.
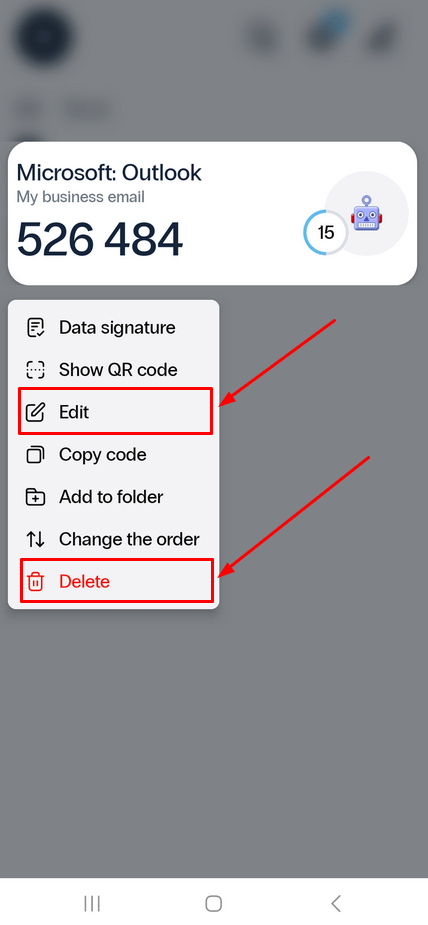
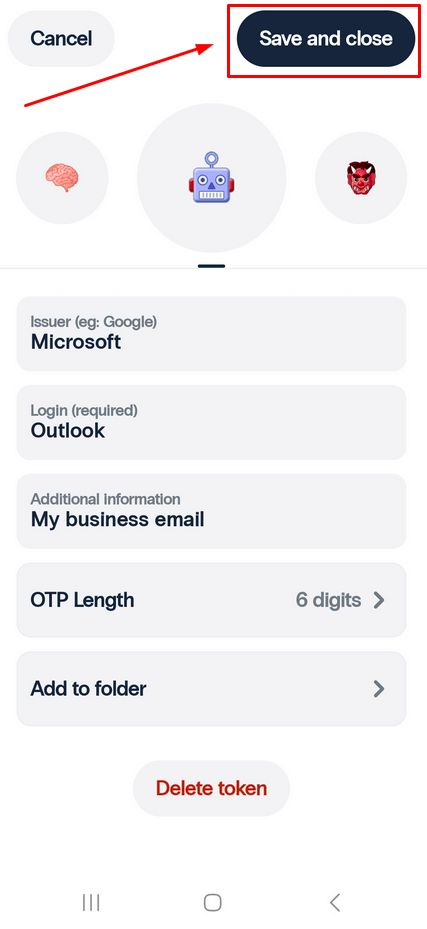
- Once you’re in the Edit Token menu, you can customize the token by:
- changing its emoji,
- setting the issuer,
- updating its name (Login),
- adding a description (Additional information),
- adjusting the OTP length,
- assigning it to a folder.
Once you’ve made your changes, click Save and close in the upper-right corner to confirm.
4. Grouping Tokens by Folders
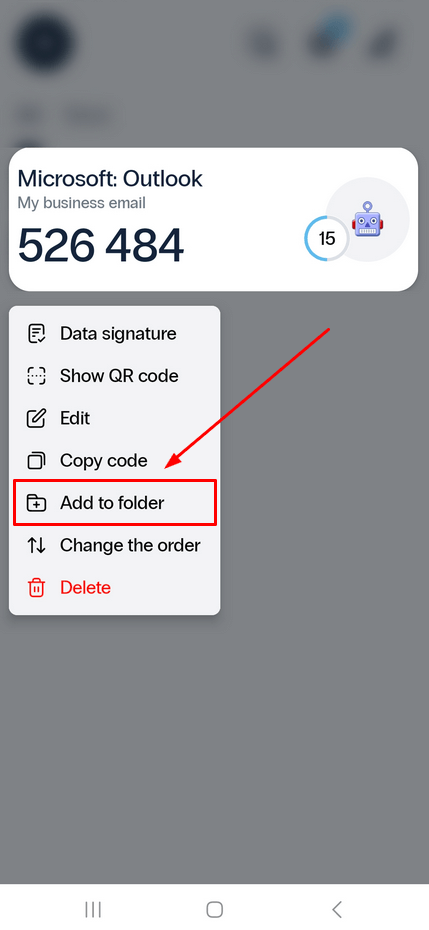
- To keep your tokens organized, you can group them into folders.
To add a token to a folder, simply long-press its name and select Add to folder.
- You’ll be taken to the folder settings menu, where you can either choose an existing folder or create a new one. If you want to create a new folder, click on the icon in the top right corner.
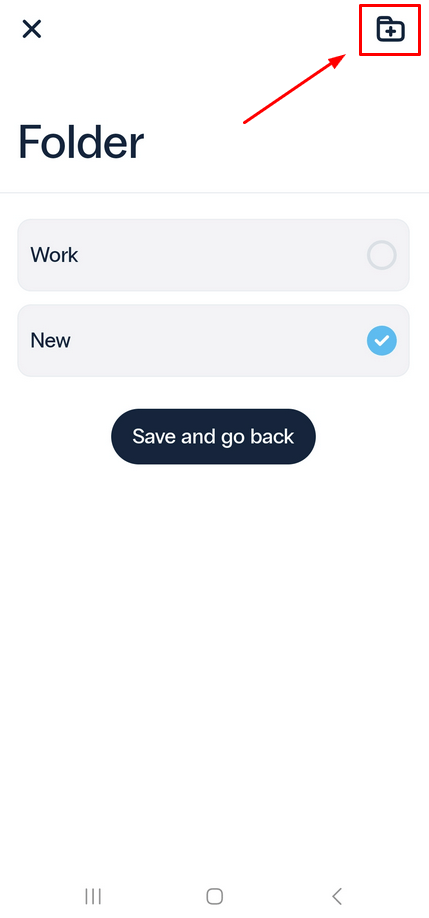
- To manage your folders, click on the gear icon in the upper right corner to go to the Settings page.
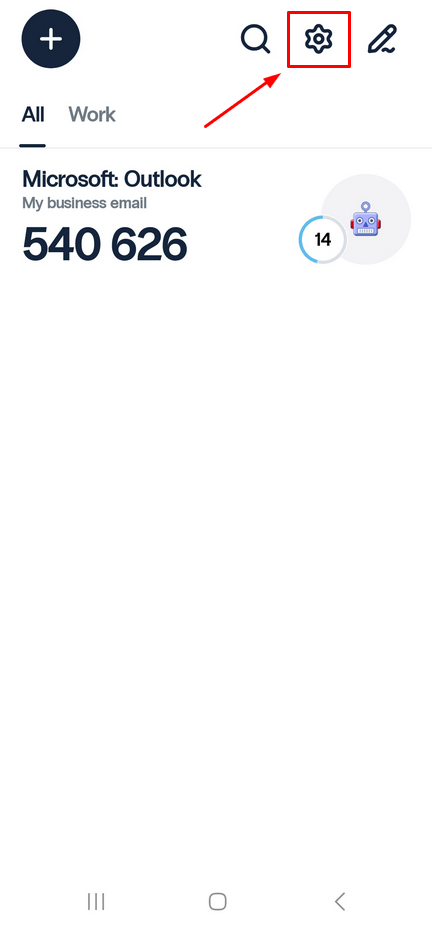
- Select Folder Settings.
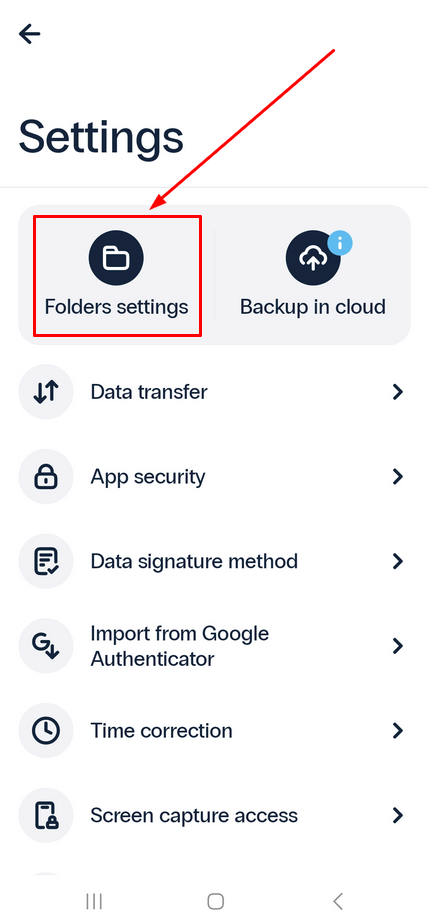
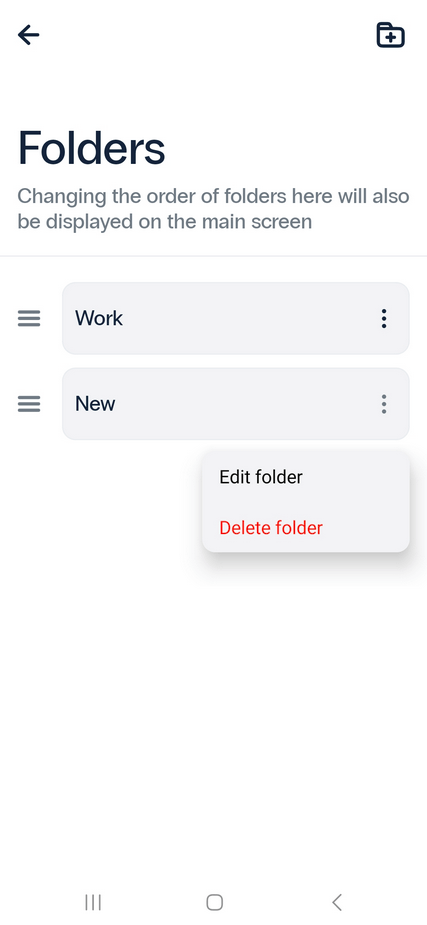
- From here, you can edit, delete, and create new folders, as well as edit tokens in any folder.
5. Changing the Order of Tokens
You can customize the order of your tokens to suit your needs. With this feature, you can quickly access your most frequently used tokens.- To do so, open the Edit Token menu by tapping the pen icon in the upper-right corner.
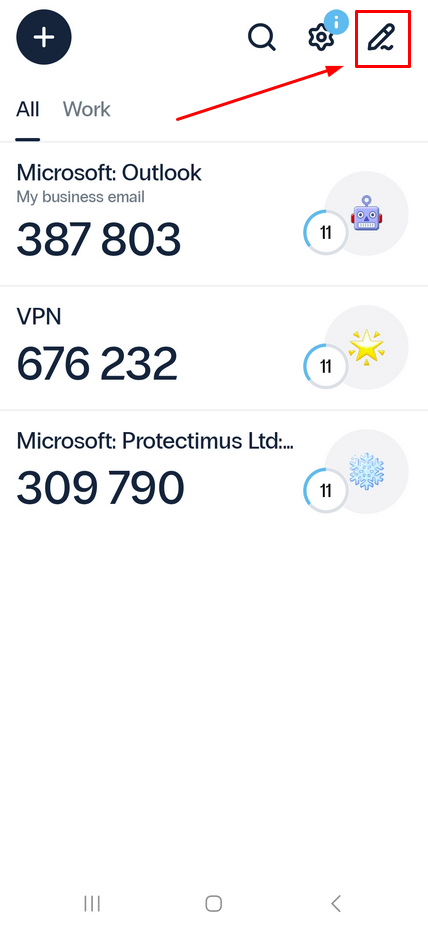
- From there, simply drag the tokens to rearrange them in the desired order. Save the changes by clicking on the checkmark in the upper right corner.
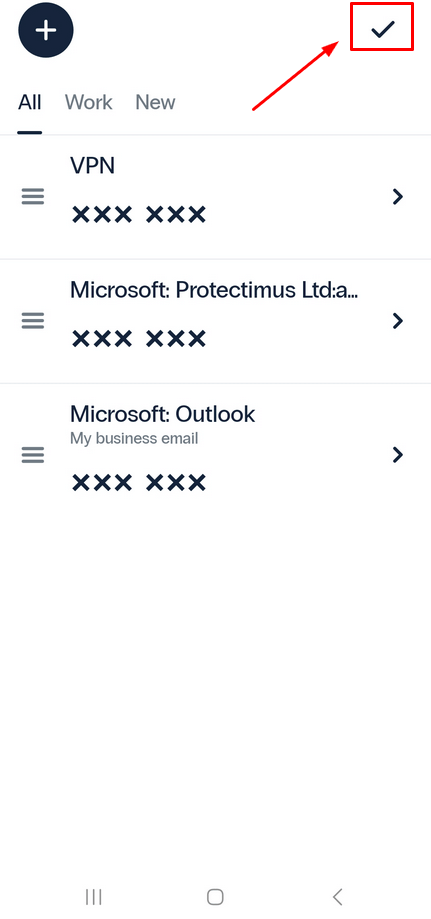
6. Cloud Backup
To safeguard your OTP tokens in case of device loss or accidental deletion of the 2FA app, we strongly recommend using the Cloud Backup feature. Additionally, we strongly advise protecting the backup file with a password for added security.To manage your backup files, simply navigate to the Backup page where you can activate, update, restore or delete your backups.
By utilizing this feature, you can ensure that your OTP tokens are always available and secure, even in unexpected circumstances.
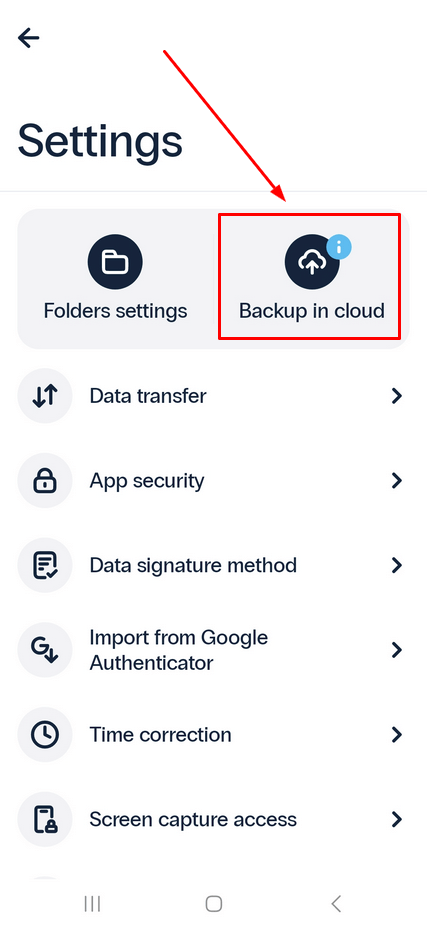
- Go to Settings.

- Tap Backup in cloud.
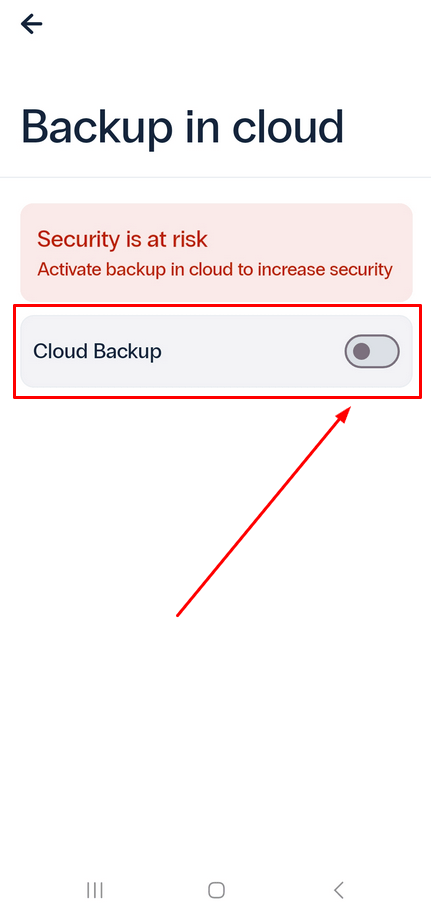
- If the backup function is not activated yet, enable it.
- If the backup function has been activated and you have made any changes, you can Restore the previous version or Update the backup file. Tap the Upload button to upload the latest changes to the cloud.
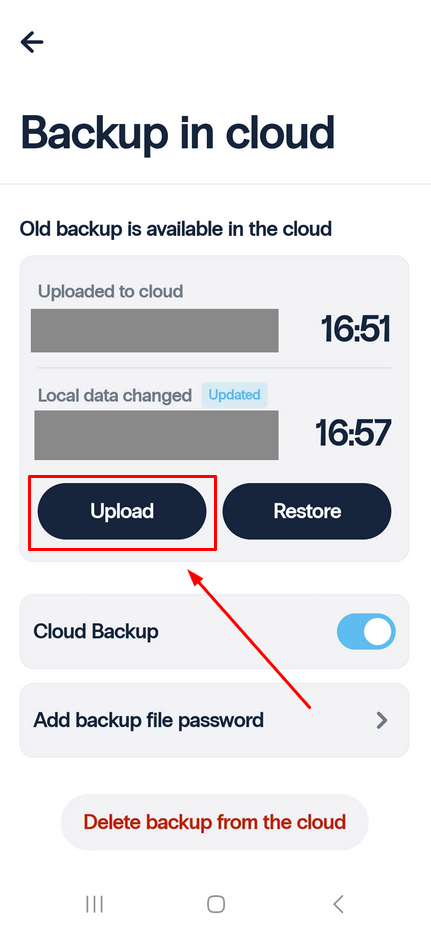
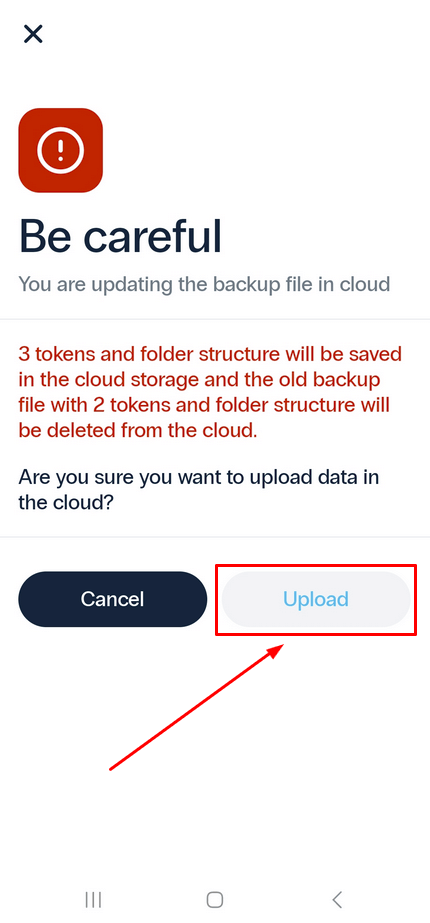
- You will see the allert message. If you are sure that you want to upload current OTP tokens in the cloud, tap Update. Please note that this will erase previous backups.
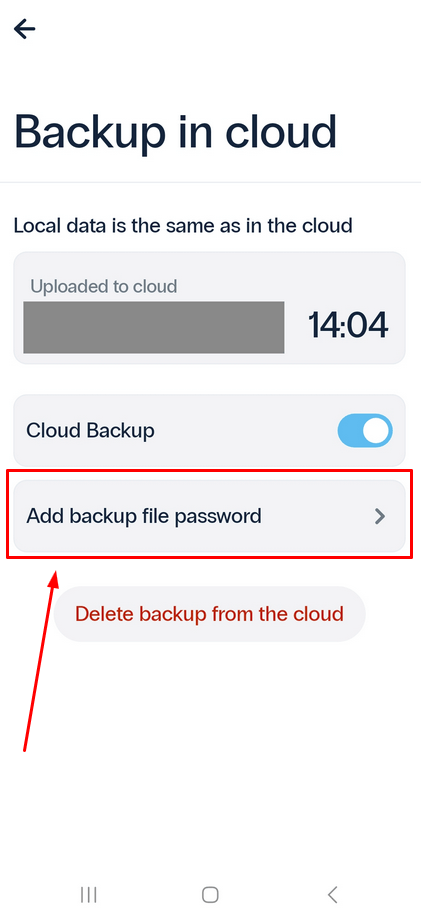
Please note! To secure you backup file, we recommend adding a password, use the Add backup file password button.
7. App Security (PIN and Biometric Authentication)
For optimal security, it is highly recommended that you safeguard access to the Protectimus Smart OTP two-factor authentication application with either a PIN or biometric authentication.To enable PIN or biometric authentication with fingerprint or face ID, follow these steps:
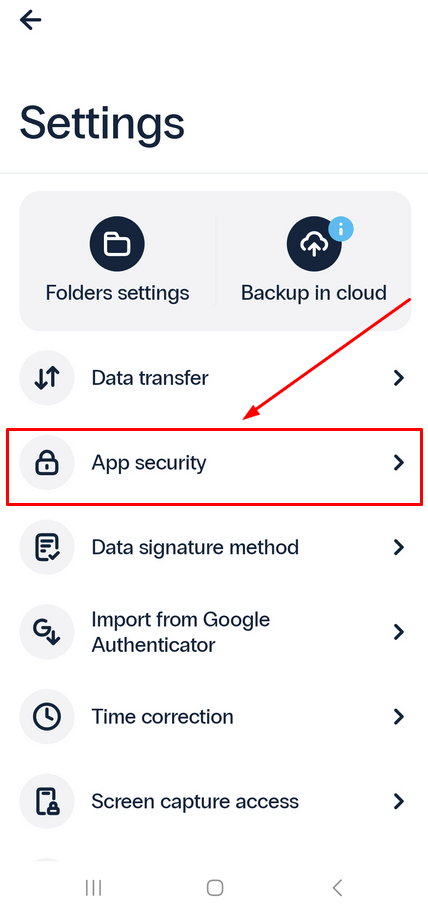
- Go to the Settings menu.

- Select App security.
- Create a unique PIN for the application.
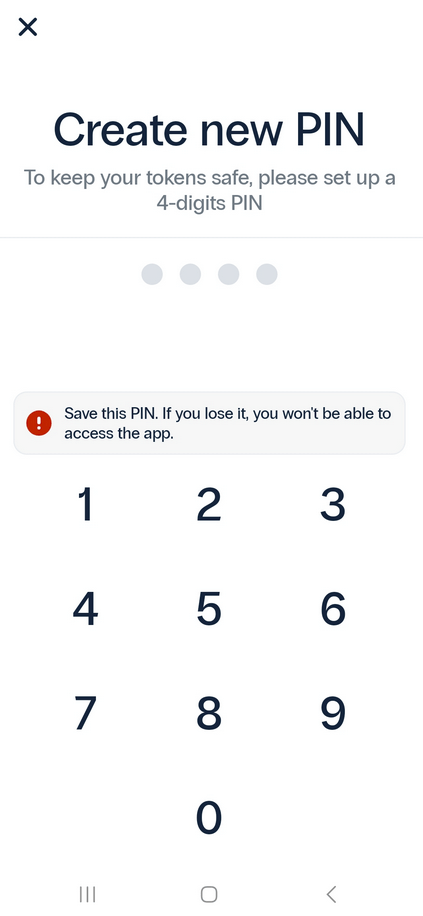
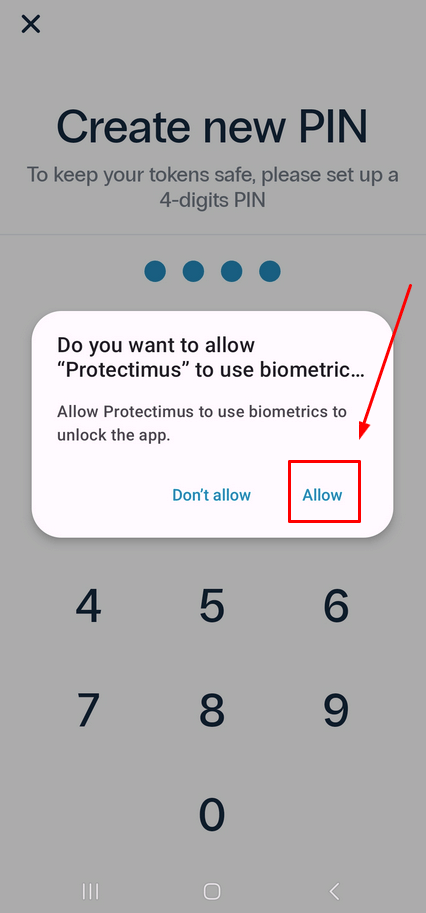
- The app will prompt you to allow biometric authentication for easier access.
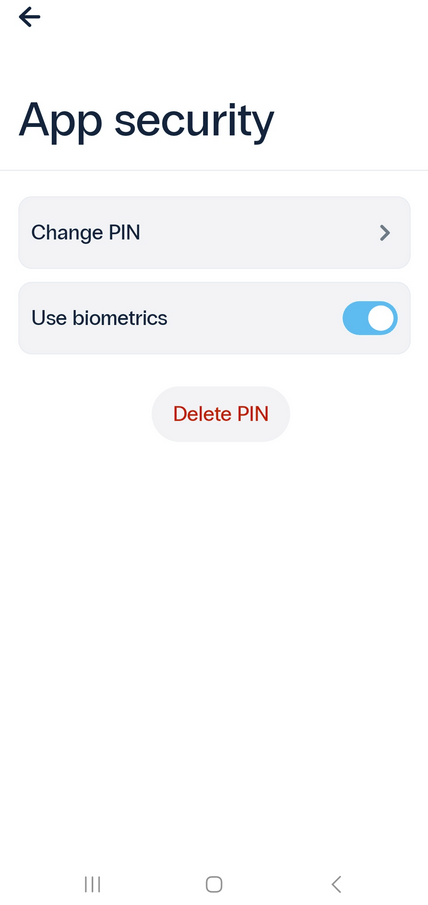
- Once both PIN and biometric protection are enabled, you can manage your PIN, and turn biometric authentication on or off from the App security page.
By taking these simple steps, you can ensure that your Protectimus Smart OTP two-factor authentication application is as secure as possible.
8. Transferring Tokens to a New Phone
Protectimus Smart OTP authenticator offers a convenient Data Transfer feature that enables you to effortlessly move your tokens from one phone to another or doenload and store the backup file in the place you like. With this feature, you can export your data into an encrypted file with password protection for added security.- To get started, simply navigate to the Settings menu.

- Tap on the Data transfer option.
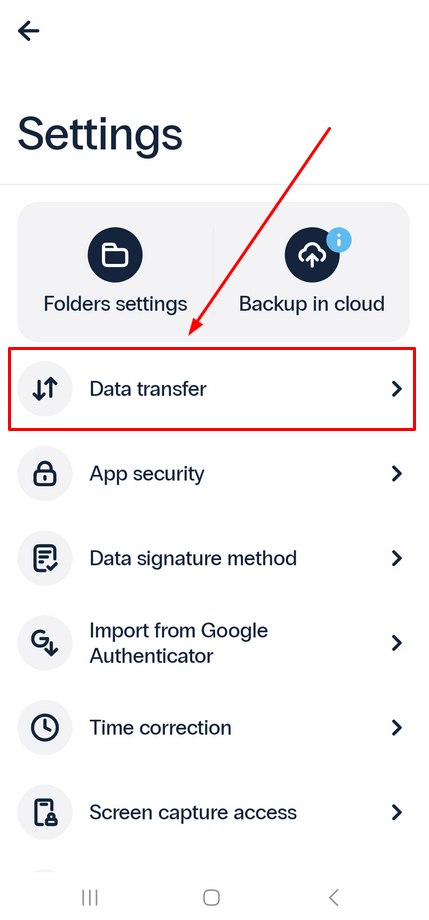
- If you want to transfer tokens from your current device to another, choose Export tokens. Alternatively, if you want to import saved data onto your device, select Import tokens.
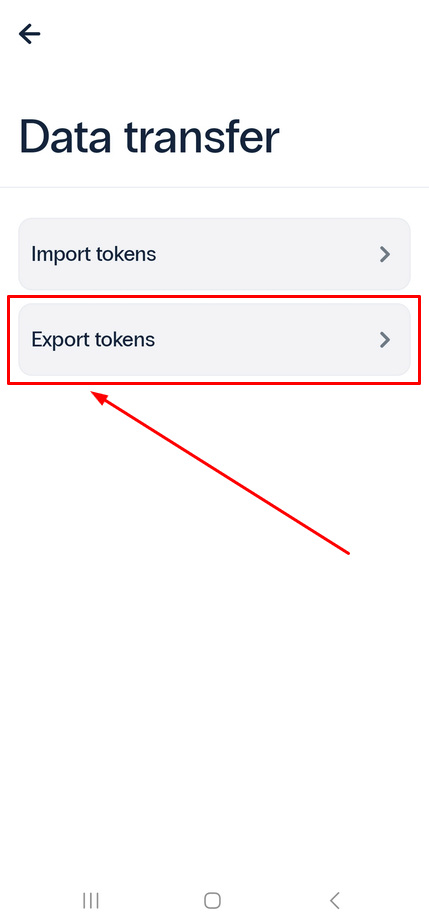
- If you choose to export tokens, create a strong password and click on Continue to generate the file containing all your data.
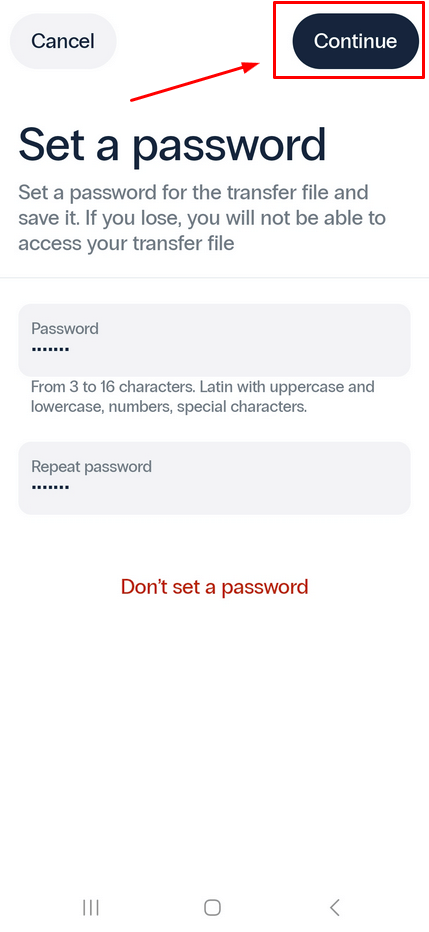
- Remember to save this file so you can import your tokens onto the new device later.
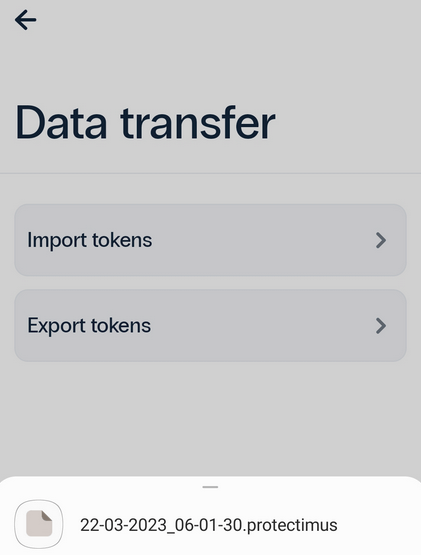
9. Importing from Google Authenticator
You can easily transfer your tokens from Google Authenticator 2FA app to the Protectimus Smart OTP.To get started, open your Google Authenticator application and:
- tap the menu button located at the top-right corner;
- select Transfer accounts;
- then choose Export accounts;
- select the tokens you wish to transfer to Protectimus Smart OTP;
- tap Next, and you will see a QR code, scan this QR code using the Protectimus Smart OTP app.
In the Protectimus Smart OTP app:
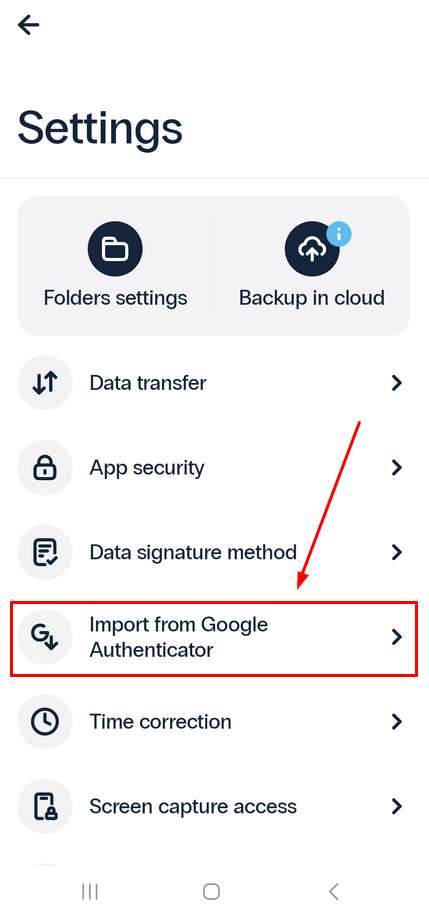
- Go to Settings.

- Select Import from Google Authenticator, scan the QR code generated by Google Authenticator and wait for the import process to complete.
10. Data Signature Method (CWYS)
Protectimus Data Signature, also known as CWYS (Confirm What You See), is a powerful tool that safeguards against phishing, data spoofing, man-in-the-middle attacks, and similar hacking techniques.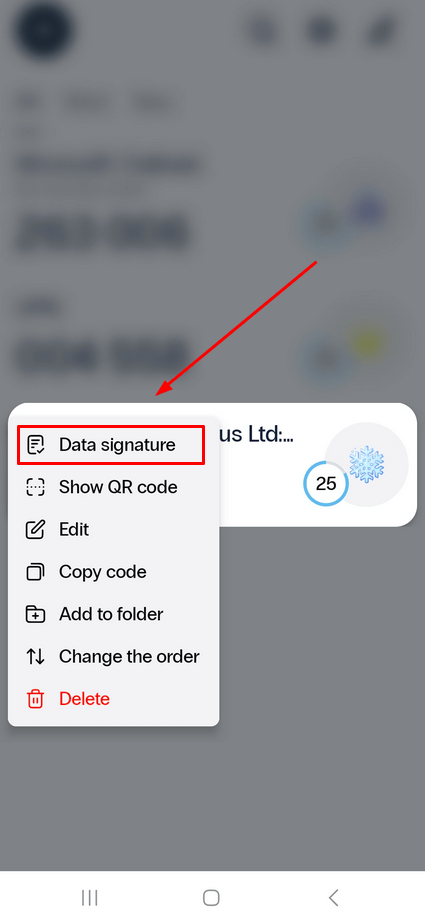
Based on the OCRA algorithm, Protectimus Data Signature allows users to verify key details of financial transactions before confirming them.
To use this feature, you will need to enter a challenge code into the app to generate a one-time password. You can enter the code manually or scan a QR code.
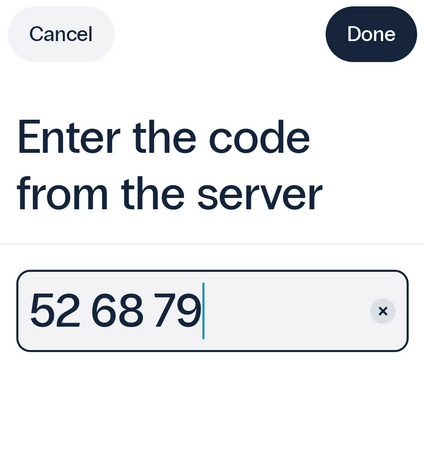
To set your preferred method for entering a challenge code:
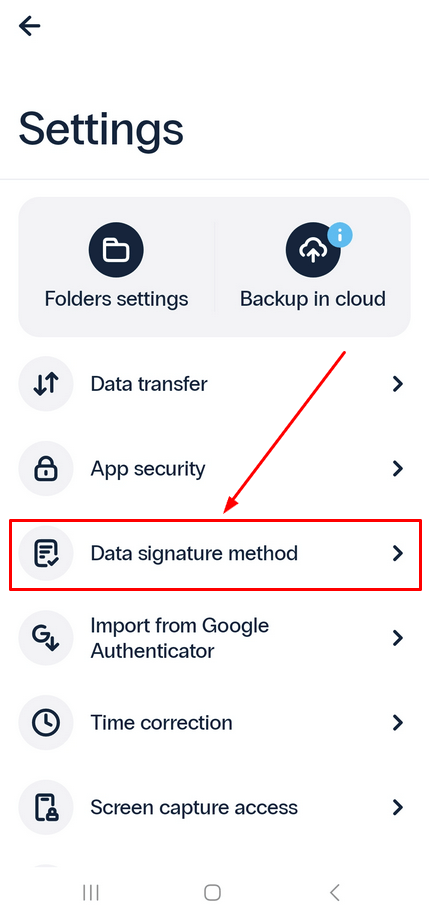
- Go to Settings.

- Select the Data Signature method.
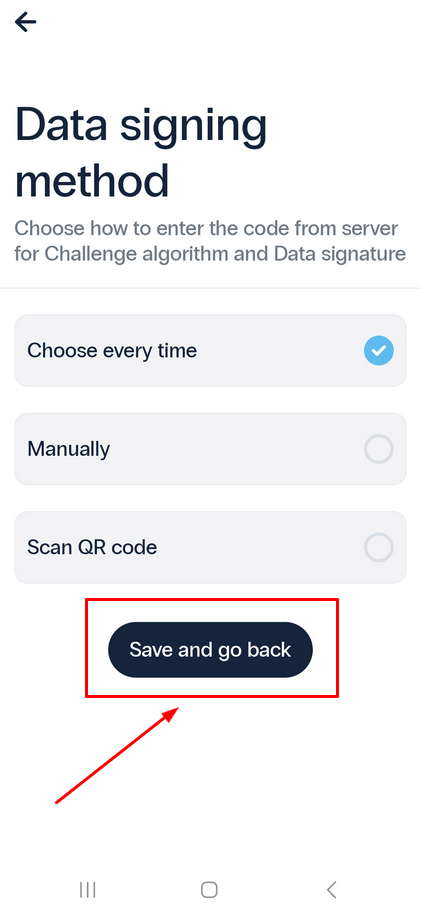
- Choose your desired option, and click Save and go back.
11. Push Tokens
Two-factor authentication app Protectimus Smart OTP offers push notifications as a convenient way to confirm transactions and streamline the login process for end-users, providing additional protection against transaction data replacement.This feature is available exclusively for services that use Protectimus 2FA solution as their two-factor authentication system backend.
To add, use, or delete push tokens, follow the steps outlined in the next paragraph.
Please note!
- You cannon receive push notification if your phone is offline.
- Push tokens cannot be edited, backed up, or transferred to another device.
11.1. How to Add Push Tokens
- Open the Protectimus Smart OTP MFA app and tap on the plus sign in the upper left corner.

- Choose to Scan QR code and scan the QR code on the service where you plan to use this push token.

- To proceed, save the public key to your device by tapping the Continue button.
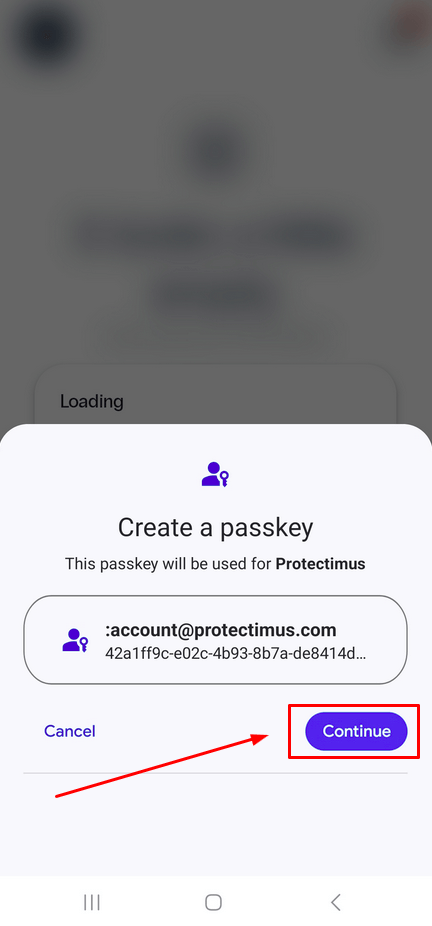
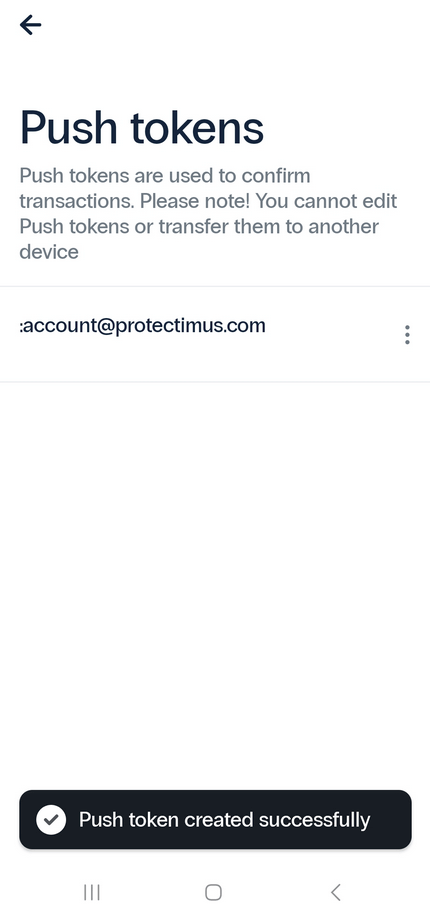
- You’re all set! The push token has been created, and you’ll receive a notification confirming its successful creation.
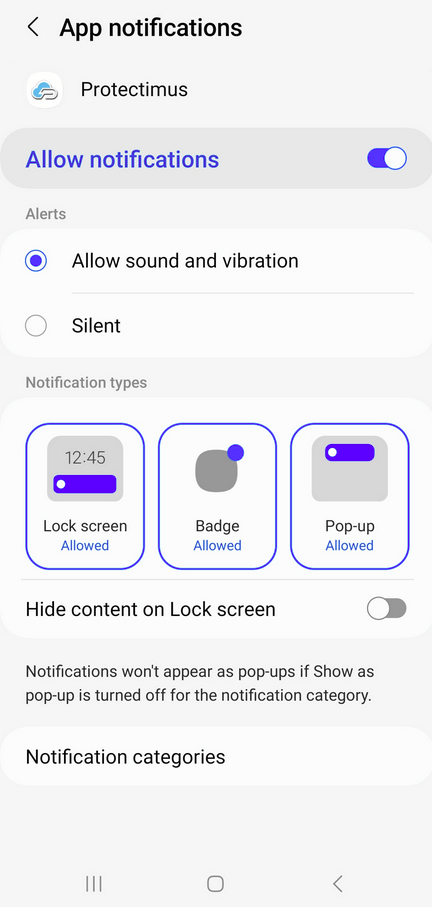
Important! To receive push notifications from the Protectimus Smart OTP 2FA app, you must enable notifications in your app settings. Please ensure that notifications from the Protectimus Smart OTP app are allowed.
11.2. How 2FA Push Notifications Work
This advanced two-factor authentication feature provides additional protection against data spoofing and transaction data replacement.Note! The device must be online to receive the push notification.
- When making a transaction or attempting to log in to a two-factor authentication-protected service, a push notification will be sent to your phone.
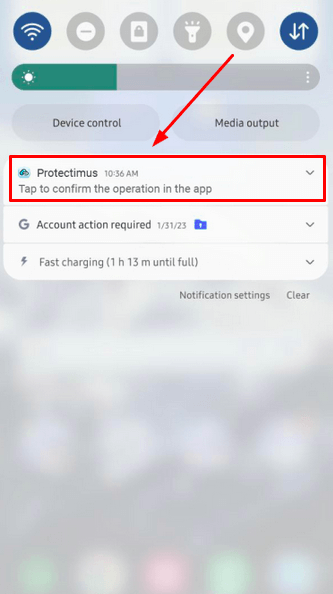
- You’ll need to open the app to view and confirm the details of the transaction.
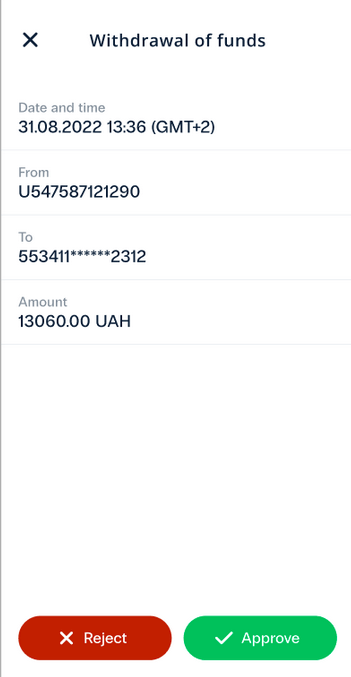
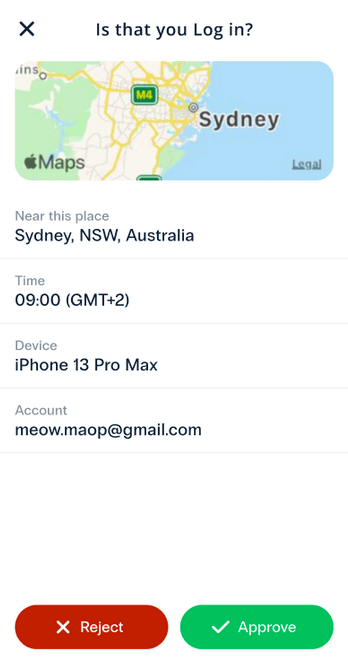
- Or to view and confirm the location of the login attempt.
11.3. How to Delete Push Tokens
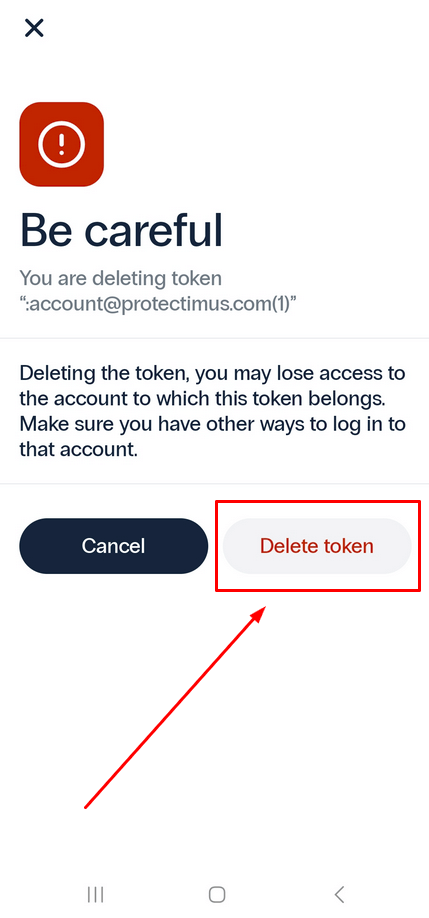
Please note! Please note that push tokens cannot be edited, backed up, or transferred to another device. Deleting the push token is irreversible, and there is no way to restore it. This means that you may lose access to the account associated with the token if it is deleted.
- To delete a push token, go to Settings.

- Go to Push tokens.
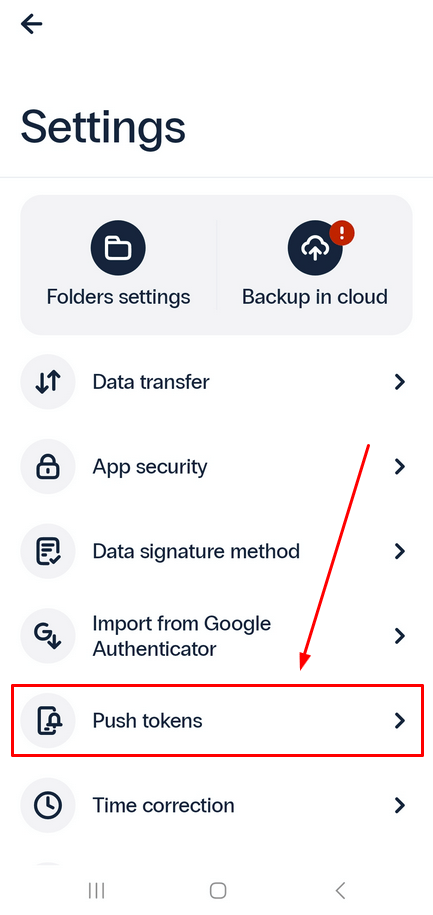
- Tap the three dots next to the token you wish to delete, and select Delete token.
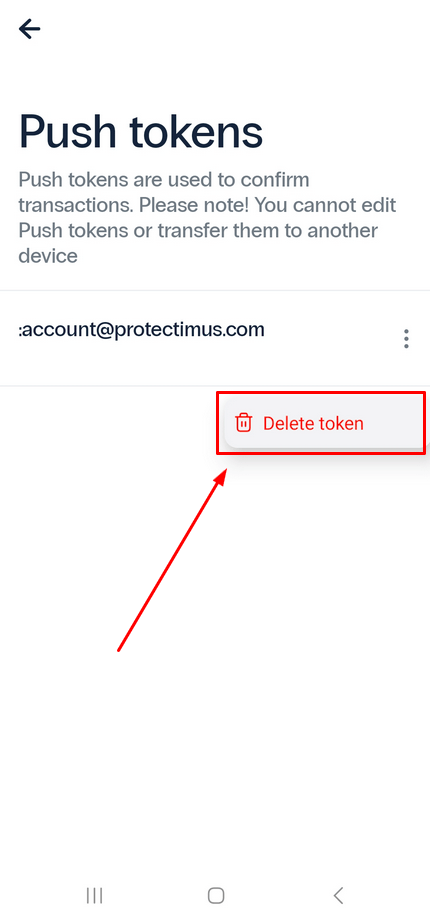
- A confirmation message will appear, and you should only proceed if you are certain that deleting the token will not result in the loss of access to the account protected by it.
12. Time Correction
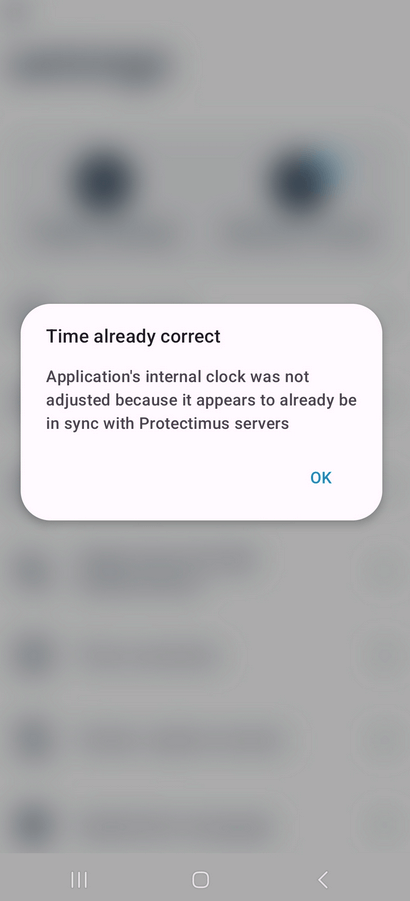
If you see the message “The one-time code is invalid” when attempting to enter a one-time password, it may be due to a time drift between your token and the two-factor authentication server. To resolve this issue, a time correction may be necessary.To synchronize your Protectimus Smart OTP app’s internal clock with Protectimus servers:
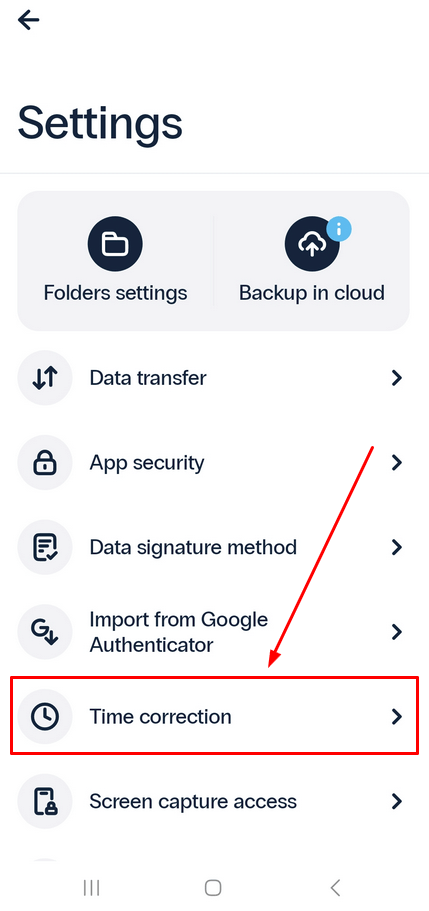
- Navigate to Settings.

- Select the Time correction option.
- If everything is in order, you will see a message confirming that the time is already correct.
13. Additional Settings
The Protectimus Smart OTP settings page provides additional options for customization, such as selecting your preferred language for the interface, enabling or disabling Screen Capture Access, and choosing between a dark or bright appearance to suit your preferences.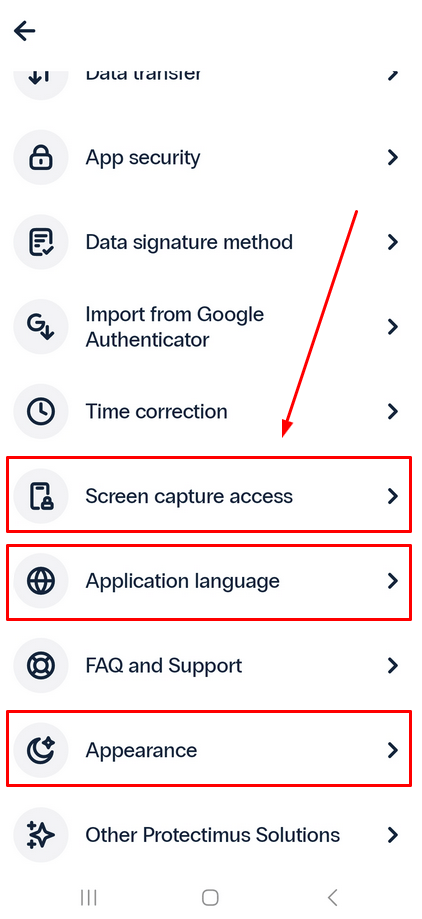
12.1. Application Language
Currently, the Protectimus Smart OTP authenticator is available in English, French, German, Spanish, Russian, and Ukrainian.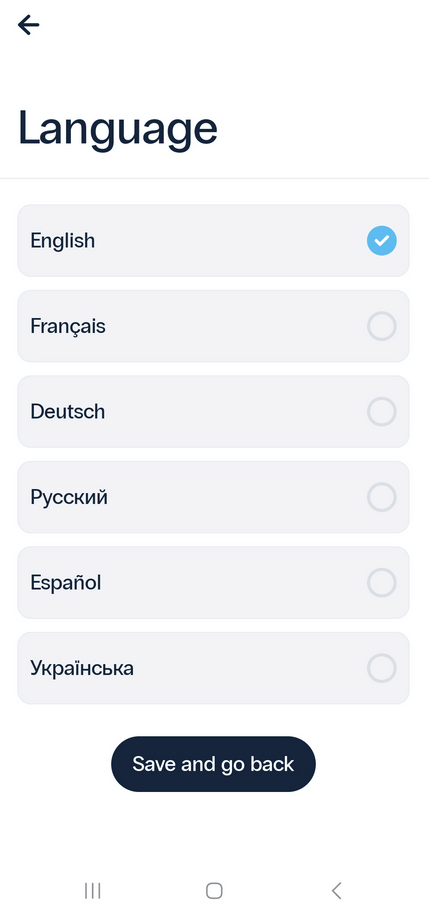
12.2. Screen Capture Access
To enhance your security, we advise against enabling screen capture access.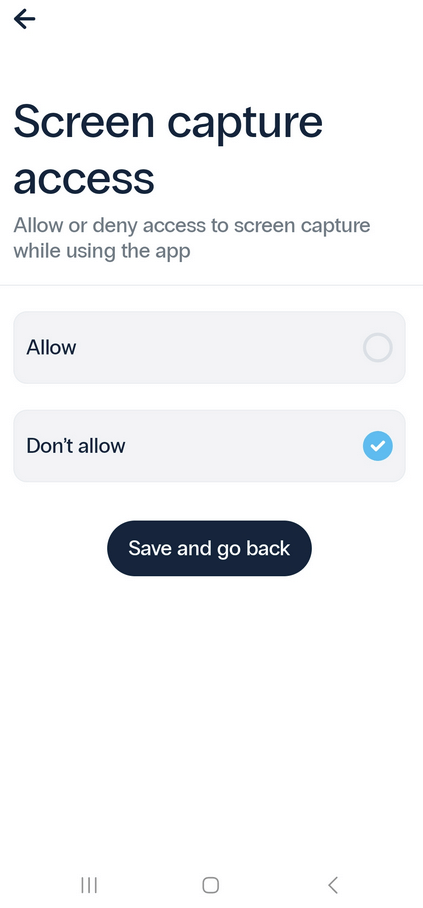
If you have any questions, please, contact Protectimus customer support service.